Palo Alto Networks (PAN) released an update addressing the vulnerability CVE-2021-3064. This vulnerability was discovered and disclosed by Randori. This vulnerability affects PAN firewalls that use the GlobalProtect Portal VPN. This VPN allows for unauthenticated remote code execution on susceptible product installations.
The zero-day vulnerability has a severity rating of 9.8. The vulnerability chain has a method for bypassing an external web server (HTTP smuggling) and a stack-based buffer overflow. When parsing user-supplied information into a fixed-length region on the stack, CVE-2021-3064 causes a buffer overflow. Without using an HTTP smuggling strategy, the problematic code is not reachable from the outside. When these vulnerabilities are exploited simultaneously, remote code execution is possible with the privileges of the affected component on the firewall device. The smuggling capability was not assigned a CVE identifier since the impacted vendor does not consider it a security border.
Here is the PoC shared by Randori:
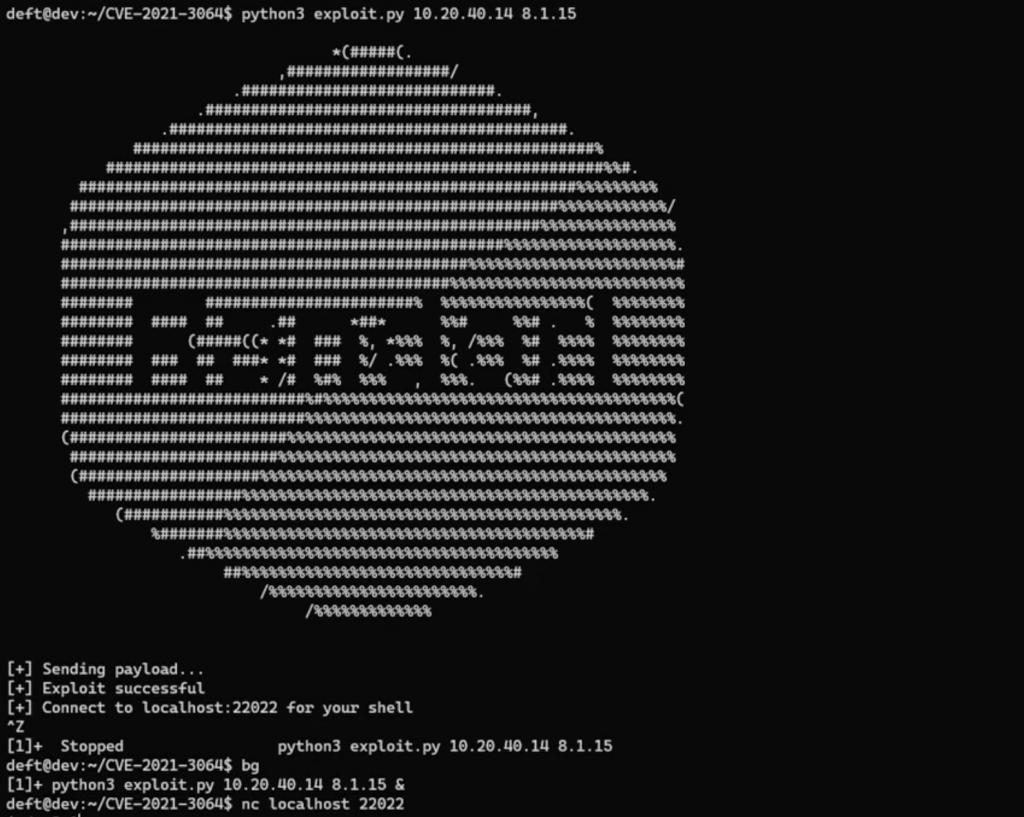 Image source: Randori
Image source: Randori
Affected versions
The CVE-2021-42321 security issue affects PAN-OS 8.1.x versions earlier than PAN-OS 8.1.17.
Mitigation
Customers are advised to refer to the Palo Alto Networks Security Advisory for information on patching this vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 730255 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://www.randori.com/blog/cve-2021-3064/
https://security.paloaltonetworks.com/CVE-2021-3064
https://bug.cyberkendra.com/2021/11/10/zero-day-disclosure-pan-globalprotect-cve-2021-3064/
https://www.zdnet.com/article/palo-alto-networks-patches-zero-day-affecting-firewalls-using-globalprotect-portal-vpn/