Microsoft has released its August 2022 Patch Tuesday edition in which 121 vulnerabilities are fixed. The security update addresses two zero-day vulnerabilities (CVE-2022-34713, CVE-2022-30134), one of which is being exploited in the wild (CVE-2022-34713). Out of the 121 vulnerabilities, 17 are rated critical as they allow remote code execution and elevate privileges.
Microsoft also included 20 updates for Microsoft Edge (Chromium-Based) in this Patch Tuesday edition. The vulnerabilities were patched earlier this month and addressed Elevation of Privilege, Remote Code Execution, and Security Feature Bypass vulnerabilities.
The advisory covers 40 products, features, and roles, including Azure Site Recovery, Microsoft Exchange Server, Microsoft Office, Microsoft Windows Support Diagnostic Tool (MSDT), Visual Studio, Windows Hyper-V, Windows Network File System, and many more.
The vulnerabilities are classified as follows:
- Spoofing: 1
- Denial of Service: 7
- Elevation of Privilege: 64
- Security Feature Bypass: 6
- Information Disclosure: 12
- Remote Code Execution: 31
Zero-day vulnerabilities addressed in Patch Tuesday, August 2022 Edition
CVE-2022-34713: Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability
The vulnerability was discovered by Imre Rad in January 2020, but Microsoft did not fix it as they did not consider it a security vulnerability. This vulnerability can be exploited only when a user opens a specially crafted file. This is a variant of the vulnerability publicly known as Dogwalk.
CVE-2022-30134: Microsoft Exchange Information Disclosure Vulnerability
This vulnerability requires a user with an affected version of Exchange Server to access a malicious server. Successful exploitation of this vulnerability allows an attacker to read targeted email messages. Microsoft says that the CVE-2022-30134 vulnerability is publicly disclosed but has not been detected in attacks.
Some of the critical vulnerabilities addressed in Patch Tuesday, August 2022 Edition
CVE-2022-35794: Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability
Successful exploitation of this vulnerability requires an attacker to win a race condition. An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine.
CVE-2022-30133, CVE-2022-35744: Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround prior to installing the updates that address this vulnerability, you can block traffic through that port; thus, rendering the vulnerability unexploitable.
Warning: Disabling Port 1723 could affect communications over your network.
CVE-2022-34691: Active Directory Domain Services Elevation of Privilege Vulnerability
An authenticated user could manipulate attributes on computer accounts that they own or manage and acquire a certificate from Active Directory Certificate Services that would allow elevation of privilege to the System.
Please see Certificate-based authentication changes on Windows domain controllers for more information and ways to protect yourself.
CVE-2022-33646: Azure Batch Node Agent Elevation of Privilege Vulnerability
Successful exploitation of this vulnerability requires an attacker to prepare the target environment to improve exploit reliability.
Evaluating workaround using Qualys Policy Compliance (PC)
Qualys Policy Compliance customers can evaluate workarounds based on the following Controls:
CVE-2022-35793: Windows Print Spooler Elevation of Privilege Vulnerability
21711 Status of the ‘Allow Print Spooler to accept client connections’ group policy setting
1368 Status of the ‘Print Spooler’ service
CVE-2022-35804: SMB Client and Server Remote Code Execution Vulnerability
24476 Status of the SMBv3 Client compressions setting
20233 Status of the SMBv3 Server compressions setting
CVE-2022-35755: Windows Print Spooler Elevation of Privilege Vulnerability
1368 Status of the ‘Print Spooler’ service
CVE-2022-35744, CVE-2022-30133: Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability
14028 List of ‘Outbound Rules’ configured in Windows Firewall with Advanced Security via GPO
11220 List of ‘Inbound Rules’ configured in Windows Firewall with Advanced Security via GPO
CVE-2022-34715: Windows Network File System Remote Code Execution Vulnerability
24139 Status of the Windows Network File System (NFSV4) service
CVE-2022-34691: Active Directory Domain Services Elevation of Privilege Vulnerability
4079 Status of the ‘Active Directory Certificate Service’.
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on the vulnerable assets.
For CAR free trial or schedule a demo: https://www.qualys.com/apps/custom-assessment-remediation/
CVE-2022-35793, CVE-2022-35755 – Windows Print Spooler Elevation of Privilege Vulnerability
Script Details: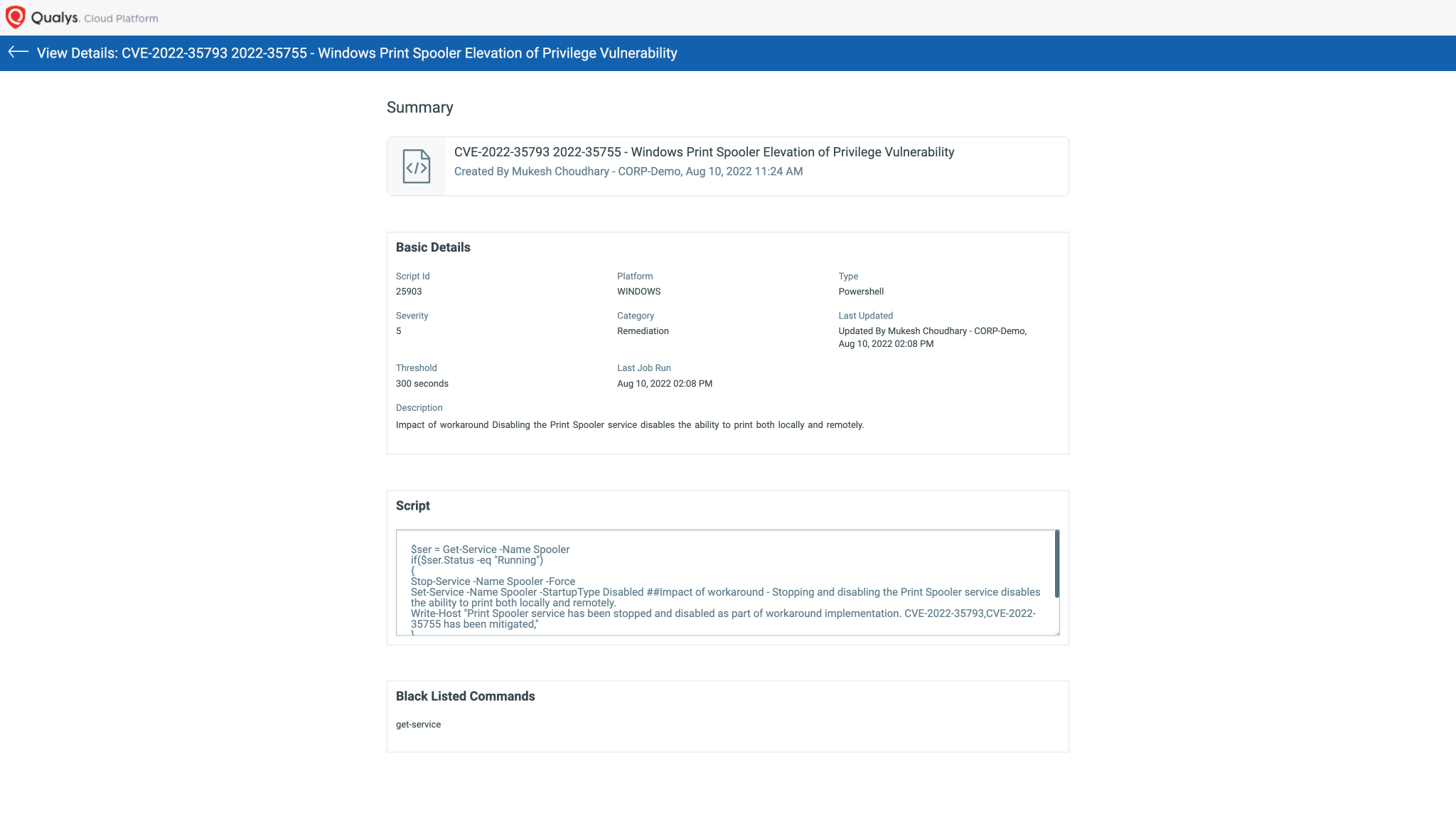 Image source: Qualys
Image source: Qualys
Script Output: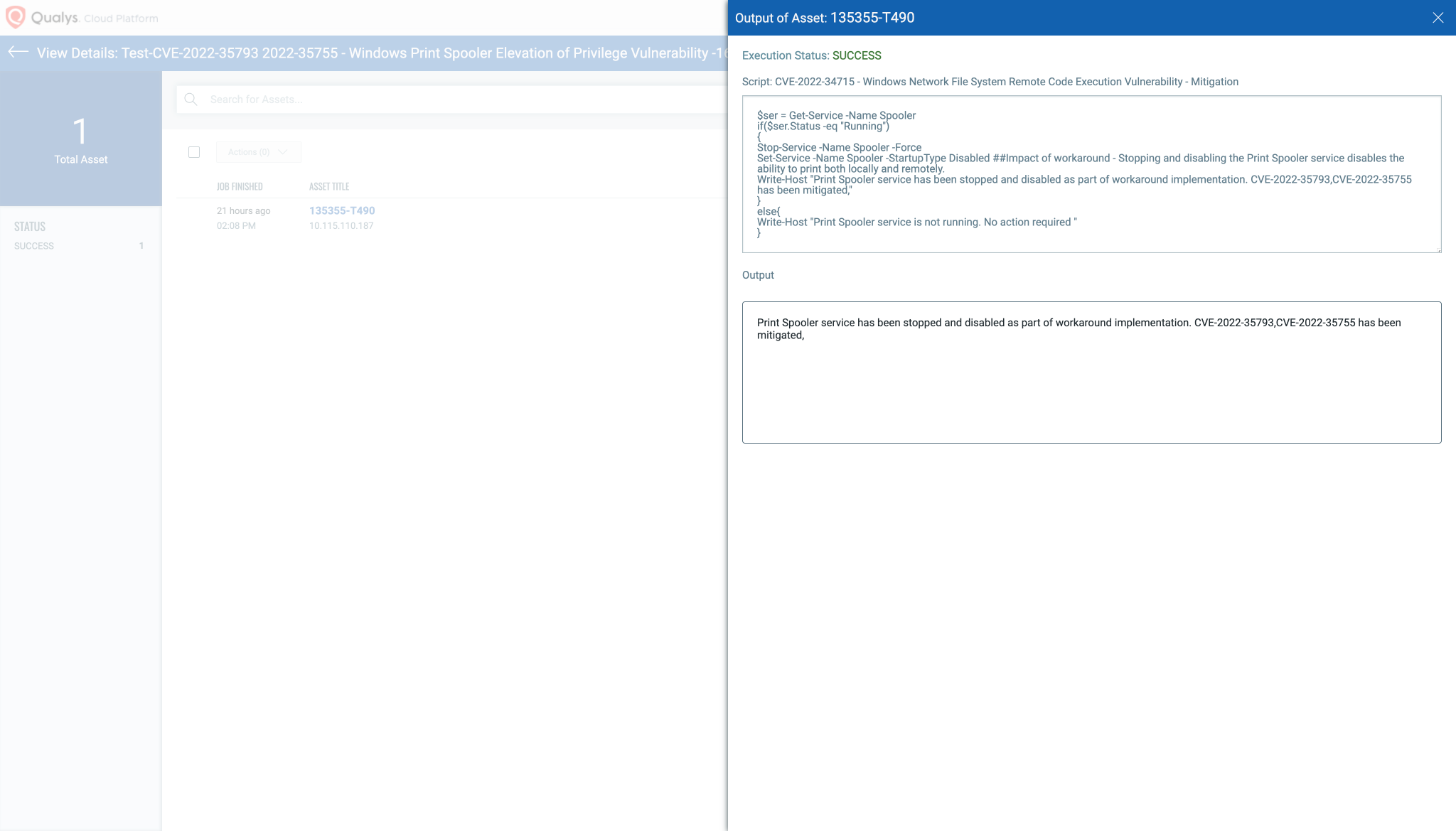 Image source: Qualys
Image source: Qualys
Impact of workaround
Disabling the Print Spooler service disables the ability to print both locally and remotely.
CVE-2022-34715 – Windows Network File System Remote Code Execution Vulnerability
Script Details: 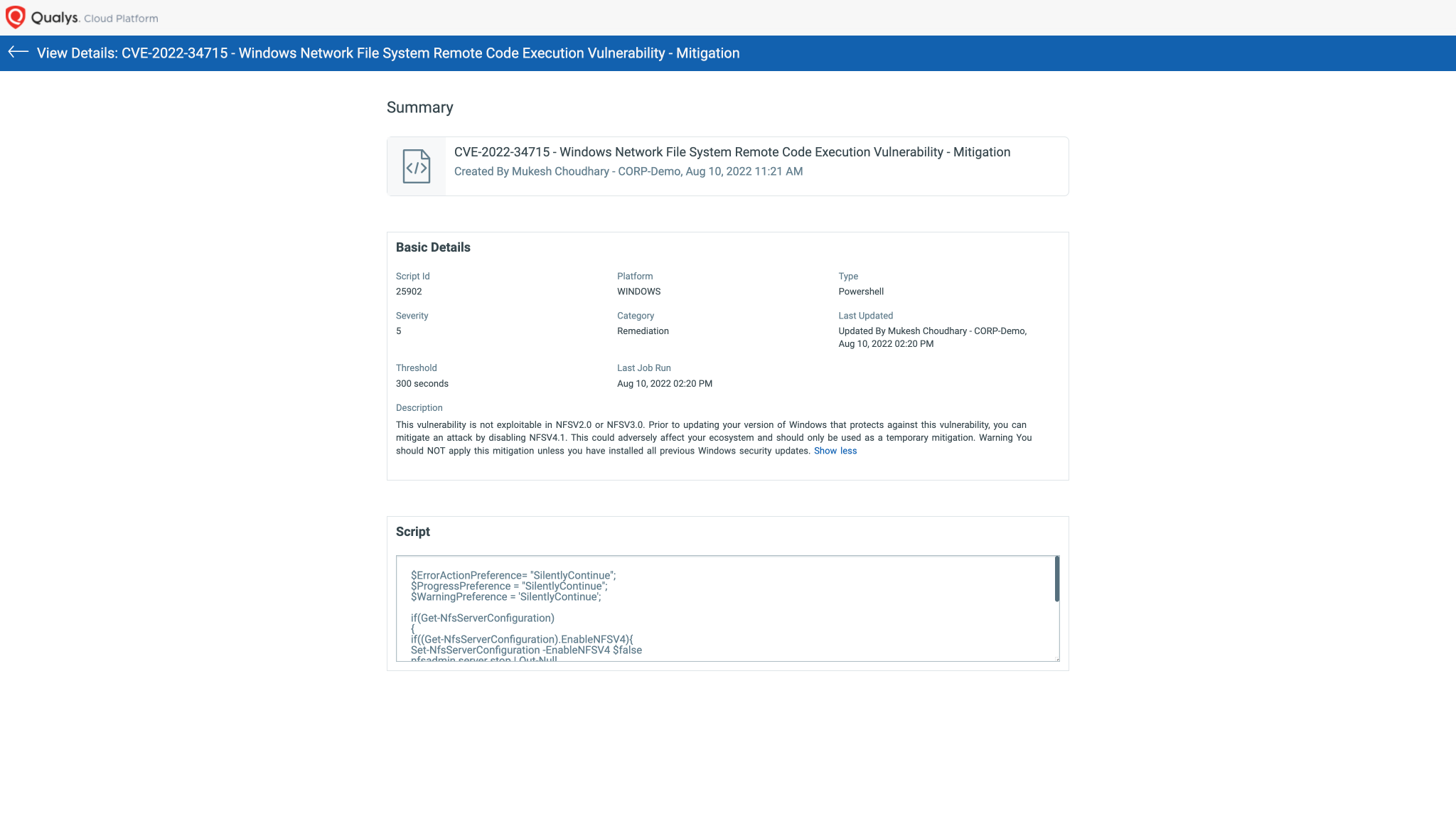 Image source: Qualys
Image source: Qualys
Script Output: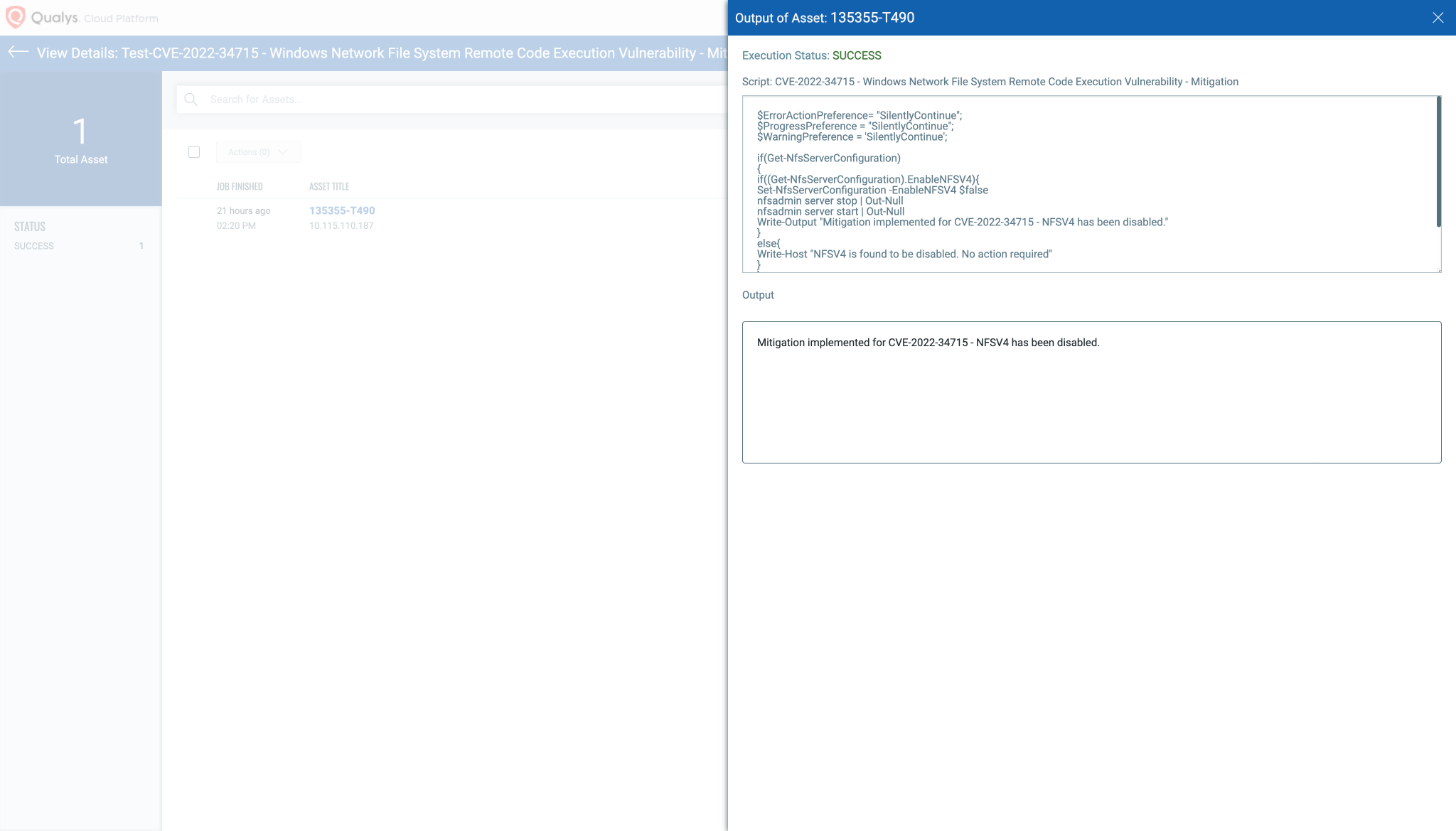 Image source: Qualys
Image source: Qualys
Impact of workaround:
This vulnerability is not exploitable in NFSV2.0 or NFSV3.0. Prior to updating your version of Windows that protects against this vulnerability, you can mitigate an attack by disabling NFSV4.1. This could adversely affect your ecosystem and should only be used as temporary mitigation. Warning You should NOT apply this mitigation unless you have installed all previous Windows security updates.
CVE-2022-35804 – SMB Client and Server Remote Code Execution Vulnerability
Script Details: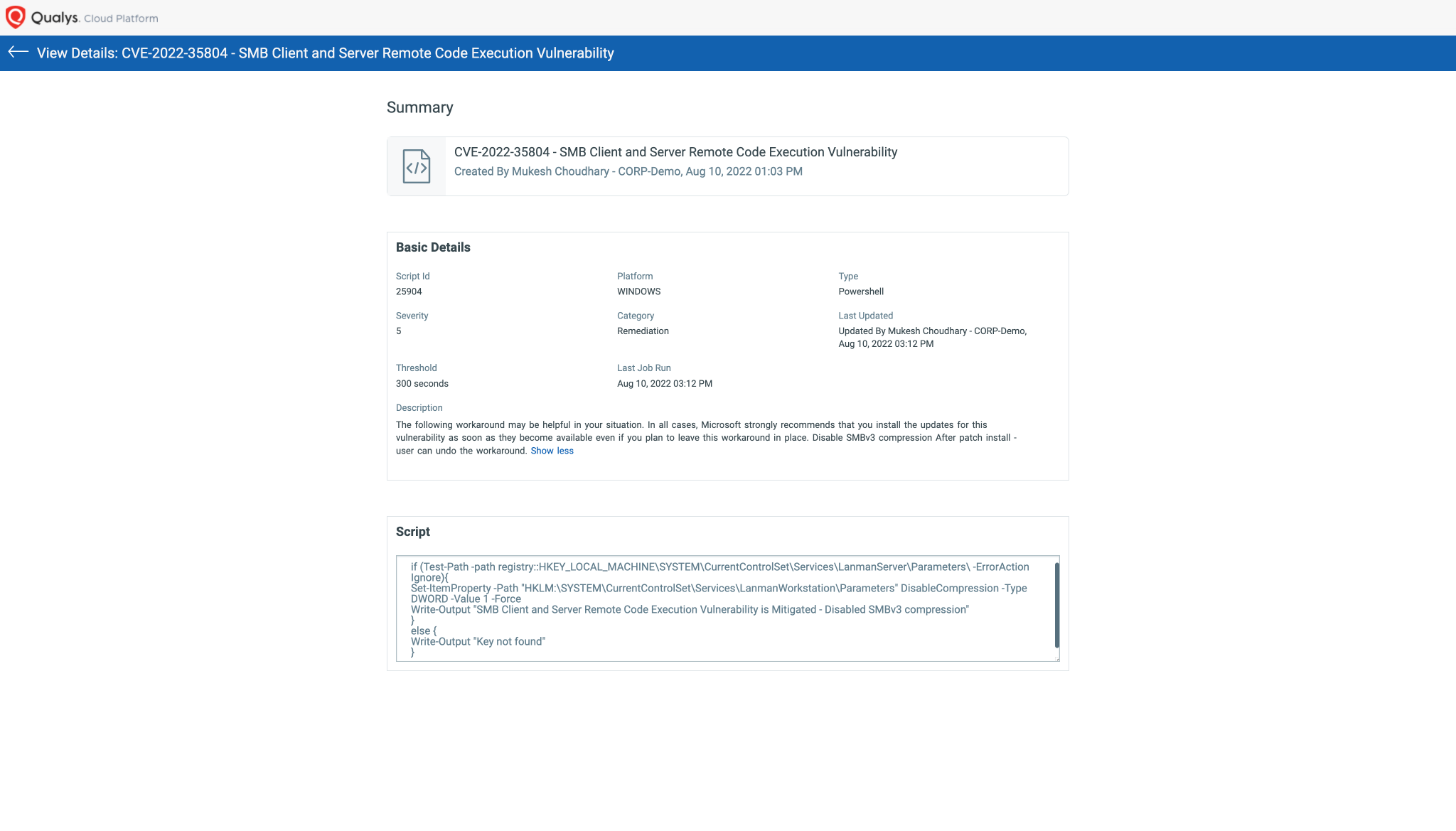 Image source: Qualys
Image source: Qualys
Script Output: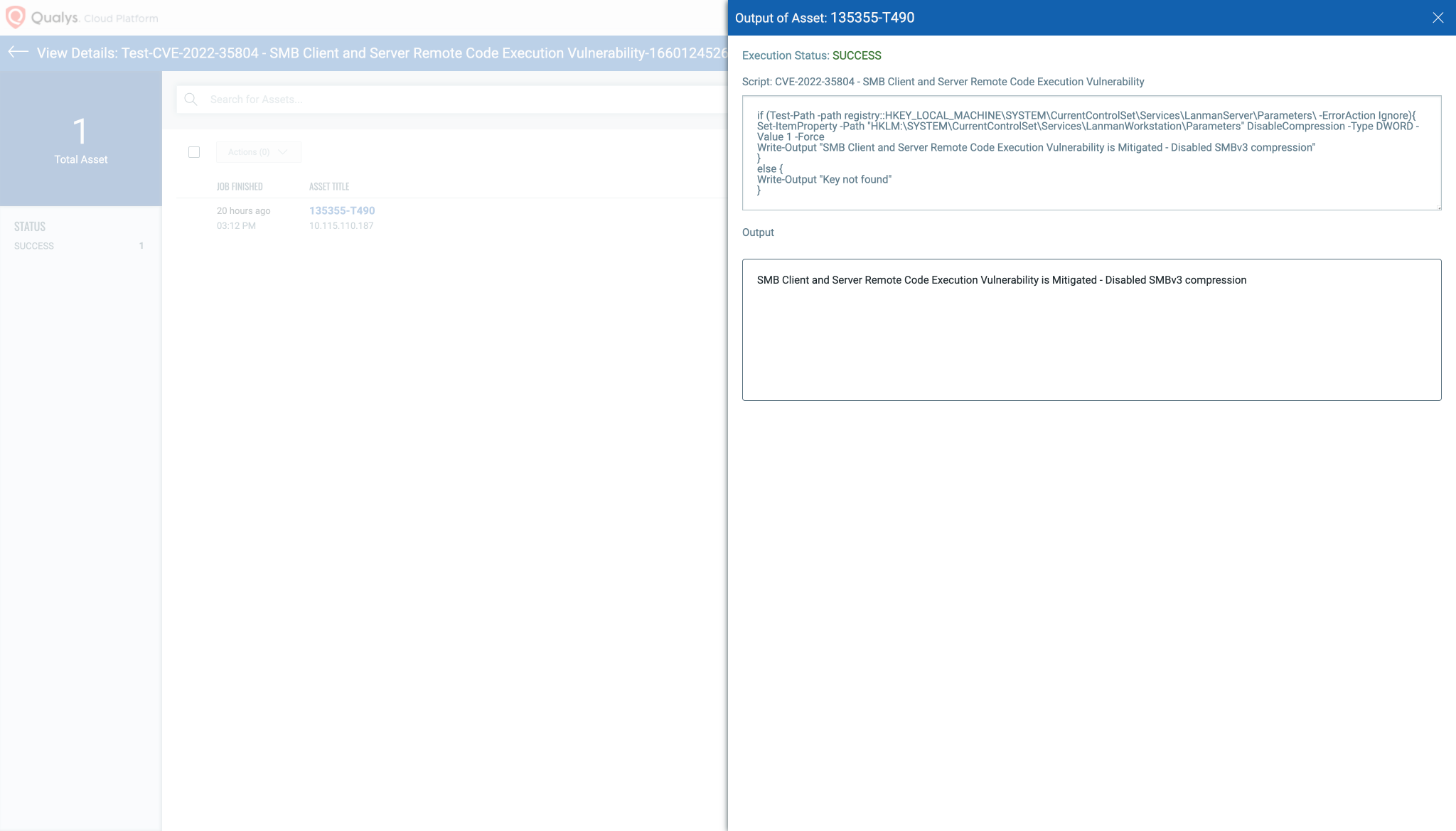 Image source: Qualys
Image source: Qualys
How to undo the workaround:
You can revert the workaround with the following PowerShell command:
Remove-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters” -Name “DisableCompression” -Force
Remove-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” -Name “DisableCompression” -Force
CVE-2022-30133, CVE-2022-35744 – Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability
Script details: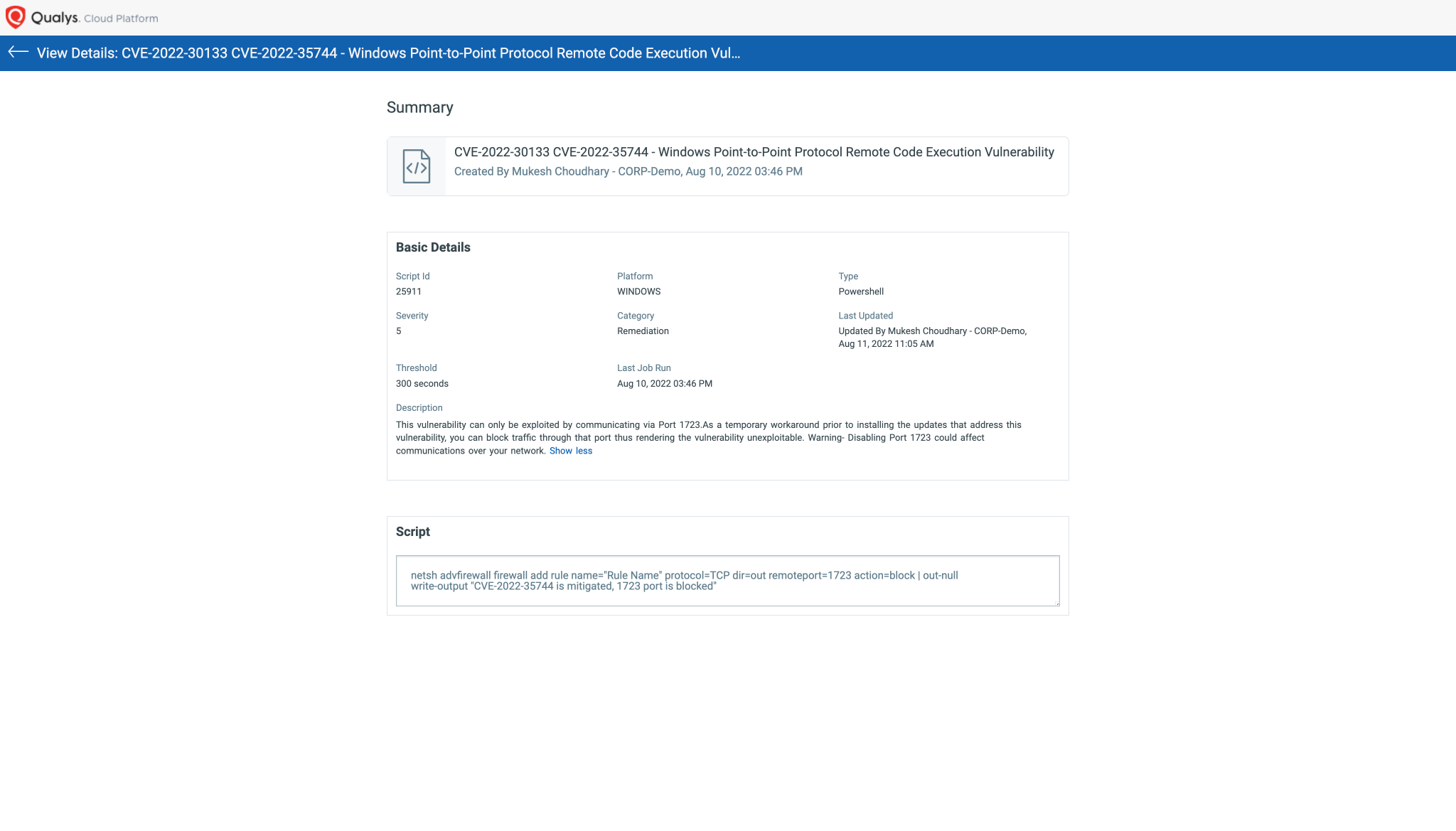 Image source: Qualys
Image source: Qualys
Script output: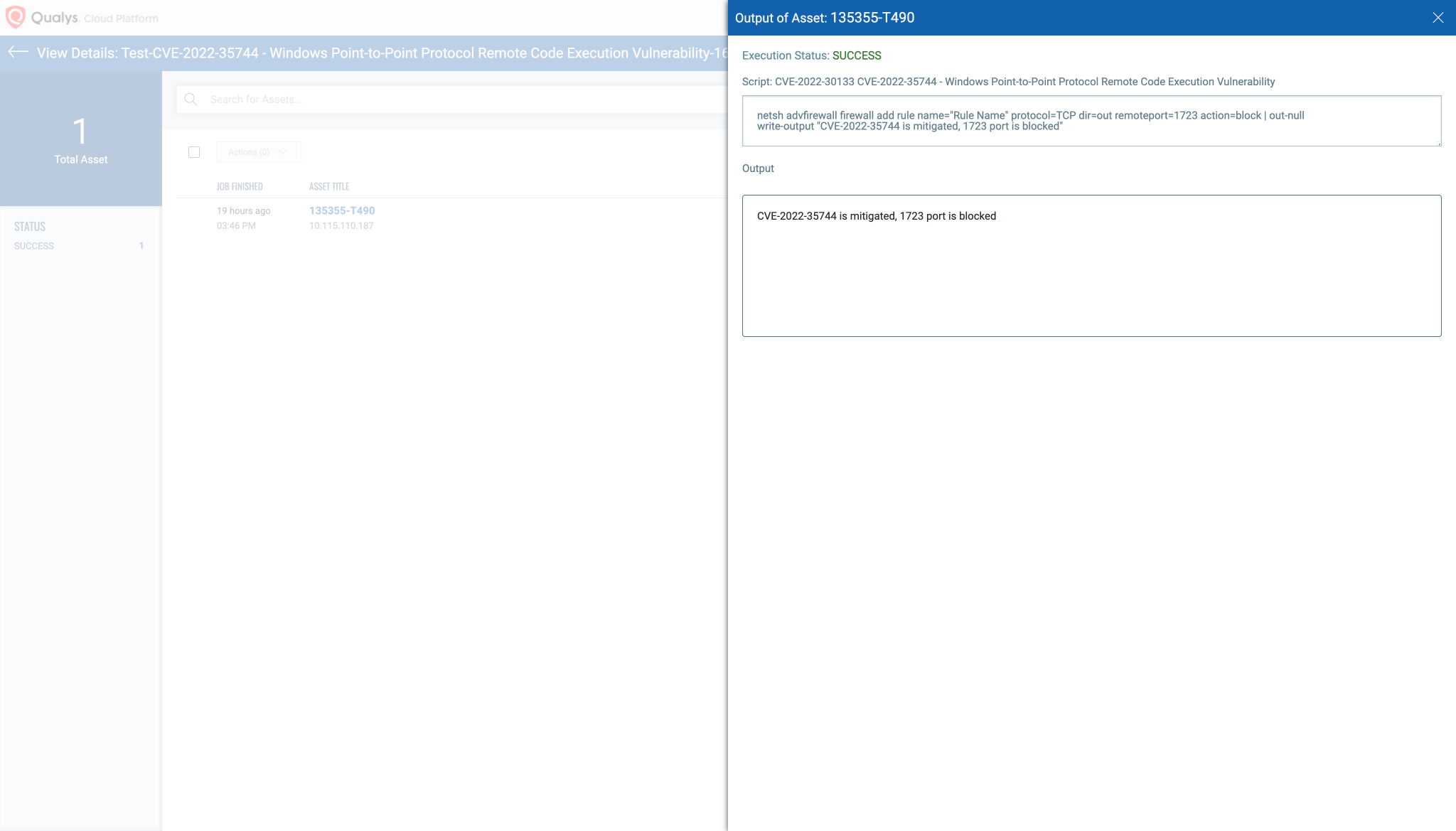 Image source: Qualys
Image source: Qualys
Impact of Workaround:
This vulnerability can only be exploited by communicating via Port 1723. As a temporary workaround prior to installing the updates that address this vulnerability, you can block traffic through that port thus rendering the vulnerability unexploitable.
Warning: Disabling Port 1723 could affect communications over your network.
Visit the August 2022 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110413, 110414, 376813, 50121, 91929, 91931, 91932, 91933, 91934, 91935, 91936 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/releaseNote/2022-Aug
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30134
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34713
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-35794
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-30133
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34691
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-33646
https://support.microsoft.com/en-us/topic/kb5014754-certificate-based-authentication-changes-on-windows-domain-controllers-ad2c23b0-15d8-4340-a468-4d4f3b188f16