WSO2 has released a fix for a Reflected Cross-Site Scripting (XSS) vulnerability in the Management Console. The vulnerability, tracked as CVE-2022-29548, can be exploited by tampering with the parameter in the Management Console. This vulnerability exists due to improper output encoding and affects various WSO2 products.
WSO2 is an open-source software provider that offers an enterprise platform for integrating application programming interfaces (APIs), applications, and web services locally and across the Internet.
According to OWASP, the Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious JavaScript is injected into otherwise safe and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, in the form of a browser side script, to a different end-user.
There are three main types of XSS attacks.
- Reflected XSS: Occurs when user input is immediately returned by a web application in an error message, search result, or any other response.
- Stored XSS: Occurs when user input is stored on the target server, such as in a database, in a message forum, visitor log, comment field, etc.
- DOM-based XSS: A form of XSS where the entire tainted data flow from source to sink takes place in the browser and the data flow never leaves the browser.
Description
The vulnerable versions of the WSO2 management console have an improper output encoding which allows an attacker to perform the Reflected Cross-Site Scripting (XSS) attack by altering the parameters of the management console.
According to the vendor, successful exploitation of this vulnerability allows a malicious actor to redirect the browser to a malicious website, make changes in the UI (User Interface) of the web page, retrieve information from the browser, or harm otherwise. However, since all the session-related sensitive cookies are set with the httpOnly flag and protected, session hijacking or similar attacks would not be possible.
The exploit works by injecting some JavaScript into the errorCode URL parameter. The associated vulnerable endpoint is /carbon/admin/login.jsp. An attacker can inject malicious JavaScript as follows by sending a simple GET request to the vulnerable server.
GET /carbon/admin/login.jsp?loginStatus=false&errorCode=');alert('qualystest')//
At Qualys Labs, we tested the vulnerability on multiple WSO2 products.
Product: WSO2 API manager
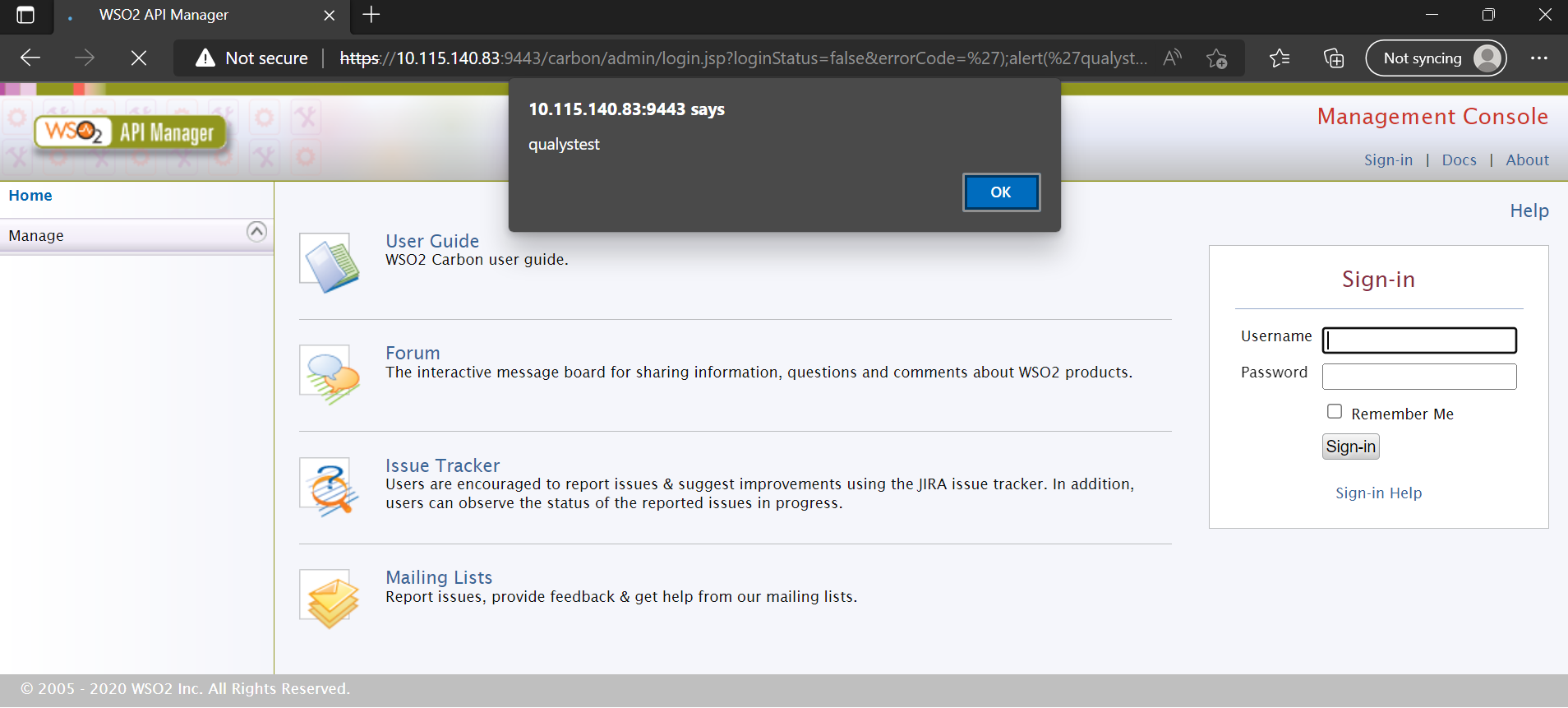 Image Source: Qualys Labs
Image Source: Qualys Labs
Product: WSO2 Identity Server
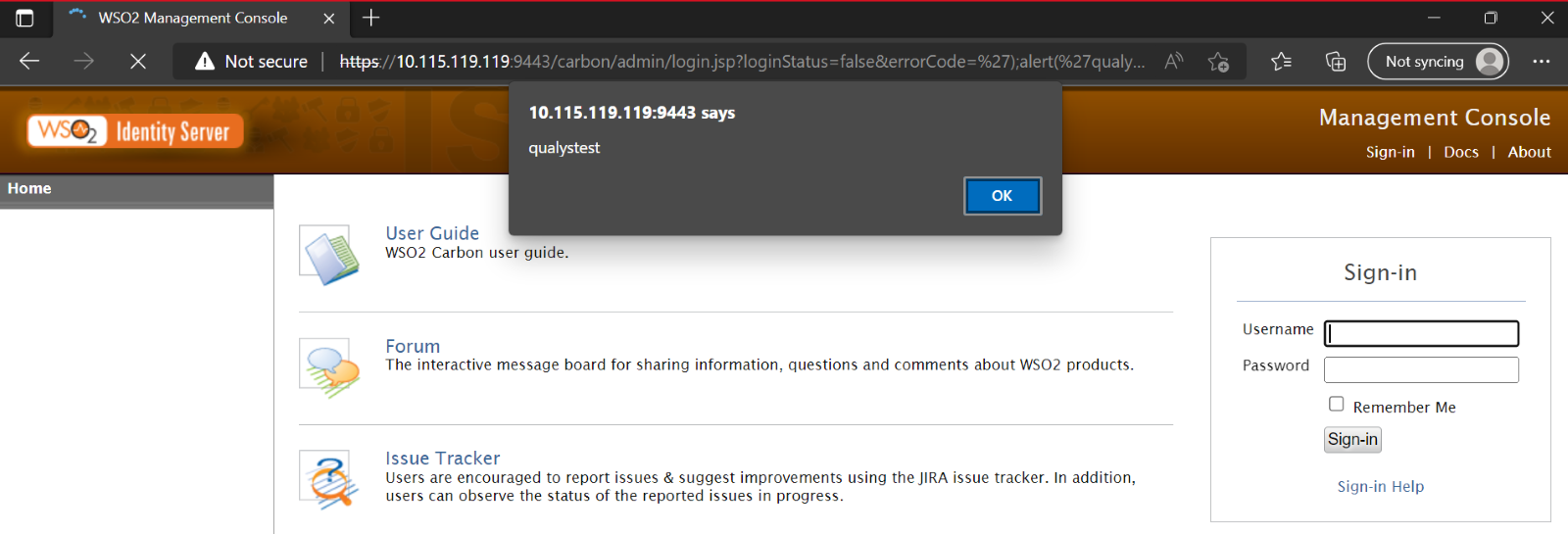
Image Source: Qualys Labs
Affected versions
- WSO2 Micro Integrator: 1.0.0
- WSO2 API Microgateway: 2.2.0
- WSO2 Data Analytics Server: 3.2.0
- WSO2 Identity Server Analytics: 5.5.0, 5.6.0
- WSO2 API Manager Analytics: 2.2.0, 2.5.0, 2.6.0
- WSO2 IS as Key Manager: 5.5.0, 5.6.0, 5.7.0, 5.9.0, 5.10.0
- WSO2 Enterprise Integrator: 6.2.0, 6.3.0, 6.4.0, 6.5.0, 6.6.0
- WSO2 Identity Server: 5.5.0, 5.6.0, 5.7.0, 5.9.0, 5.10.0, 5.11.0
- WSO2 API Manager: 2.2.0, 2.5.0, 2.6.0, 3.0.0, 3.1.0, 3.2.0, 4.0.0
Mitigation
The vendor has released a patch addressing the XSS vulnerability. Customers can refer to the WSO2 Security Advisory WSO2-2021-1603 to know more about patch details.
Qualys Detection
Qualys customers can scan their devices with QID 730513 to detect vulnerable assets.
Continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://github.com/cxosmo/CVE-2022-29548
https://owasp.org/www-community/attacks/xss/
https://docs.wso2.com/display/Security/Security+Advisory+WSO2-2021-1603