The Apache HTTP Server Project is a group of people working together to create and maintain an open-source, software-based HTTP server for modern operating systems such as UNIX and Windows. This technology is considered among the most widely used web servers on the internet.
A Server-Side Request Forgery (SSRF) vulnerability (CVE-2021-40438) has been identified in Apache HTTP Server versions 2.4.48 and older. The vulnerability exists because the mod_proxy module in Apache HTTP Server does not properly validate user-supplied information. A remote attacker can fool the web server into initiating queries to arbitrary systems by sending a specially crafted HTTP request with a selected uri-path.
If this vulnerability is successfully exploited, a remote attacker can obtain access to sensitive data on the local network or send malicious requests to other services from the vulnerable system.
For a server to be vulnerable, the mod_ proxy module must be activated, therefore attackers must first discover servers that meet this criterion to exploit the flaw.
mod_proxy is used to implement a proxy/gateway for Apache HTTP Server, supporting several popular protocols as well as different load balancing algorithms. In simple terms, it can be used to redirect traffic from Apache to a proxy server.
If mod_proxy is enabled and a proxy server is running at the backend, an attacker can append ‘UNIX’ into the URL, and since the unpatched version of the code checks everywhere for ‘UNIX:’, it can be appended as a parameter and will trigger the UDS (Unix Domain Socket) code path.
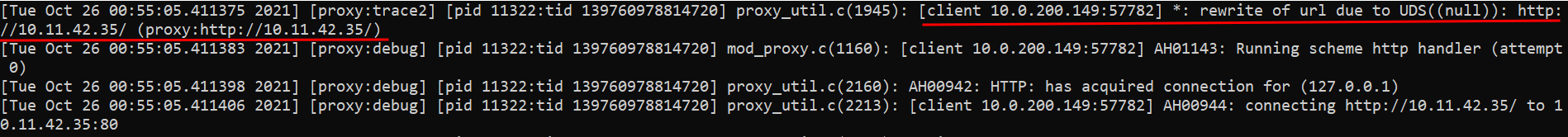 Image Source: Qualys
Image Source: Qualys
This allows an attacker to append many A’s (7701 to be precise) into the GET request and trigger the UDS to redirect the Apache server to a URL of the attacker’s choosing.
The vulnerable configuration for mod_proxy might look as follows:
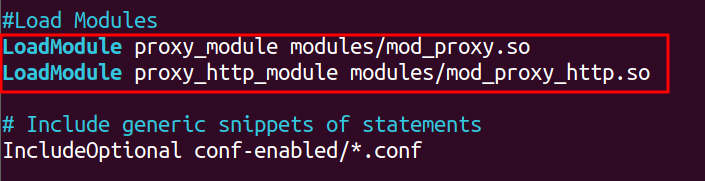 Image Source: Qualys
Image Source: Qualys
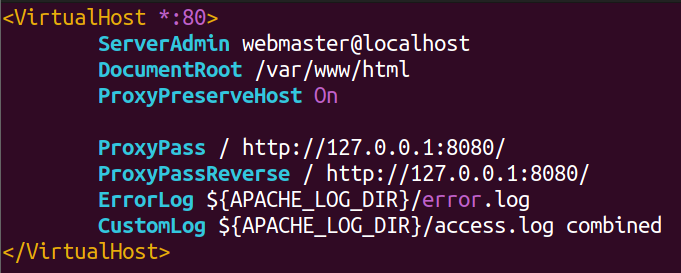 Image Source: Qualys
Image Source: Qualys
What is SSRF?
Server-side request forgery is a web– security flaw that allows an attacker to force a server-side application to send HTTP requests to any domain the attacker chooses.
The attacker may cause the server to connect to internal-only services within the organization’s architecture in a conventional SSRF attack. They may also be able to force the server to connect to arbitrary external systems, exposing sensitive data such as authorization credentials.
At Qualys Labs, we have tried to recreate the issue and tested it on vulnerable Apache versions, successfully.
Output with mod_proxy disabled:
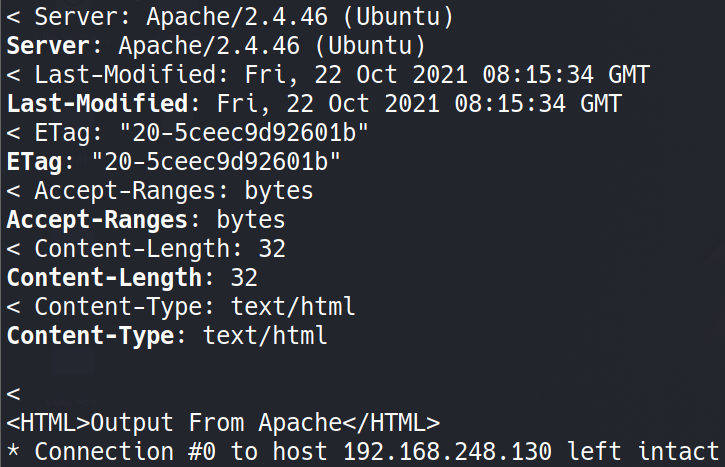 Image Source: Qualys
Image Source: Qualys
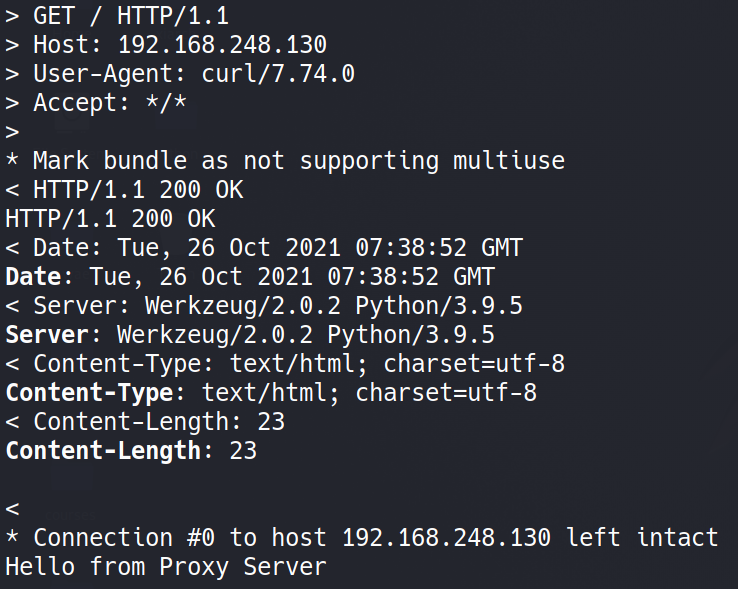 Image Source: Qualys
Image Source: Qualys
Output with SSRF payload:
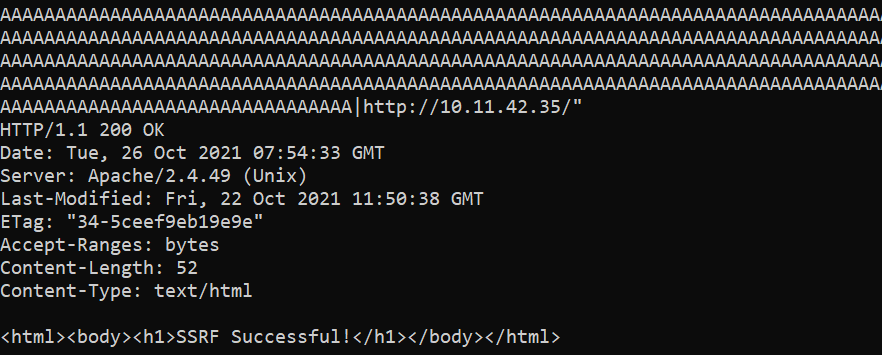 Image Source: Qualys
Image Source: Qualys
Affected versions
Apache HTTP Server 2.4.48 and older versions are affected by this vulnerability.
Mitigation
Customers are advised to update to Apache HTTP Server 2.4.49 or later. For more information, refer to Apache Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 87468 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://httpd.apache.org/security/vulnerabilities_24.html
https://www.cybersecurity-help.cz/vulnerabilities/56678/
https://portswigger.net/daily-swig/developers-fix-multitude-of-vulnerabilities-in-apache-http-server
https://www.fastly.com/blog/apache-redux-preventing-server-side-request-forgery-via-cve-2021-40438