Malicious actors are actively exploiting a recently patched critical vulnerability in Zoho’s Desktop Central and Desktop Central MSP products. This is the third time in the last four months that a security vulnerability in one of its products has been exploited in the wild.
Tracked as CVE-2021-44515, this is an authentication bypass vulnerability in ManageEngine Desktop Central that could result in remote code execution.
Zoho ManageEngine Desktop Central is a desktop and mobile device management software. Administrators can manage servers, laptops, desktops, cellphones, and tablets from one place with this tool.
Detecting the flaw
In the security advisory, Zoho has mentioned the way to detect the vulnerability in Desktop Central and Desktop Central MSP versions using their Exploit Detection Tool. Customers can download the tool and follow the given steps to detect the vulnerability in their tool:
- Extract the tool to \ManageEngine\UEMS_CentralServer\bin folder or \ManageEngine\DesktopCentral_Server\bin folder, whichever is applicable for you.
- Open a command prompt with admin privilege and navigate to one of the following locations:
\ManageEngine\UEMS_CentralServer\bin or \ManageEngine\DesktopCentral_Server\bin. - Run the command RCEScan.bat
- As shown in the screenshots below, if your installation is affected, you will see the error message “Exploit Detected”. If your installation is safe, you will see the message “No Exploit Detected”.
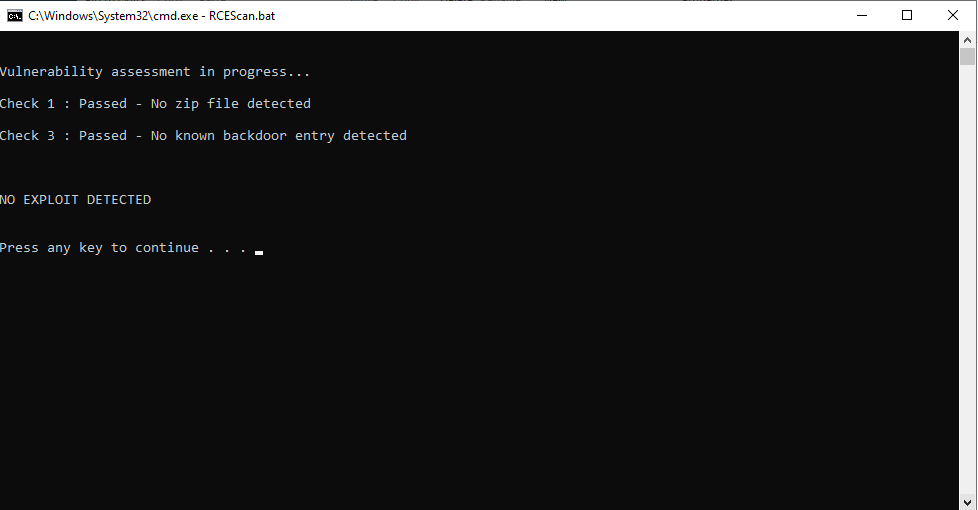 Image source: Zoho security advisory
Image source: Zoho security advisory
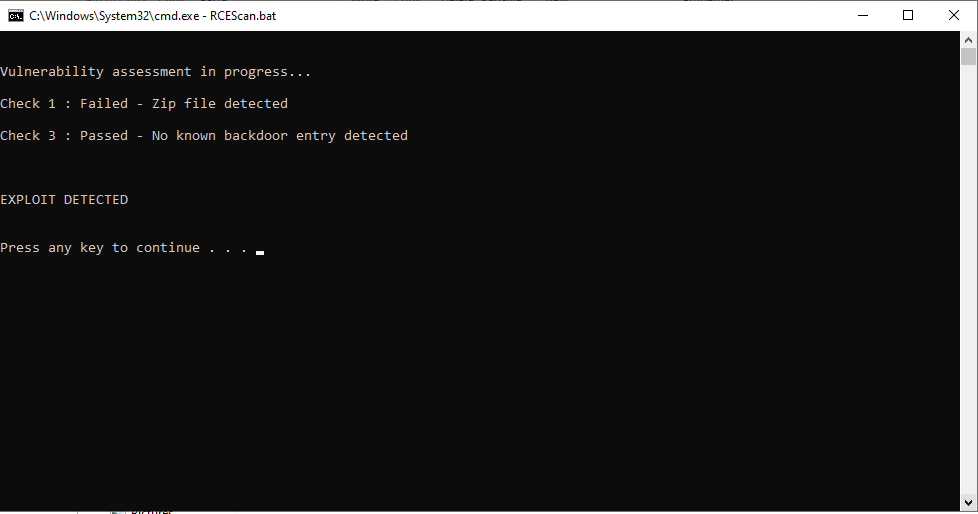 Image source: Zoho security advisory
Image source: Zoho security advisory
CVE-2021-44515 joins CVE-2021-44077 and CVE-2021-40539 as prior vulnerabilities that have been used to hack critical infrastructure companies’ networks around the world.
Affected versions
Following versions of Zoho ManageEngine Desktop Central and Desktop Central MSP are prone to this vulnerability.
- For Enterprise:
- Builds 10.1.2127.17 and earlier and builds 10.1.2128.0 to 10.1.2137.2,
- For MSP:
- Builds 10.1.2127.17 and earlier and builds 10.1.2128.0 to 10.1.2137.2
Mitigation
Here are the upgrades released by Zoho:
- For Enterprise:
- For builds 10.1.2127.17 and earlier, upgrade to 10.1.2127.18
- For builds 10.1.2128.0 to 10.1.2137.2, upgrade to 10.1.2137.3
- For MSP:
- For builds 10.1.2127.17 and earlier, upgrade to 10.1.2127.18
- For builds 10.1.2128.0 to 10.1.2137.2, upgrade to 10.1.2137.3
Refer to the following advisories for more information:
Qualys Detection
Qualys customers can scan their devices with QID 376138 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://therecord.media/zoho-warns-of-new-zero-day-vulnerability-exploited-in-attacks/
https://thehackernews.com/2021/12/warning-yet-another-zoho-manageengine.html
https://www.manageengine.com/desktop-management-msp/cve-2021-44515-security-advisory.html
https://www.bleepingcomputer.com/news/security/zoho-patch-new-manageengine-bug-exploited-in-attacks-asap/
https://www.manageengine.com/products/desktop-central/cve-2021-44515-authentication-bypass-filter-configuration.html