Atlassian has released a patch to address a hardcoded credentials vulnerability in Confluence Server and Data Center. Tracked as CVE-2022-26138, the vulnerability can allow an unauthenticated, remote attacker to log into vulnerable servers. Atlassian has rated the vulnerability as Critical as there are reports of this vulnerability being exploited in the wild and the hardcoded passwords are also publicly known. The advisory also states that the Questions for Confluence app for Confluence Cloud is not affected by this vulnerability.
Questions for Confluence offers a cutting-edge substitute to forums for information exchange and social interaction through questions and answers. Currently installed on more than 8,000 Confluence servers, the app helps the organization’s internal Q&A staff communicate more effectively.
Description
A Confluence user account with the username disabledsystemuser is created when the Questions for Confluence app is activated on Confluence Server or Data Center. This account helps administrators move data from the app to Confluence Cloud. The disabledsystemuser account is created with a hardcoded password and is added to the confluence-users group. This group has the default permission for viewing and editing any non-restricted pages inside Confluence.
The hardcoded password could be used by a remote, unauthenticated attacker to log into Confluence and access any pages that the confluence-users group has access to.
The disabledsystemuser account is set up with a third-party email address that is not within Atlassian’s control. A vulnerable instance that has been set up to email notifications will do so if this vulnerability has not been fixed. One type of email notification is called Recommended Updates Notifications, which lists the most popular Confluence spaces pages that the user is authorized to see. In order to investigate and close the account, Atlassian is actively collaborating with the third-party email address service provider.
Anton has discovered and publicly disclosed the hardcoded password on Twitter.
How To Determine If You Are Affected
According to the advisory, a Confluence Server or Data Center instance is affected if it has an active user account with the following information:
- User: disabledsystemuser
- Username: disabledsystemuser
- Email: do****************@em***.com
- Password: disabled1system1user6708
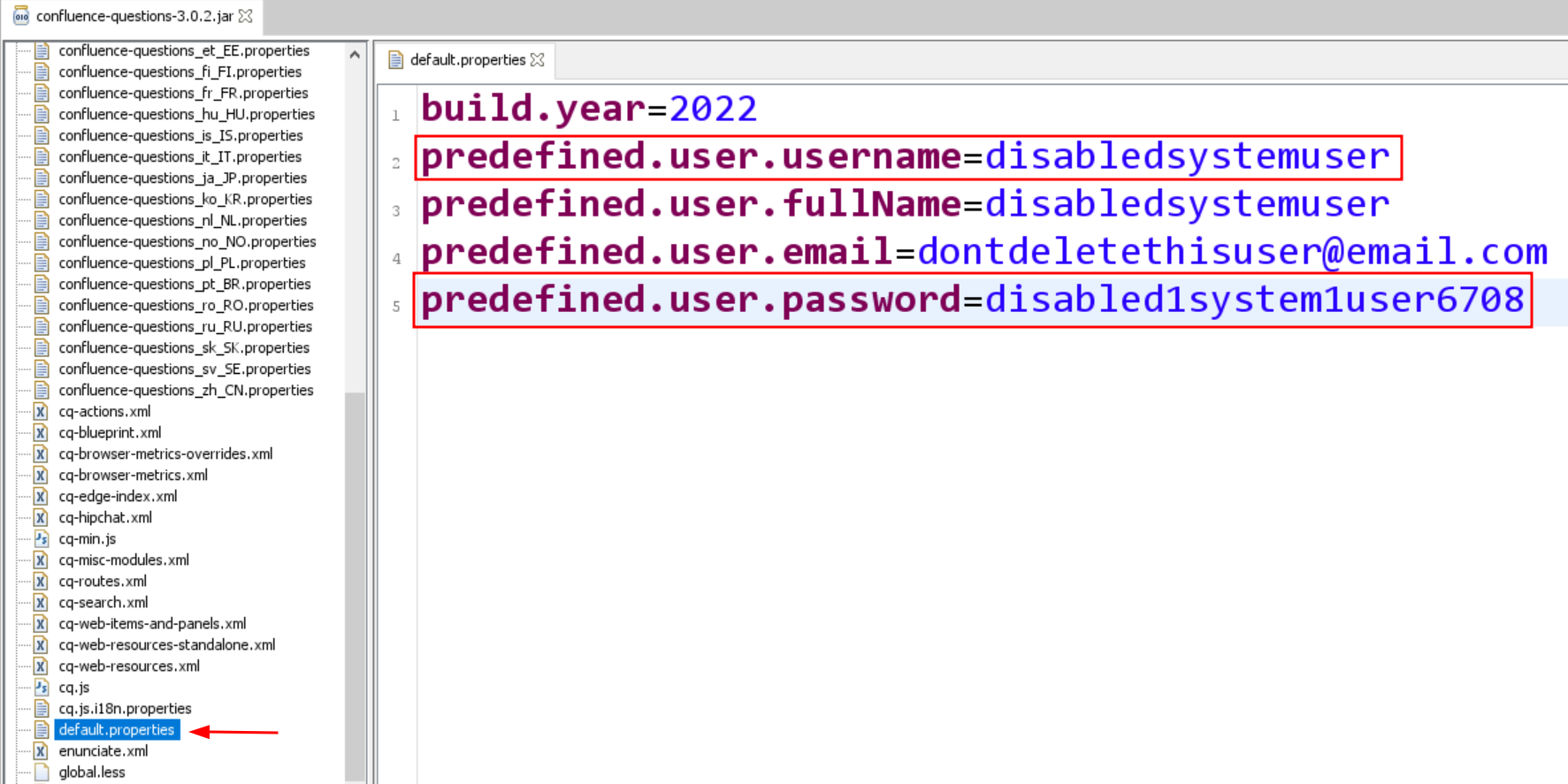
Image Source: Qualys
Note: This account can also be present if the Questions for Confluence app has previously been installed and uninstalled.
If this account does not show up in the list of active users, the Confluence instance is not affected.
Affected versions
- Questions for Confluence 2.7.34, 2.7.35, and 3.0.2
- Confluence Server and Data Center versions 7.4.0, 7.13.0, 7.4.12, 7.16.0, 7.15.1, and 7.17.0
Mitigation
The advisory states, “Uninstalling the Questions for Confluence app does not remediate this vulnerability. The disabledsystemuser account does not automatically get removed after the app has been uninstalled. If you have verified a Confluence Server or Data Center instance is affected, two equally effective ways to remediate this vulnerability are listed below.”
Option 1: Update to a non-vulnerable version of Questions for Confluence
Update the Questions for Confluence app to a fixed version:
- 2.7.x >= 2.7.38 (compatible with Confluence 6.13.18 through 7.16.2)
- Versions >= 3.0.5 (compatible with Confluence 7.16.3 and later)
For more information on how to update an app, refer to:
https://confluence.atlassian.com/upm/updating-apps-273875710.html
Fixed versions of the Questions for Confluence app stop creating the disabledsystemuser user account and remove it from the system if it has already been created.
Note: If Confluence is configured to use a read-only external directory (e.g., Atlassian Crowd), follow Option 2.
Option 2: Disable or delete the disabledsystemuser account
Search for the disabledsystemuser account and either disable it or delete it. For instructions on how to disable or delete an account (including an explanation of the differences between the two options), refer to:
https://confluence.atlassian.com/doc/delete-or-disable-users-138318.html
If the Confluence is running in a cluster, make sure to apply the above update on all the nodes.
Customers can refer to the Questions For Confluence Security Advisory 2022-07-20 to know more about patch details.
Qualys Detection
Qualys customers can scan their devices with QID 730569 to detect vulnerable assets.
Continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://confluence.atlassian.com/doc/questions-for-confluence-security-advisory-2022-07-20-1142446709.html
https://twitter.com/therceman/status/1550791890026565638?s=21&t=nnw9cwCBaYpequsfuhWvBw
https://www.bleepingcomputer.com/news/security/atlassian-fixes-critical-confluence-hardcoded-credentials-flaw/