CISA has warned security agencies to patch an actively exploited vulnerability in Oracle Access Manager by adding it to its Known Exploited Vulnerabilities Catalog. Tracked as CVE-2021-35587, it is a pre-authentication remote code execution vulnerability in the Oracle Access Manager (OAM). Oracle has rated this vulnerability as critical and provided a CVSS base score of 9.8. Nguyen Jang of VNPT and peterjson from VNG Corporation discovered the vulnerability. CISA has given a deadline of 19th Dec to patch the vulnerability.
Oracle Access Manager comes with risk-aware, end-to-end multifactor authentication (MFA), and single sign-on (SSO) features to integrate identities and systems across the cloud and on-premises. Business organizations widely use this for single sign-on (SSO) as part of the Oracle Fusion Middleware suite.
Description
CVE-2021-35587 is a pre-authentication remote code execution vulnerability in the OpenSSO Agent component of the Oracle Access Manager product, which is widely used for single sign-on (SSO) as part of the Oracle Fusion Middleware suite. This vulnerability can be exploited by an unauthenticated attacker with network access to compromise and completely take over vulnerable Access Manager instances.
The security researcher has mentioned in its blog, “It’s quite easy to access the entry point and exploit the vulnerability, so it’s recommended to apply patch now! It may give the attacker access to the OAM server, to create any user with any privileges, or get code execution in the victim’s server.”
To check if the vulnerable version of Oracle Access Manager is running:
Send a GET request to the vulnerable endpoint: “oam/server/opensso/sessionservice.”
If the page responds with status code 200 ok and “Oracle Corporation,” then the Oracle Access Manager is vulnerable.
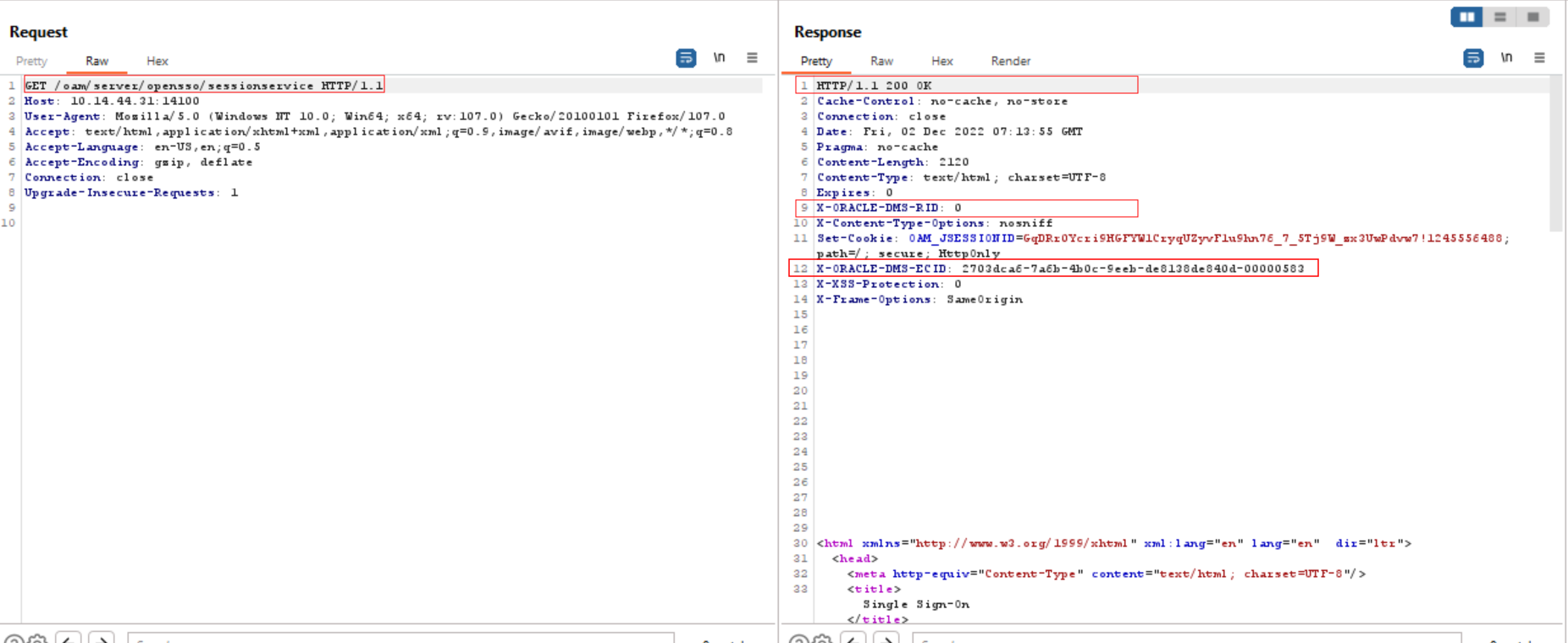
Image Source: Qualys Labs
Affected versions
Oracle Access Manager 11.1.2.3.0, 12.2.1.3.0, and 12.2.1.4.0 are affected by this vulnerability.
Mitigation
Oracle addressed this vulnerability in the Critical Patch Update in January 2022. For more information, please refer to the Oracle Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 730674 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.oracle.com/security-alerts/cpujan2022.html
https://testbnull.medium.com/oracle-access-manager-pre-auth-rce-cve-2021-35587-analysis-1302a4542316