Cybersecurity researchers from Palo Alto Networks Unit 42 have discovered a new vulnerability in Microsoft’s Service Fabric – commonly used with Azure. Tracked as CVE-2022-30137, the vulnerability could allow a malicious actor with access to a compromised container to escalate privileges and gain control of the resource’s host Service Fabric node and the entire cluster.
The vulnerability is named FabricScape and could be exploited on containers that are configured to have runtime access, which is granted by default to every container. According to the MSRC blog, the bug exists on both Windows and Linux, but it is only exploitable on Linux. The Windows operating system is not vulnerable to this attack.
According to Microsoft, the Azure Service Fabric is a distributed systems platform that makes it easy to package, deploy, and manage scalable and reliable microservices and containers.
A Service Fabric cluster is a group of network-connected nodes created to manage and run applications made up of microservices or containers. According to Microsoft, it powers many Microsoft services today, including Azure SQL Database, Azure Cosmos DB, Cortana, Microsoft Power BI, Microsoft Intune, Azure Event Hubs, Azure IoT Hub, Dynamics 365, Skype for Business, and many other core Azure services.
An example of a Service Fabric Linux node is shown in the image below:
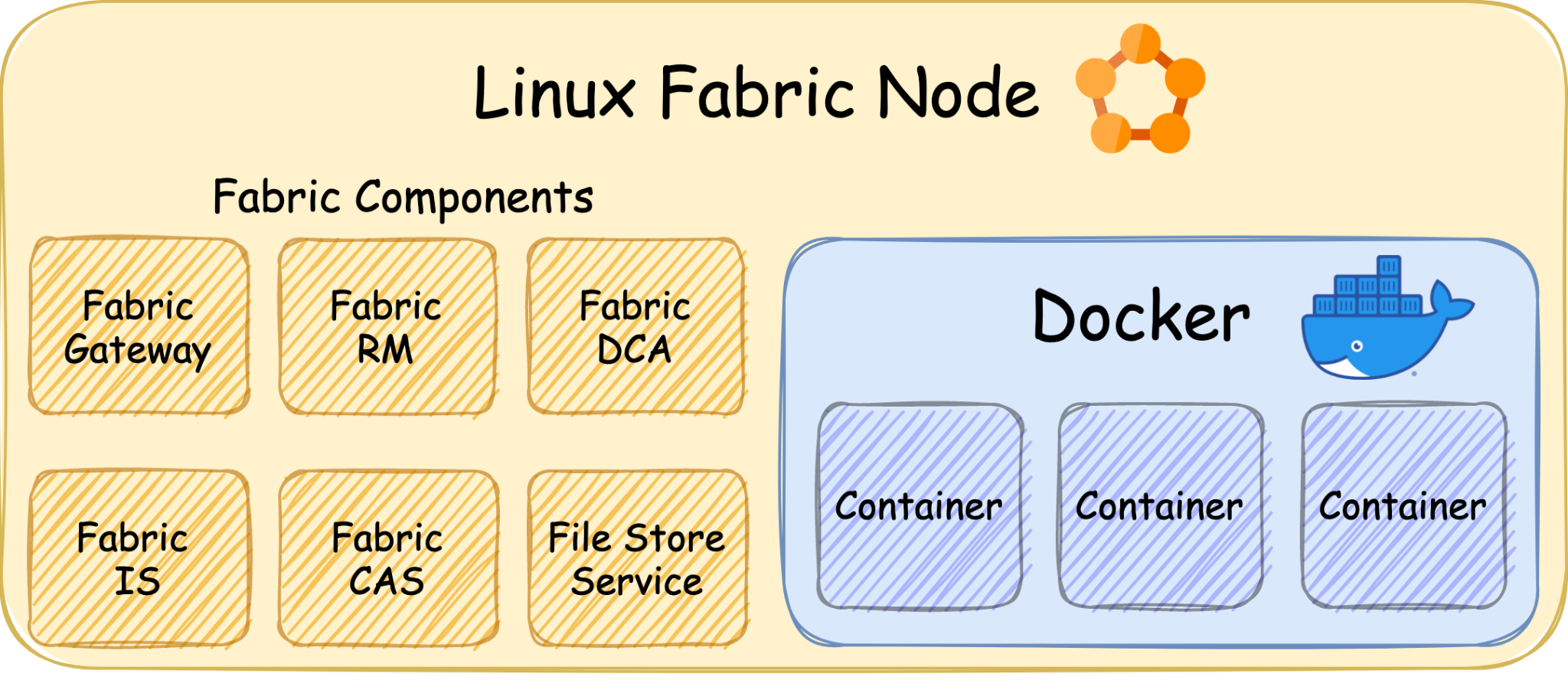 Image Source: Palo Alto Networks Unit 42
Image Source: Palo Alto Networks Unit 42
Description
Service Fabric deploys applications as containers and during the container initialization process, it creates new logs. These logs are mounted into each container with read and write permission. On each node, each of the directories is concentrated in a single path.
The Data Collection Agent (DCA) is a part of Service Fabric that gathers the logs from the directories for further processing. It runs as root on every node since it requires high rights to access the directories.
It manages files that containers could modify simultaneously. Therefore, exploiting a vulnerability in the agent’s mechanism that handles these files could result in a container escape and gaining root on the node.
According to the MSRC blog, for the successful exploitation of this vulnerability, these ordered steps are required:
-
- Step 1: An attacker must compromise a containerized workload deployed by the owner of a Linux Service Fabric cluster.
- Step 2: The malicious code running inside the container could substitute an index file read by DCA with a symlink race.
- Using an additional timing attack, an attacker could gain control of the machine hosting the Service Fabric node.
The DCA source code contains a potential race-conditioned arbitrary write in the function GetIndex. This function reads a file, verifies that the content is in the desired format, alters some of the material, and then overwrites the original file with the modified content.
It uses two sub-functions to accomplish the tasks:
- LoadFromFile – reads the file
- SaveToFile – writes new data to the file
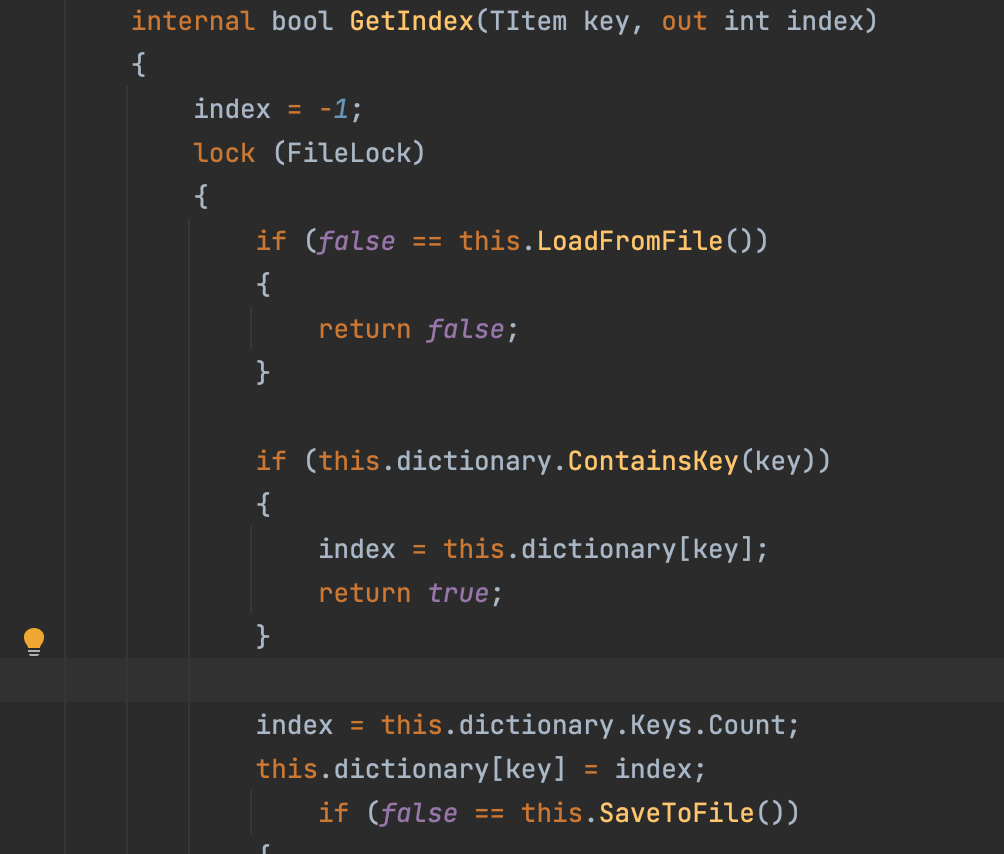 Image Source: Palo Alto Networks Unit 42
Image Source: Palo Alto Networks Unit 42
Exploitation of the FabricScape vulnerability
To take advantage of the flaw, an attacker must get DCA to run the vulnerable function on a file it controls. DCA keeps track of the emergence of filenames and performs various operations for each file.
When DCA discovers that this file was generated, it calls a function that ultimately calls GetIndex several times on paths inside the container-modifiable log directory. To overcome the race situation and overwrite any path on the node filesystem, a malicious container may allow GetIndex to be executed on a file that it controls.
Affected versions
Microsoft Service Fabric version prior to 9.0.1035.1 is affected by the vulnerability.
The vulnerability does not affect the Windows operating system, it is only exploitable on Linux.
Mitigation
Microsoft mentioned in a blog that “Customers without automatic updates enabled should upgrade their Linux clusters to the most recent Service Fabric release. Release notes can be found here.”
“Customers whose Linux clusters are automatically updated do not need to take further action.”, Microsoft adds further.
Please refer to the Microsoft Advisory for more information about the vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 376710 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://unit42.paloaltonetworks.com/fabricscape-cve-2022-30137/
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30137
https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-overview
https://thehackernews.com/2022/06/new-fabricscape-bug-in-microsoft-azure.html
https://msrc-blog.microsoft.com/2022/06/28/azure-service-fabric-privilege-escalation-from-containerized-workloads-on-linux/