Linux has been exploited by a highly severe vulnerability (CVE-2022-0847) that is being called ‘Dirty Pipe’. This vulnerability can allow local users to gain root privileges through publicly available exploits and is considered one of the most significant Linux security vulnerabilities that have been discovered since 2016 when another high-severity and easy-to-exploit Linux bug (dubbed Dirty Cow) was discovered while being exploited to hack a researcher’s server. It allows a non-privileged user to inject and overwrite data in read-only files, including SUID processes that execute as root.
The vulnerability was discovered while a researcher for website builder CM4all was investigating a sequence of corrupted files that kept arriving on a customer’s Linux machine. This flaw is particularly concerning for web hosting companies that provide Linux shell access, as well as educational institutes that often provide shell access to multi-user Linux systems.
It’s been a difficult year for Linux, with a slew of high-profile privilege-escalation flaws exposed. The Linux iSCSI subsystem has privilege elevation vulnerabilities, as does another kernel flaw, the Extended Berkeley Packet Filter (eBPF), and Polkit’s pkexec component.
At Qualys, we have recreated the issue successfully on Linux 5.10.0.
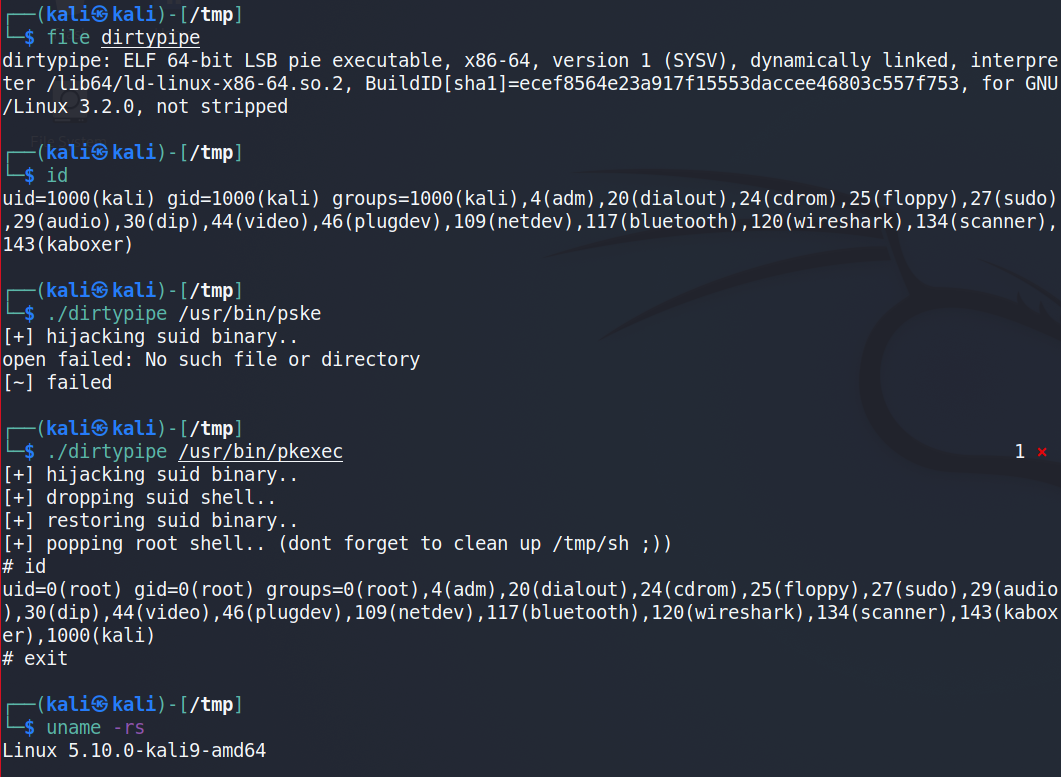
Image Source: Qualys
Affected versions
The vulnerability affects all the Linux kernel versions 5.8 and the versions prior to 5.17.
Mitigation
The vulnerability has been fixed in Linux kernels 5.16.11, 5.15.25, and 5.10.102. For more information, please refer to the security advisory.
Qualys Detection
Qualys customers can scan their devices with QID 376451 to detect vulnerable assets.
We also have a QID 179104 dedicated to the Debian security advisory. Customers can scan their devices with this QID to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://security-tracker.debian.org/tracker/DSA-5092-1
https://security-tracker.debian.org/tracker/CVE-2022-0847
https://www.bleepingcomputer.com/news/security/new-linux-bug-gives-root-on-all-major-distros-exploit-released/
https://arstechnica.com/information-technology/2022/03/linux-has-been-bitten-by-its-most-high-severity-vulnerability-in-years/