Cisco has released multiple security advisories addressing high severity vulnerabilities in the Webex Meeting app (CVE-2022-20863), SD-WAN vManage (CVE-2022-20696), and RV series VPN routers (CVE-2022-20923). The patches include a fix for a vulnerability related to the NVIDIA Data Plane Development Kit (CVE-2022-28199).
As per Cisco’s advisory regarding CVE-2022-20923, the organization “Cisco has not released and will not release software updates to address the vulnerability described in this advisory. Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers have entered the end-of-life process. Customers are encouraged to migrate to Cisco Small Business RV132W, RV160, or RV160W Routers.”
Cisco SD-WAN vManage Software Unauthenticated Access to Messaging Services Vulnerability (CVE-2022-20696)
An unauthenticated, nearby attacker with access to the VPN0 logical network can exploit this vulnerability in the binding configuration of Cisco SD-WAN vManage Software containers to access the messaging service ports on a vulnerable device.
The message server container ports on an impacted system don’t have enough security measures, which leads to this vulnerability. The attacker must be able to send network traffic to interfaces inside the VPN0 logical network in order to take advantage of this vulnerability. Depending on how the device deployment configuration is, this network may be restricted to protect logical or physical nearby networks. On successful exploitation, an attacker can view and inject messages into the messaging service, which can cause configuration changes or cause the system to reload.
This vulnerability does not affect the following Cisco products:
- SD-WAN vEdge Routers
- IOS XE SD-WAN Software
- SD-WAN vEdge Cloud Routers
- SD-WAN vSmart Controller Software
- SD-WAN vBond Orchestrator Software
Workaround
The Cisco SD-WAN vManage Software messaging services use ports 4222, 6222, and 8222, which administrators can prohibit using access control lists (ACLs). Based on the deployment, the following steps can be taken for configuration:
- Configure ACLs on Cisco IOS devices.
- Configure ACLs at the firewall that protects Cisco SD-WAN vManage Software.
Cisco Webex Meetings App Character Interface Manipulation Vulnerability (CVE-2022-20863)
The vulnerability in the Cisco Webex Meetings app can allow an unauthenticated, remote attacker to manipulate links or other content within the messaging interface.
This vulnerability exists because the affected software does not properly handle character rendering. An attacker could exploit this vulnerability by sending messages within the program interface. A successful exploit could give an attacker the ability to modify the display of links or other content within the interface, thus enabling phishing or spoofing attacks.
There are no workarounds released for this vulnerability.
Cisco Small Business Routers IPSec VPN Server Authentication Bypass Vulnerability (CVE-2022-20923)
The Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers’ IPSec VPN Server authentication feature may be vulnerable, allowing an unauthenticated, remote attacker to bypass authentication measures and access the IPSec VPN network.
This vulnerability results from the password validation algorithm’s inappropriate application. By using “crafted credentials” to connect to the VPN from a compromised device, an attacker could exploit this vulnerability. On successful exploitation, the attacker might be able to enter the IPSec VPN network without authentication. Depending on the carefully designed credentials used, the attacker might be able to get access with the same degree of privileges as an administrative user.
To determine if the IPSec VPN Server feature is configured on a device, please follow the steps:
- Log in to the web-based management interface.
- Choose VPN > IPSec VPN Server > Setup.
If the Server Enable check box is selected, the IPSec VPN Server is enabled on the device.
Vulnerability in NVIDIA Data Plane Development Kit Affecting Cisco Products (CVE-2022-28199)
The Data Plane Development Kit (MLNX DPDK) distributed by NVIDIA has a network stack vulnerability, where error recovery is not handled appropriately. This vulnerability could allow a remote attacker to damage data integrity and confidentiality as well as denial of service.
In case of the error condition, the device may either reload or stop receiving traffic, leading to a denial of service (DoS) condition.
This vulnerability does not affect the following Cisco products:
Routing and Switching – Enterprise and Service Provider
- Cloud Services Router 1000V Series
- IOS Software
- IOS XE Software (other than Cisco Catalyst 8000V Edge Software)
- IOS XR Software
- NX-OS Software
Indicator of compromise
If Cisco Catalyst 8000V Edge Software is using the MLX5 driver and it is affected by this vulnerability, administrators would see that traffic is not being received on the interface and rx_errors will increase on the affected interface, as shown in the following example where interface GigabitEthernet2 has been affected:
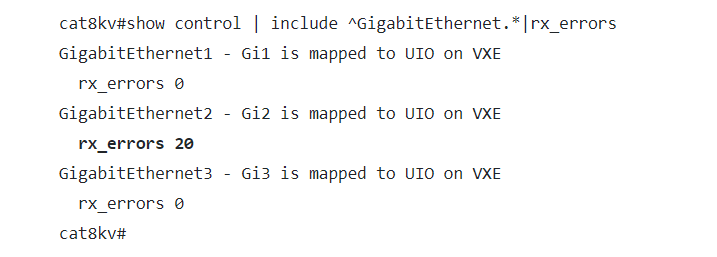
Image source: Cisco advisory
Workaround
There is one recovery mechanism that exists in Cisco Catalyst 8000V Edge Software.
Taking forward from the above example, where GigabitEthernet2 has been affected, the commands in the following example show the recovery technique of shut/no shut:
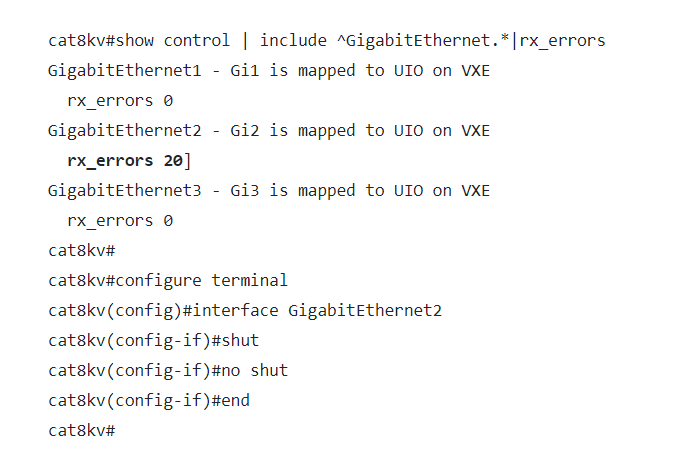
Image source: Cisco advisory
Affected versions
CVE-2022-20696 affects the following versions:
- Cisco SD-WAN vManage versions older than 20.6.4 and 20.9.1
CVE-2022-20863 affects the following versions:
- Cisco Webex App versions older than 42.7
CVE-2022-20923 affects the following products:
- RV130 VPN Router
- RV215W Wireless-N VPN Router
- RV110W Wireless-N VPN Firewall
- RV130W Wireless-N Multifunction VPN Router
CVE‑2022‑28199 affects the following versions:
- Adaptive Security Virtual Appliance
- Cisco Catalyst 8000V Edge Software
- Secure Firewall Threat Defense Virtual (formerly FTDv)
Mitigation
Customers can refer to the following official advisories for information about patching the vulnerabilities:
- Cisco SD-WAN vManage security advisory (cisco-sa-vmanage-msg-serv-AqTup7vs)
- Cisco Webex Meetings App security advisory (cisco-sa-webex-app-qrtO6YC2)
- Cisco Small Business RV series security advisory (cisco-sa-sb-rv-vpnbypass-Cpheup9O)
- NVIDIA Data Plane Development Kit security advisory and cisco-sa-mlx5-jbPCrqD8
Qualys Detection
Qualys customers can scan their devices with QIDs 317220, 376975, and 730609 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://nvidia.custhelp.com/app/answers/detail/a_id/5389
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-mlx5-jbPCrqD8
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-webex-app-qrtO6YC2
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb-rv-vpnbypass-Cpheup9O
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-vmanage-msg-serv-AqTup7vs