Attackers are actively exploiting a zero-day vulnerability in Windows Installer. The vulnerability was found after a Microsoft patch for another security weakness failed to adequately repair the initial and unrelated bug.
A security researcher found this Windows Installer Elevation of Privilege vulnerability termed as CVE-2021-41379. The vulnerability allows threat actors with limited access to a compromised device to elevate their privileges that would help them spread laterally within a network.
Bypass to patched vulnerability released by security researchers
With the November Patch Tuesday release, the CVE-2021-41379 vulnerability in Windows Installer was expected to be patched.
Abdelhamid Naceri, a security researcher, discovered a bypass to the patch as well as a more serious new zero-day privilege escalation issue after examining Microsoft’s update. Yesterday, Naceri published a successful proof-of-concept exploit for the new zero-day on GitHub, claiming that it works on all supported Windows versions. When authenticated into a Windows workstation with Edge installed, the POC, named InstallerFileTakeOver, allows an attacker to get complete control of the system by popping a SYSTEM shell.
Researchers from Cisco Talos Security Intelligence and Research Group, as well as others, confirmed that the proof-of-concept can be replicated and provided evidence that threat actors were already exploiting the flaw.
At Qualys Labs, we have tried to recreate the issue and tested it on Windows 10 pro version 21H1 and Windows 10 Version 20H2.
Windows 10 pro version 21H1
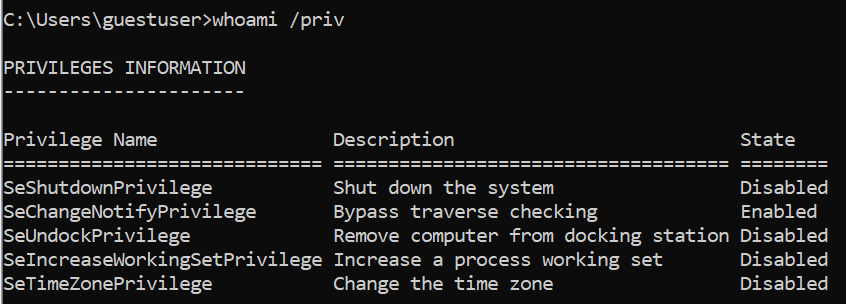 Image Source: Qualys
Image Source: Qualys
Image Source: Qualys
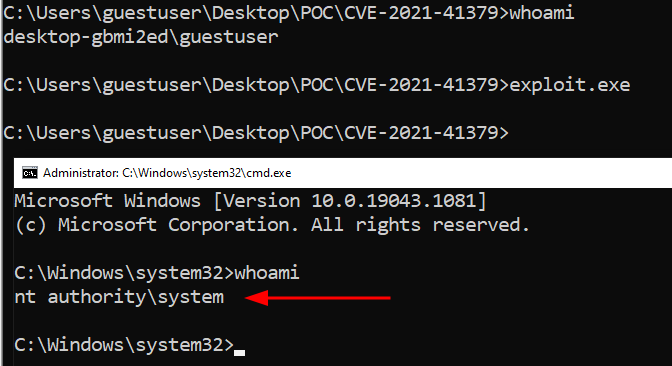
Image Source: Qualys
Affected versions
The privilege escalation vulnerability affects all supported versions of Windows, from Windows 10, Windows 11 to Windows Server 2022.
Mitigation
Microsoft has not released patches that remediate the vulnerability. Customers are advised to contact Microsoft regarding official updates or workarounds.
Qualys Detection
Qualys customers can scan their devices with QID 91840 to detect vulnerable assets.
Note: QID 91841 deprecated as QID 91840 is already present. The QID 91841 is retired on December 06, 2021.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://threatpost.com/attackers-target-windows-installer-bug/176558/
https://www.techtarget.com/searchsecurity/news/252509959/Researcher-drops-instant-admin-Windows-zero-day-bug
https://www.bleepingcomputer.com/news/microsoft/new-windows-zero-day-with-public-exploit-lets-you-become-an-admin/