Microsoft has released security updates for 65 new vulnerabilities in its November 2022 Patch Tuesday Edition. The security update also addressed six actively exploited zero-day vulnerabilities. Out of the 65 vulnerabilities, 10 are rated as critical that include privilege elevation, spoofing, remote code execution, and other severe types of vulnerabilities.
This month’s security updates also included a Microsoft Defense in Depth Update (ADV220003). On November 2nd, 2022, Microsoft also released two advisories for OpenSSL 3.x for Azure SDK for C++, C++ Library Manager for Windows (vcpkg), and Microsoft Azure Kubernetes Service (CVE-2022-3602, CVE-2022-3786).
The advisory covers a total of 39 products, features, and roles, including AMD CPU Branch, Network Policy Server (NPS), Open-Source Software, Visual Studio, Windows Advanced Local Procedure Call, Windows ALPC, Windows Group Policy Preference Client, Windows Win32K, and many more.
The vulnerabilities are classified as follows:
- Spoofing Vulnerability: 3
- Denial of Service Vulnerability: 6
- Elevation of Privilege Vulnerability: 27
- Security Feature Bypass Vulnerability: 4
- Information Disclosure Vulnerability: 11
- Remote Code Execution Vulnerability: 16
Actively exploited zero-day vulnerabilities addressed in Patch Tuesday, November 2022 Edition
CVE-2022-41128 – Windows Scripting Languages Remote Code Execution Vulnerability
This vulnerability was discovered by Benoît Sevens and Clément Lecigne of Google’s Threat Analysis Group. This vulnerability affects the JScript9 scripting language. This vulnerability requires a user running a vulnerable version of Windows to connect to a malicious server. An attacker would have to host a specially crafted server share or website. An attacker can exploit this vulnerability by making the users visit the specially crafted server share or websites by an enticement in an email or chat message.
CVE-2022-41091 – Windows Mark of the Web Security Feature Bypass Vulnerability
An attacker can craft a malicious file to evade Mark of the Web (MOTW) defenses that could result in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which relies on MOTW tagging.
The vulnerability can be exploited in the following scenarios:
- In a web-based attack scenario: An attacker could host a malicious website that exploits the security feature bypass.
- In an email or instant message attack scenario: An attacker could send the targeted user a specially crafted .url file designed to exploit the bypass.
- Compromised websites or websites that accept or host user-provided content could contain specially crafted content to exploit the security feature bypass.
CVE-2022-41073 – Windows Print Spooler Elevation of Privilege Vulnerability
The vulnerability was discovered by Microsoft Threat Intelligence Center (MSTIC). On successful exploitation of this vulnerability, an attacker could gain SYSTEM privileges.
CVE-2022-41125 – Windows CNG Key Isolation Service Elevation of Privilege Vulnerability
The vulnerability was discovered by Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC). On successful exploitation of this vulnerability, an attacker could gain SYSTEM privileges.
Microsoft Exchange Server Zero-day Vulnerabilities (CVE-2022-41040 and CVE-2022-41082) (ProxyNotShell)
The vulnerabilities were discovered by the Vietnamese cybersecurity outfit GTSC via the Zero-day initiative.
CVE-2022-41040 is a Server-Side Request Forgery (SSRF) vulnerability. To exploit this vulnerability, an attacker must be authenticated and required to have the ability to run PowerShell in the context of the system.
CVE-2022-41082 allows remote code execution (RCE) when PowerShell is accessible to the attacker. An authenticated attacker could target server accounts for arbitrary or remote code execution. The attacker could try to leverage a network call as an authenticated user to attempt to execute malicious code in the context of the server’s account.
Microsoft has released patches for these vulnerabilities and advised its users to apply the patches. The previously released mitigations are no longer recommended by Microsoft.
Some of the critical vulnerabilities addressed in Patch Tuesday, November 2022 Edition
CVE-2022-38023 – Netlogon RPC Elevation of Privilege Vulnerability
The vulnerability arises in the Netlogon protocol when RPC signing is used instead of RPC sealing. This cryptographic protocol vulnerability in the Windows Netlogon protocol could be exploited by an authenticated attacker when RPC Signing is used instead of RPC Sealing. When RPC Signing is used in place of RPC Sealing, the attacker may be able to take over the service and modify Netlogon protocol traffic to elevate their level of privileges.
CVE-2022-37966 – Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability
The vulnerability was discovered by Tom Tervoort with Secura. This cryptographic protocol vulnerability in RFC 4757 (Kerberos encryption type RC4-HMAC-MD5) and MS-PAC (Privilege Attribute Certificate Data Structure specification) could be exploited by an unauthenticated attacker to bypass security features in a Windows AD environment.
CVE-2022-37967 – Windows Kerberos Elevation of Privilege Vulnerability
On successful exploitation of this vulnerability, an attacker could gain administrator privileges. If the attacker gains control of the service that is allowed for delegation, they can modify the Kerberos PAC to elevate their privileges.
CVE-2022-41080 – Microsoft Exchange Server Elevation of Privilege Vulnerability
This vulnerability was discovered by rskvp93 with VcsLab of Viettel Cyber Security. Technical details of this vulnerability and the exploitation information are unavailable now.
CVE-2022-41118 – Windows Scripting Languages Remote Code Execution Vulnerability
This vulnerability was discovered by Tim Cluff that affects both the JScript9 and Chakra scripting languages. This vulnerability requires a user running a vulnerable version of Windows to connect to a malicious server. An attacker would have to host a specially crafted server share or website. An attacker can exploit this vulnerability by making the users visit the specially crafted server share or websites by an enticement in an email or chat message.
CVE-2022-41088 – Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability
This vulnerability was discovered by Yuki Chen with Cyber KunLun. An attacker is required to win a race condition for exploiting the vulnerability. To exploit this vulnerability, an attacker would need to send a specially crafted malicious PPTP packet to a PPTP server. This could result in remote code execution on the server side.
CVE-2022-41044 – Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability
This vulnerability was discovered by Microsoft’s Windows Servicing and Delivery Group – Network Security and Containers (NSC) Team. An attacker is required to win a race condition for exploiting the vulnerability. An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine.
Evaluating workaround using Qualys Policy Compliance (PC)
CVE-2022-37967 – Windows Kerberos Elevation of Privilege Vulnerability
25167 Status of the ‘KrbtgtFullPacSignature’ setting for the Kerberos
CVE-2022-38023 – Netlogon RPC Elevation of Privilege Vulnerability
25168 Status of the ‘RequireSeal’ setting for the Netlogon Remote Protocol
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation empowers a system administrator to quickly and easily perform configuration updates on your technology infrastructure when the current situation requires the implementation of a vendor-suggested mitigation or workaround.
Try It for Free! Sign up now for a no-cost trial of Qualys Custom Assessment and Remediation
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on vulnerable assets.
Please refer to the Qualys GitHub link to ensure the most current version of a Qualys script is being applied.
CVE-2022-37967 – Windows Kerberos Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.2/10.
Exploitability Assessment: Exploitation More Likely
Refer – https://support.microsoft.com/en-us/topic/kb5020805-how-to-manage-kerberos-protocol-changes-related-to-cve-2022-37967-997e9acc-67c5-48e1-8d0d-190269bf4efb#registry5020805
To help protect your environment and prevent outages, we recommend that you take the following steps:
- Update your Windows domain controllers with a Windows update released on or after November 8, 2022.
- MOVE your Windows domain controllers to Audit mode by using the Registry Key setting section.
- MONITOR events filed during Audit mode to secure your environment.
- ENABLE Enforcement mode to address CVE-2022-37967 in your environment.
NOTE: Step 1 of installing updates released on or after November 8, 2022, will NOT address the security issues in CVE-2022-37967 for Windows devices by default. To fully mitigate the security issue for all devices, you must move to Audit mode (described in Step 2) followed by Enforced mode (described in Step 4) as soon as possible on all Windows domain controllers.
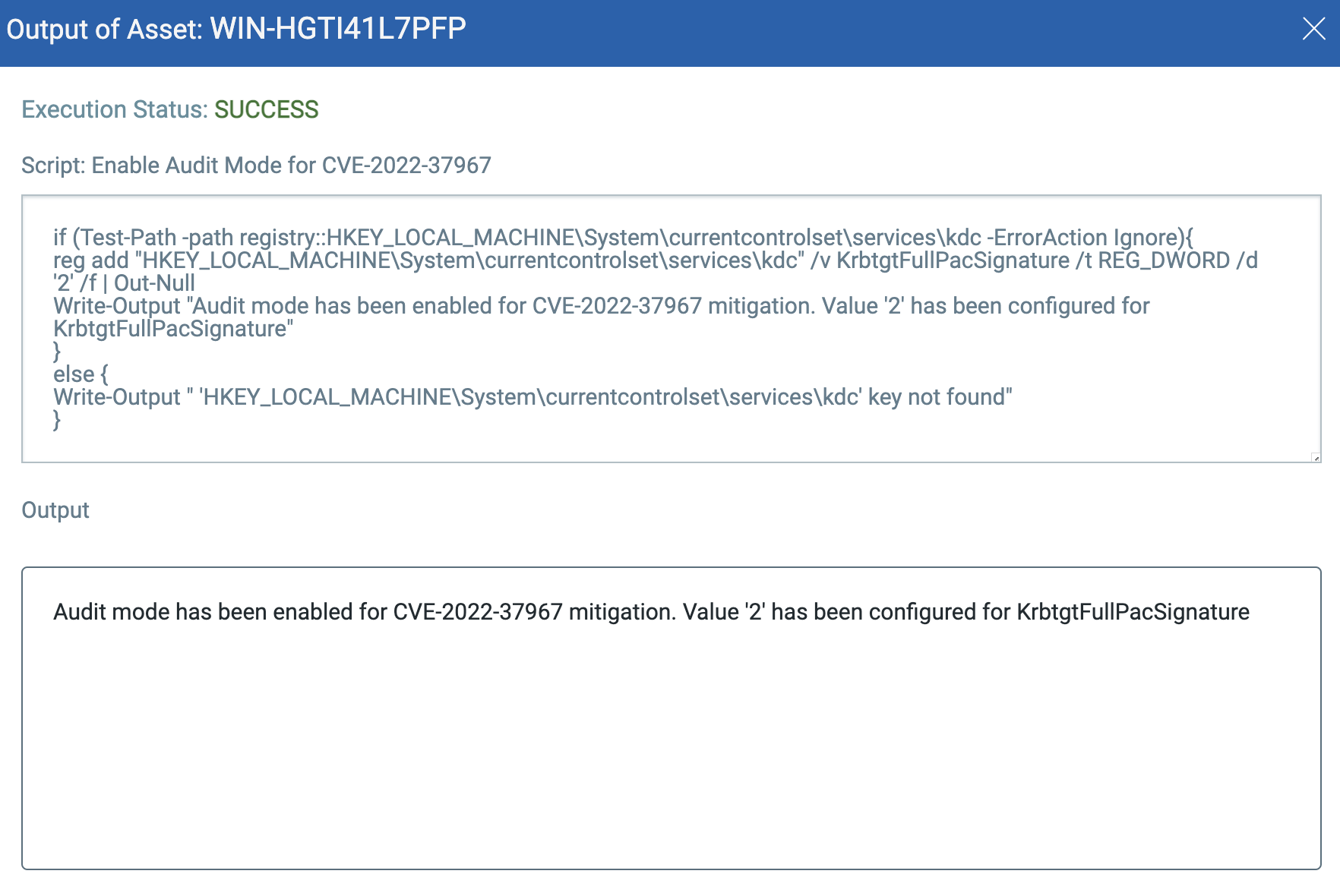
Enable Audit Mode
GitHub Link for Audit Mode
Script
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc -ErrorAction Ignore){
reg add “HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc” /v KrbtgtFullPacSignature /t REG_DWORD /d ‘2’ /f | Out-Null
Write-Output “Audit mode has been enabled for CVE-2022-37967 mitigation. Value ‘2’ has been configured for KrbtgtFullPacSignature”
}
else {
Write-Output ” ‘HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc’ key not found”
}
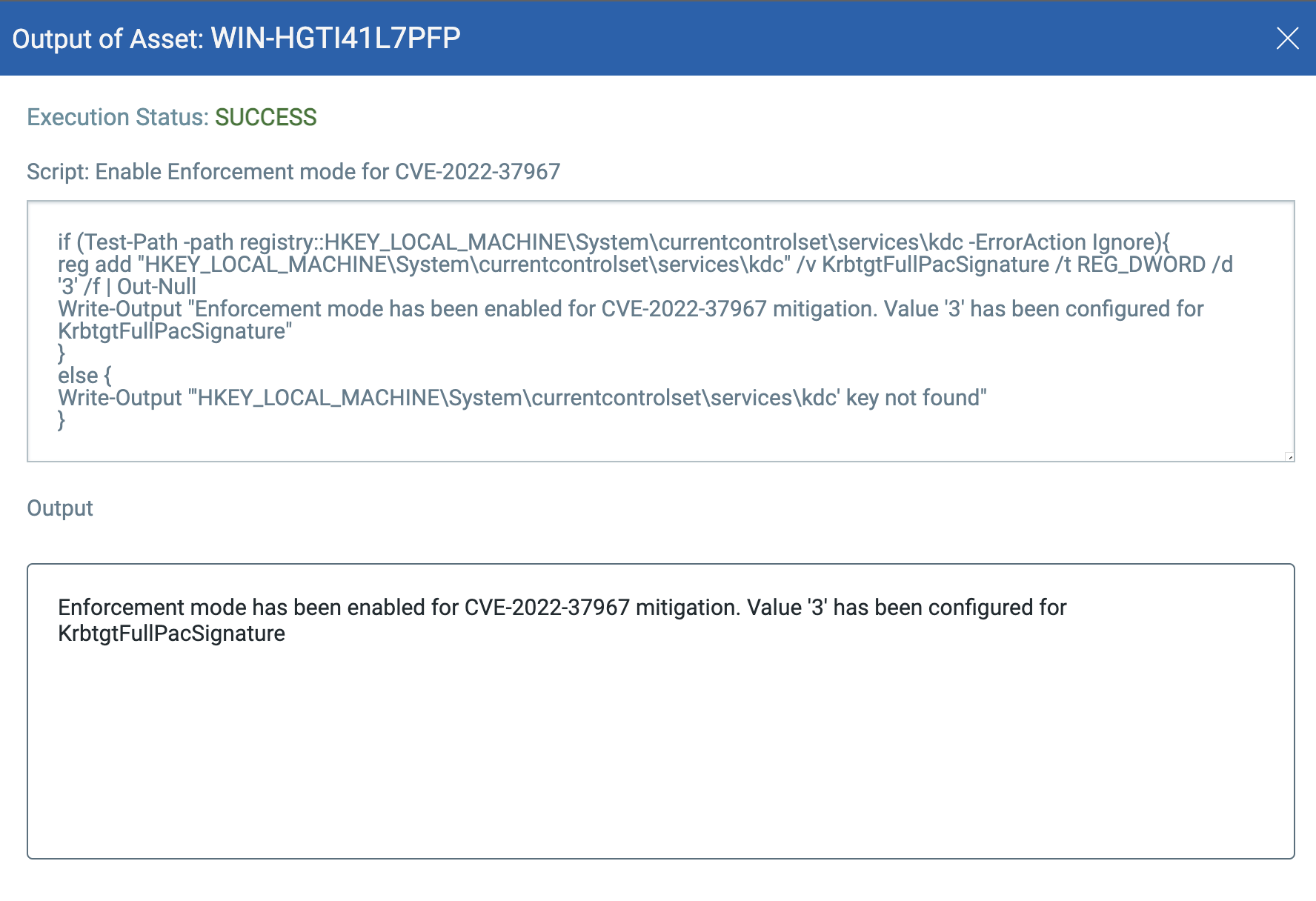
Enable Enforcement Mode
GitHub link for Enforcement Mode
Script
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc -ErrorAction Ignore){
reg add “HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc” /v KrbtgtFullPacSignature /t REG_DWORD /d ‘3’ /f | Out-Null
Write-Output “Enforcement mode has been enabled for CVE-2022-37967 mitigation. Value ‘3’ has been configured for KrbtgtFullPacSignature”
}
else {
Write-Output “‘HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc’ key not found”
}
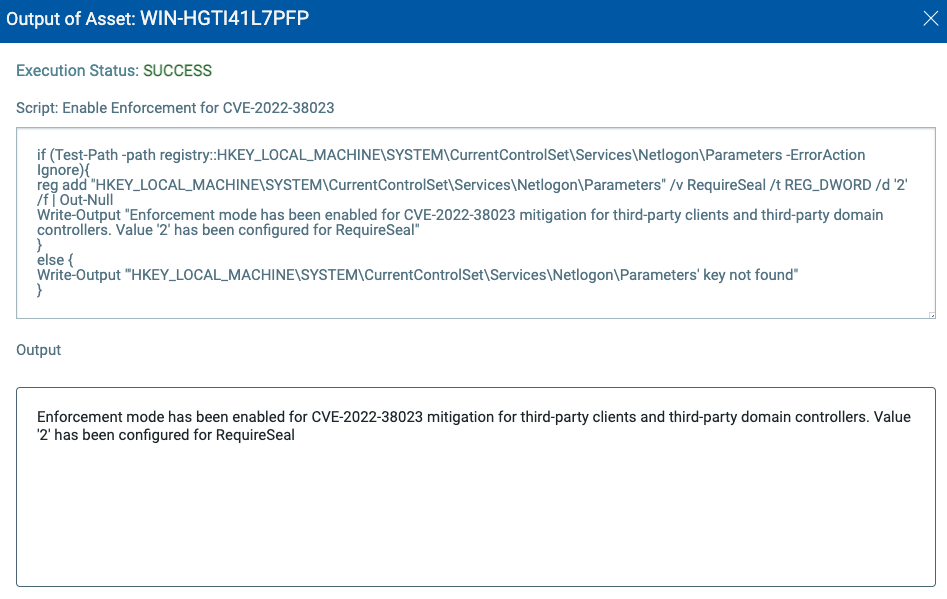
CVE-2022-38023 – Netlogon RPC Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Exploitability Assessment: Exploitation More Likely
NOTE: This update protects Windows devices from CVE-2022-38023 by default. For third-party clients and third-party domain controllers, the update is in Compatibility mode by default and allows vulnerable connections from such clients. Refer to the Registry Key settings section for steps to move to Enforcement mode.
GitHub Link for Enable Enforcement
Script
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters -ErrorAction Ignore){
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters” /v RequireSeal /t REG_DWORD /d ‘2’ /f | Out-Null
Write-Output “Enforcement mode has been enabled for CVE-2022-38023 mitigation for third-party clients and third-party domain controllers. Value ‘2’ has been configured for RequireSeal”
}
else {
Write-Output “‘HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters’ key not found”
}
Visit the November 2022 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 48223, 50122, 50123, 91954, 91956, 91957, 91958, 91959, 91960, 110419, and 110420 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2022-Nov
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41128
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41091
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41073
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41125
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41040
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-38023
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37966
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41080
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41118
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41044
https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1040