Microsoft has released fixes for 84 security flaws in its July 2022 edition of Patch Tuesday. This month’s update includes a fix for one zero-day (CVE-2022-22047). Out of the 84 vulnerabilities, four are rated as critical. All the critical vulnerabilities are Remote Code Execution (RCE). Microsoft also released two Microsoft Edge (Chromium-Based) security updates earlier this month.
The advisory covers 36 products, features, and roles, including Azure Site Recovery, Windows Hyper-V, Xbox, Windows Network File System, Windows BitLocker, Windows Boot Manager, DNS Server, Windows Group Policy, Windows Kernel, Microsoft Office, and many more.
The vulnerabilities are classified as follows:
- Tampering: 2
- Denial of Service: 5
- Elevation of Privilege: 50
- Security Feature Bypass: 4
- Information Disclosure: 11
- Remote Code Execution: 12
Zero-day vulnerability addressed in Patch Tuesday, July 2022 Edition
Windows CSRSS Elevation of Privilege Vulnerability (CVE-2022-22047)
The elevation-of-privilege vulnerability affects all currently supported versions of Microsoft’s pervasive operating system. An attacker with an already-existing foothold can exploit this vulnerability to gain SYSTEM-level privileges.
Critical vulnerabilities addressed in Patch Tuesday, July 2022 Edition
Windows Graphics Component Remote Code Execution Vulnerability (CVE-2022-30221)
To exploit this vulnerability, an attacker would have to convince a targeted user to connect to a malicious RDP server. Upon connection, the malicious server could execute code on the victim’s system in the context of the targeted user. The vulnerability is effective on Windows 7 Service Pack 1 or Windows Server 2008 R2 Service Pack 1 if either RDP 8.0 or RDP 8.1 is installed.
Windows Print Spooler Elevation of Privilege Vulnerability (CVE-2022-30206)
This vulnerability was discovered by luckyu with NSFOCUS TIANYUAN LAB and Victor Mata with FusionX, Accenture Security. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
Windows Network File System Remote Code Execution Vulnerability (CVE-2022-22029)
Successful exploitation of this vulnerability requires an attacker to invest time in repeated exploitation attempts through sending constant or intermittent data An attacker might use this flaw to run arbitrary code on the system by delivering a specially crafted request.
Remote Procedure Call Runtime Remote Code Execution Vulnerability (CVE-2022-22038)
Successful exploitation of this vulnerability requires an attacker to invest time in repeated exploitation attempts through sending constant or intermittent data.
Windows Network File System Remote Code Execution Vulnerability (CVE-2022-22039)
To successfully exploit this vulnerability, an attacker must succeed in a race condition. Making an unauthenticated, carefully constructed call to a Network File System (NFS) service could be used to exploit this vulnerability over the network remotely.
Microsoft Edge (Chromium-based) Type Confusion in V8 Vulnerability (CVE-2022-2294)
This is a heap-based buffer overflow vulnerability in the WebRTC (Web Real-Time Communications) component. This component is responsible for providing real-time audio and video communication capabilities in browsers without installing any plugins or downloading native apps.
Visit the July 2022 Security Updates page to access the full description of each vulnerability and the systems it affects.
Workaround/Mitigation Detection
Microsoft has released workarounds for vulnerabilities in Windows Print Spooler and Windows Network File System.
Windows Print Spooler Elevation of Privilege Vulnerability (CVE-2022-30206, CVE-2022-22041, CVE-2022-22022, CVE-2022-30226)
Determine if the Print Spooler service is running
Run the following in Windows PowerShell:
Get-Service -Name Spooler
If the Print Spooler is running or if the service is not disabled, follow these steps:
Stop and disable the Print Spooler service
If stopping and disabling the Print Spooler service is appropriate for your environment, run the following in Windows PowerShell:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Windows Network File System Remote Code Execution Vulnerability (CVE-2022-22029)
The following PowerShell command will disable NFSV3:
Set-NfsServerConfiguration -EnableNFSV3 $false
After this, you will need to restart the NFS server or reboot the machine.
To restart the NFS server, start a cmd window with Run as Administrator, and enter the following commands:
- nfsadmin server stop
- nfsadmin server start
To confirm that NFSv3 has been turned off, run the following command in a PowerShell window:
PS C:\Get-NfsServerConfiguration
Here is the sample output, and notice the EnableNFSv3 is “False” now:
State : Running
LogActivity :
CharacterTranslationFile : Not Configured
DirectoryCacheSize (KB) : 128
HideFilesBeginningInDot : Disabled
EnableNFSV2 : False
EnableNFSV3 : False
EnableNFSV4 : True
EnableAuthenticationRenewal : True
AuthenticationRenewalIntervalSec : 600
NlmGracePeriodSec : 45
MountProtocol : {TCP, UDP}
NfsProtocol : {TCP, UDP}
NisProtocol : {TCP, UDP}
NlmProtocol : {TCP, UDP}
NsmProtocol : {TCP, UDP}
PortmapProtocol : {TCP, UDP}
MapServerProtocol : {TCP, UDP}
PreserveInheritance : False
NetgroupCacheTimeoutSec : 30
UnmappedUserAccount :
WorldAccount : Everyone
AlwaysOpenByName : False
GracePeriodSec : 240
LeasePeriodSec : 120
OnlineTimeoutSec : 180
Evaluating workaround using Qualys Policy Compliance (PC)
Qualys Policy Compliance customers can evaluate workaround based on the following Controls:
CVE-2022-30206, CVE-2022-22041, CVE-2022-22022, CVE-2022-30226 – Windows Print Spooler Elevation of Privilege Vulnerability
1368 Status of the ‘Print Spooler’ service.
CVE-2022-22029- Windows Network File System Remote Code Execution Vulnerability
23841 Status of the Windows Network File System (NFSV3) service.
CVE-2022-30136 – Windows Network File System Remote Code Execution Vulnerability
24139 Status of the Windows Network File System (NFSV4) service.
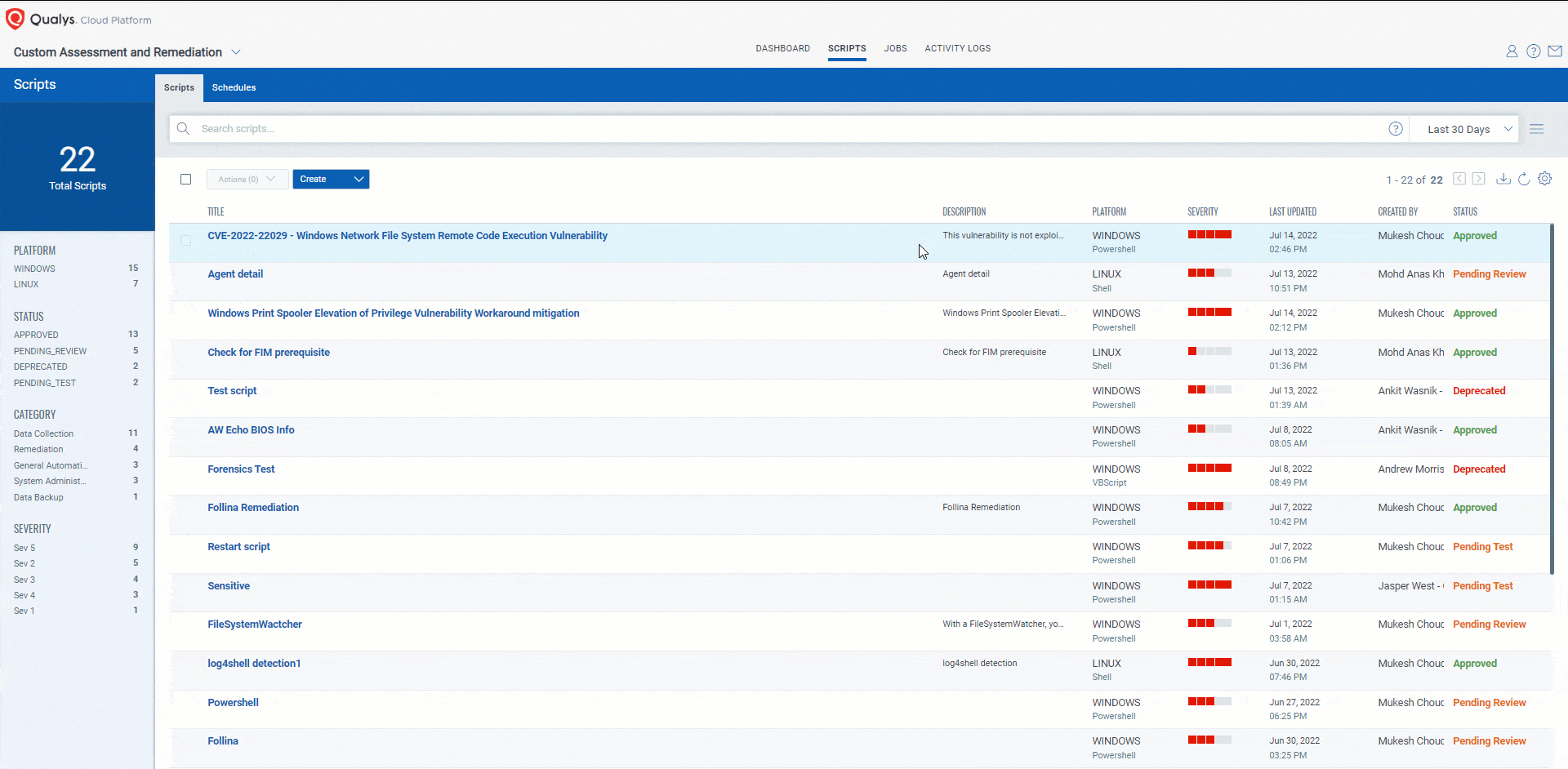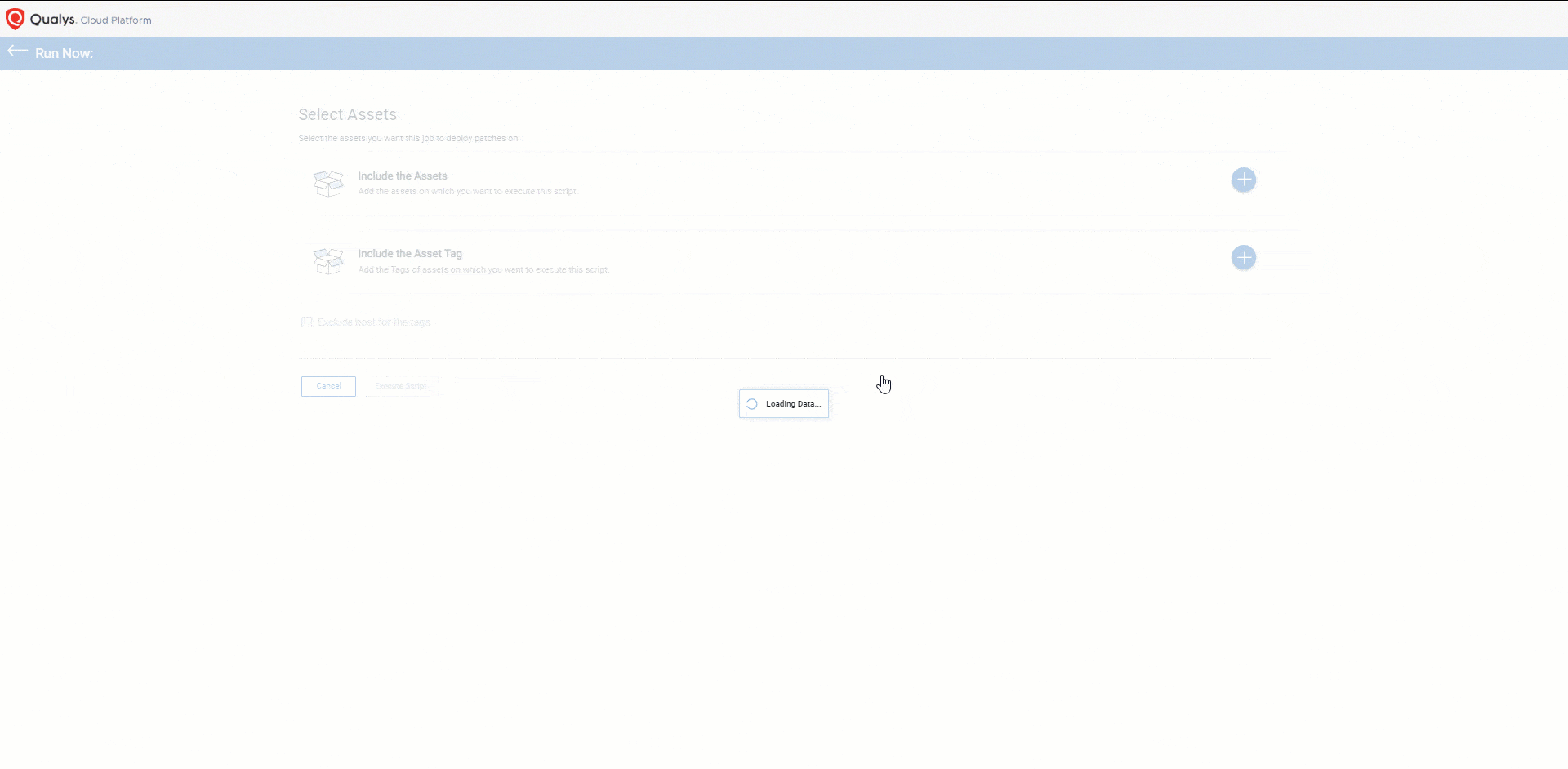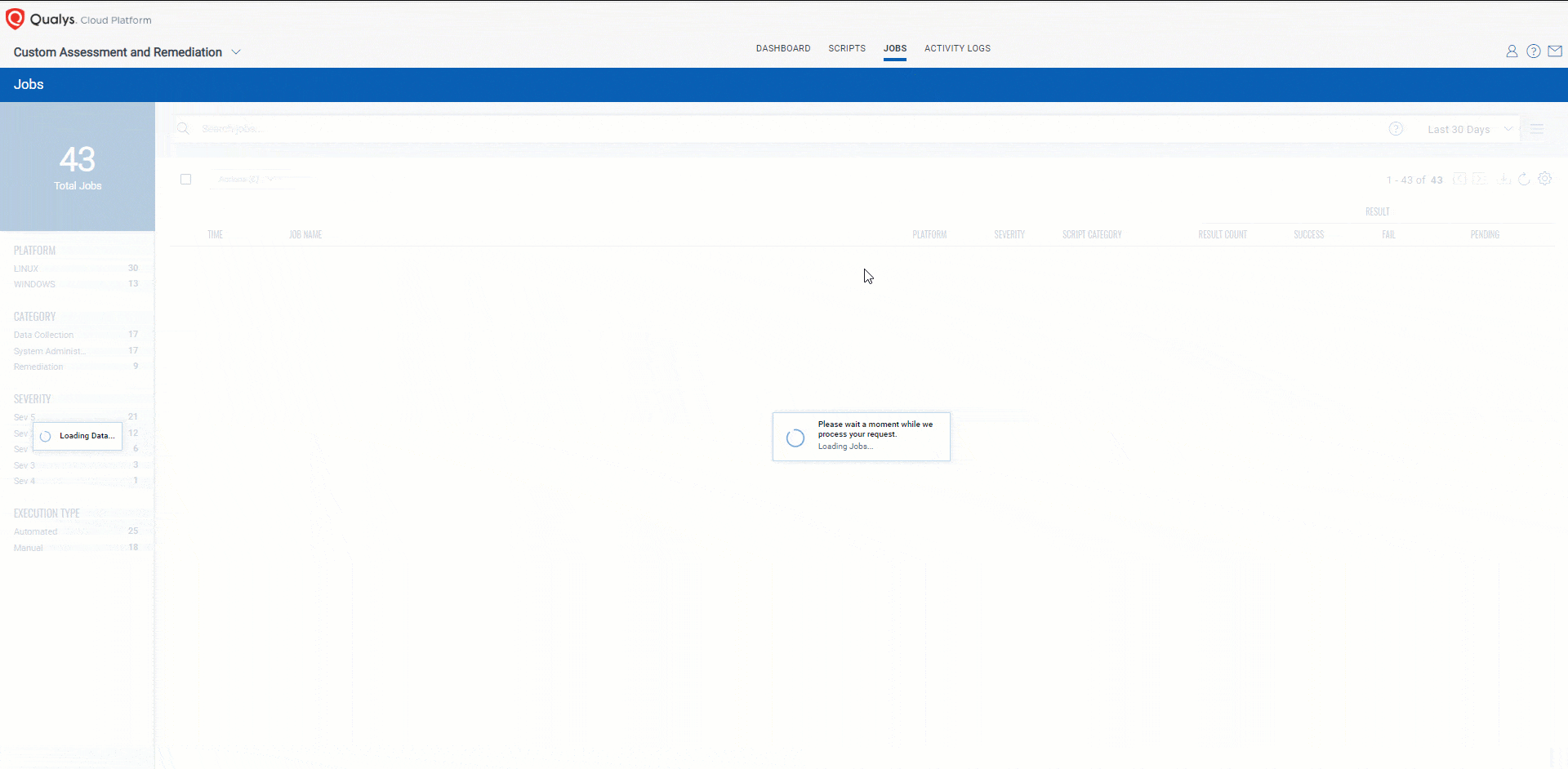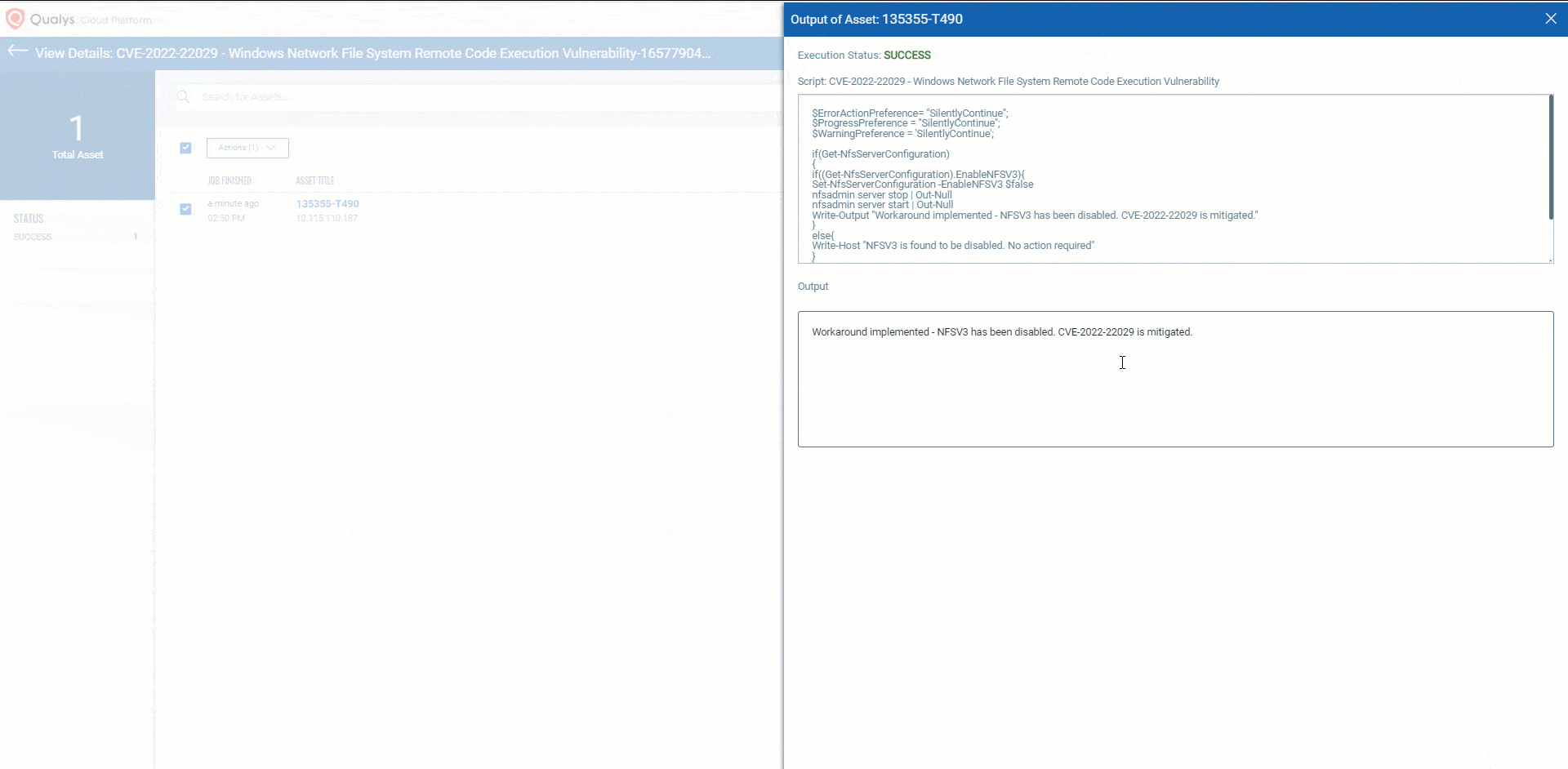
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on the vulnerable assets.
CVE-2022-30206, CVE-2022-22041, CVE-2022-22022, CVE-2022-30226 – Windows Print Spooler Elevation of Privilege Vulnerability
Source: Qualys
Impact of workaround: Stopping and disabling the Print Spooler service disables the ability to print both locally and remotely.
CVE-2022-22029- Windows Network File System Remote Code Execution Vulnerability
NOTE: This vulnerability is not exploitable in NFSV4.1. Before updating your version of Windows that protects against this vulnerability, you can mitigate an attack by disabling NFSV3. This may adversely affect your ecosystem and should only be used as temporary mitigation.
Source: Qualys
To re-enable NFSv3 when the machine is patched, enter the following command:
Set-NfsServerConfiguration -EnableNFSV3 $True
Again, after this, you will need to restart the NFS server or reboot the machine.
CVE-2022-30136 – Windows Network File System Remote Code Execution Vulnerability
This vulnerability is not exploitable in NFSV2.0 or NFSV3.0. Before updating your Windows version that protects against this vulnerability, you can mitigate an attack by disabling NFSV4.1. This could adversely affect your ecosystem and should only be used as temporary mitigation.
Warning: You should NOT apply this mitigation unless you have installed the May 2022 Windows security updates. Those updates address CVE-2022-26937 which is a Critical vulnerability in NFSV2.0 and NFSV3.0.
Source: Qualys
To re-enable NFSv4.1 after you have installed the June 2022 security update, enter the following command:
Set-NfsServerConfiguration -EnableNFSV4 $True
Again, after running the command you will need to restart the NFS server or reboot the machine.
Qualys customers can scan their network with QIDs 110411, 110412, 376725, 91921, 91922, 91923, 91924, and 91927 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/releaseNote/2022-Jul
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-2294
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-2295
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30206
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30136
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-22029
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-22038
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-22039