A critical severity arbitrary code execution vulnerability, found in the Apache Commons Text library, has been discovered and reported by Alvaro Munoz. Tracked as CVE-2022-42889, this vulnerability has been assigned a CVSS base score of 9.8 and could result in remote code execution applied to untrusted input due to insecure interpolation defaults.
Apache Commons Text is a library that focuses on algorithms working on strings. Apache Commons Text performs the task of variable interpolation, enabling characteristics to be dynamically assessed and expanded. The standard format for interpolation is “${prefix:name}“, where “prefix” is used to locate an instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation.
The vulnerability is being compared to Log4Shell as it is also an Open-source library-level vulnerability that can affect a wide variety of software applications that use the relevant object. However, the initial investigation suggests that the comparison is inappropriate. The flaw differs from Log4Shell (CVE-2021-44228) in which string manipulation is possible from the log message body, which commonly contains untrusted input. Since string interpolation is explicitly intended and well-documented in the relevant method in the Apache Common Text issue, it is far less likely that applications will unintentionally feed in untrusted input without the required validation.
Description
The collection of default Lookup instances contains interpolators that could lead to arbitrary code execution or communication with external servers. Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used.
These lookups are:
- “script” – execute expressions using the JVM script execution engine (javax.script)
- “dns” – resolve dns records
- “url” – load values from urls, including from remote servers
The vulnerability exists in the StringSubstitutor interpolator object. When this object is used with the default interpolators, (StringSubstitutor.createInterpolator()) performs string lookups that may lead to arbitrary code execution.
“If untrusted data flows into the StringSubstitutor.replace() or StringSubstitutor.replaceIn() methods, an attacker will be able to use the ScriptStringLookup to trigger arbitrary code execution”, the researcher mentioned in the blog.
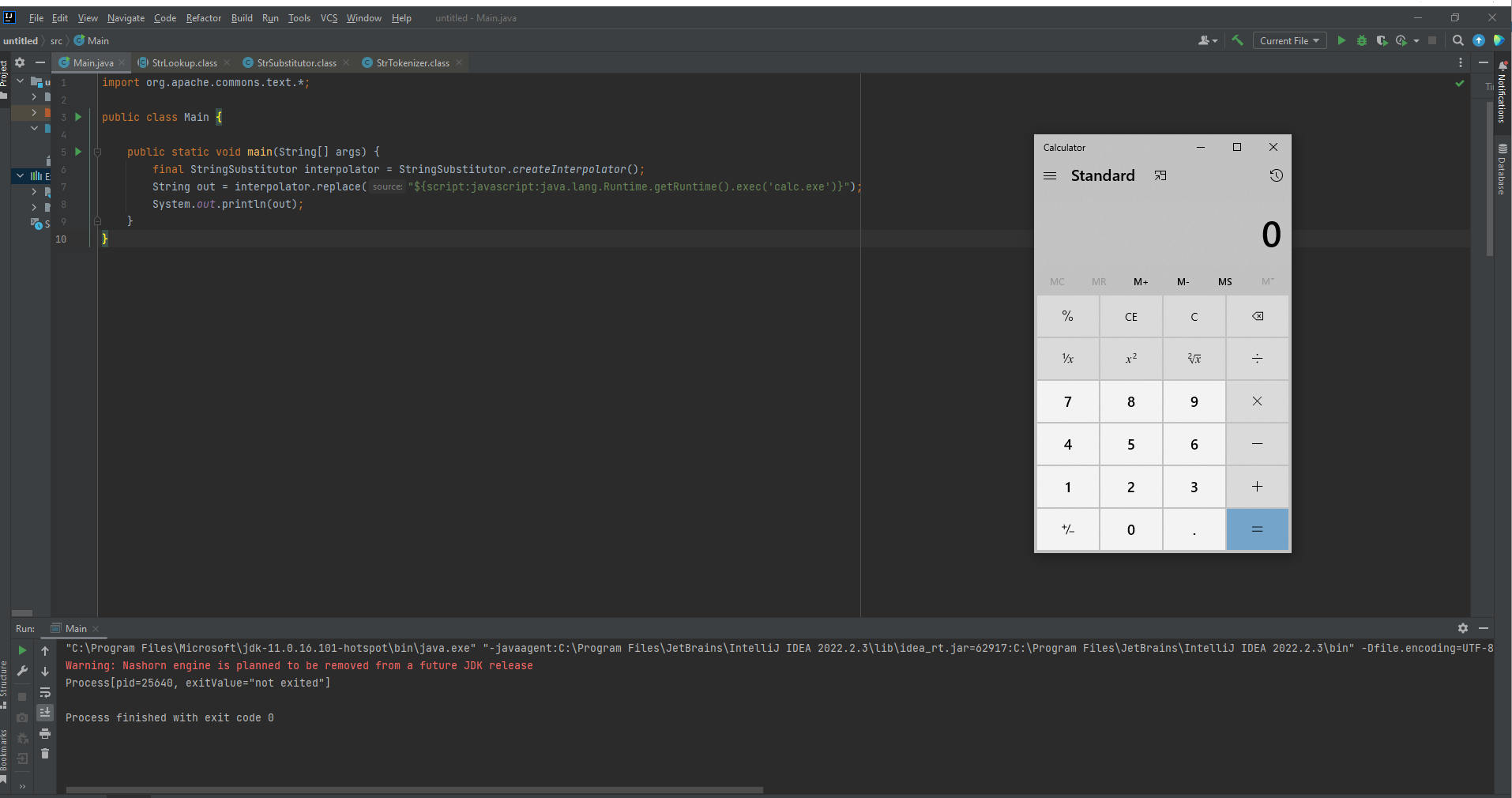 Image Source: Qualys Labs
Image Source: Qualys Labs
Affected Versions
Apache Commons Text versions 1.5 to 1.9 are affected by this vulnerability.
Mitigation
To patch this vulnerability, customers must upgrade to the latest Apache Commons Text version 1.10. For more information, please refer to the Apache Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 377639, 377701, and 988179 to detect vulnerable assets.
The QID 988179 will be available to customers who subscribe to the SCA (Software Composition Analysis) product. Qualys is proactively working on adding coverage for our VM, Cloud Agent, and Container Sensor customers.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://lists.apache.org/thread/n2bd4vdsgkqh2tm14l1wyc3jyol7s1om
https://securitylab.github.com/advisories/GHSL-2022-018_Apache_Commons_Text/