Cisco has released a patch for a zero-day vulnerability that exists in its IOS XR router software. Tracked as CVE-2022-20821, the vulnerability could allow an unauthenticated attacker to access Redis instances running in NOSi docker containers remotely.
The vulnerability was found during the resolution of a Cisco TAC support case. The vulnerability affects Cisco 8000 series routers running a vulnerable release of Cisco IOS XR software and having the health check RPM installed and active.
The Cisco IOS XR software is a distributed operating system designed for continuous system operation combined with service flexibility and speed. The IOS XR Network OS is deployed on multiple Cisco router platforms, including NCS 540 & 560, NCS 5500, 8000, and ASR 9000 series routers.
Description
The vulnerability (CVE-2022-20821) arises because, on activation, the health check RPM opens TCP port 6379 by default. An attacker could take advantage of this vulnerability by connecting to the Redis instance over an open port. On successful exploitation, this vulnerability could allow an attacker to write to the Redis in-memory database, write arbitrary files to the container filesystem, and obtain Redis database information.
Because the Redis instance runs in a sandboxed container, even if attackers successfully exploit this vulnerability, they will not be able to execute code remotely or compromise the host system’s integrity.
Affected versions
Cisco devices running on Cisco IOS XR Software version 7.3.3 are affected by this vulnerability.
Customers can use the “run docker ps” CLI command to determine if the device is vulnerable. If the output returns a docker container with the name NOSi then the device is vulnerable.
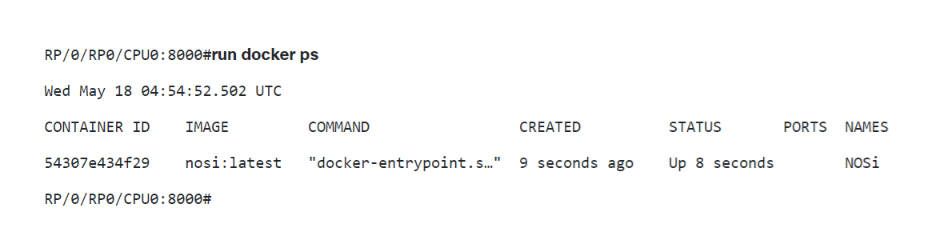
Image Source: Cisco Advisory
Workaround
Cisco has mentioned the following workarounds to address the vulnerability. Choose one of the following mitigations based on your environment:
Option 1: Disable health check and explicitly disable the use cases
To effectively disable health check, enter the following commands exactly as shown:
RP/0/RP0/CPU0:8000(config)#no healthcheck enable
RP/0/RP0/CPU0:8000(config)#healthcheck use-case asic-reset disable
RP/0/RP0/CPU0:8000(config)#healthcheck use-case packet-drop disable
RP/0/RP0/CPU0:8000(config)#commit
RP/0/RP0/CPU0:8000#
Then remove the health check RPM from the device:
RP/0/RP0/CPU0:8000#install package remove xr-healthcheck
Wed May 18 05:00:08.060 UTCInstall remove operation 5.2.2 has started
Install operation will continue in the background
RP/0/RP0/CPU0:8000#
RP/0/RP0/CPU0:8000#install apply restart
Wed May 18 05:01:08.842 UTC
Install apply operation 5.2 has started
Install operation will continue in the background
RP/0/RP0/CPU0:8000#
Option 2: Use an Infrastructure Access Control List (iACLs) to block port 6379
To protect infrastructure devices and minimize the risk, impact, and effectiveness of direct infrastructure attacks, administrators are advised to deploy infrastructure access control lists (iACLs) to perform policy enforcement of traffic sent to infrastructure equipment. Administrators can construct an iACL by explicitly permitting only authorized traffic sent to infrastructure devices in accordance with existing security policies and configurations.
For more information, read the Cisco Advisory.
Mitigation
Customers are advised to upgrade to the latest Cisco IOS XR Software version 7.3.4. Please refer to the official Cisco Security Advisory ( cisco-sa-iosxr-redis-ABJyE5xK) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 317189 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://thehackernews.com/2022/05/cisco-issues-patches-for-new-ios-xr.html
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxr-redis-ABJyE5xK
https://www.bleepingcomputer.com/news/security/cisco-urges-admins-to-patch-ios-xr-zero-day-exploited-in-attacks/