VMware has released a security advisory to address multiple vulnerabilities in its vRealize Log Insight product. The vulnerabilities have CVSSv3 scores ranging from 5.3 to 9.8. The vulnerabilities are being tracked as CVE-2022-31706, CVE-2022-31704, CVE-2022-31710, and CVE-2022-31711.
vRealize Log Insight is used by infrastructure and applications in any environment for intelligent log management. This is a highly scalable log management solution. This tool offers intuitive, actionable dashboards, sophisticated analytics, and broad third-party extensibility across physical, virtual, and cloud environments. This tool helps monitor and maintain extensive data and promotes rapid troubleshooting and root cause analysis.
Description
VMware vRealize Log Insight Broken Access Control Vulnerability (CVE-2022-31704)
The broken access control vulnerability allows an unauthorized user to access restricted resources. Broken access control vulnerabilities are usually exploited by attackers to access files/endpoints that are available for privileged users only. According to the VMware advisory, a malicious actor can exploit this vulnerability in VMware vRealize Log Insight to inject files into the affected appliance’s operating system, which could result in remote code execution.
VMware vRealize Log Insight Directory Traversal Vulnerability (CVE-2022-31706)
The directory traversal vulnerability, also known as path traversal vulnerability, allows an attacker to read arbitrary files on the server that is running a vulnerable application. According to the VMware advisory, an unauthenticated attacker can exploit the vulnerability to inject files into the operating system of an impacted appliance which can result in remote code execution.
VMware vRealize Log Insight contains a Deserialization Vulnerability (CVE-2022-31710)
The deserialization vulnerability in the vRealize Log Insight requires no authentication for exploitation. According to the VMware advisory, an unauthenticated attacker can exploit the vulnerability to trigger the deserialization of untrusted data, which could result in a denial of service.
VMware vRealize Log Insight contains an Information Disclosure Vulnerability (CVE-2022-31711)
Information disclosure vulnerability occurs when a website mistakenly makes sensitive information available to its users. The vulnerability existing in the vRealize Log Insight requires no authentication for exploitation. According to the VMware advisory, a malicious actor can exploit this vulnerability to remotely collect sensitive session and application information.
Vulnerability Analysis
Three of four CVEs addressed in the advisory (CVE-2022-31704, CVE-2022-31706, and CVE-2022-31711) can be combined by an attacker to gain remote code execution as root.
Indicators of compromise (IOCs)
The two indicators of compromise are mentioned below:
- Log entries on the Log Insight server
- Network traffic to or from the Log Insight server
Log entries IOCs
The Log Insight server stores logs in file /var/log/loginsight/runtime.log. The URL and the file name can be different, but they will always be in the format /tmp/fiilename>.pak. An administrator should assess the URL to see if it is a legitimate download URL to identify whether an attack has taken place.
Network Traffic IOCs
An attacker may perform the attack using two network protocols, Apache Thrift and HTTP(S).
An attacker can exploit the Apache Thrift services running on ports 16520 through 16580 on the Log Insight instance. Any unidentified inbound traffic coming to these ports should be monitored to avoid exploitation of the vulnerability.
The Log Insight instance must establish an outbound connection to a remote server to download a malicious payload for the attack to occur. All connections made by the Log Insight instance to unrecognized IP addresses should be further examined to identify whether an attack has occurred.
Proof of Concept (PoC)
CVE-2022-31706 is the directory traversal vulnerability that could allow remote code execution on successful exploitation. The other two CVEs (CVE-2022-31704 and CVE-2022-317011) help exploit this vulnerability.
The workaround KB90635 contains two scripts:
- KB90635.sh
- KB90635_validate.sh
These scripts insert and validate iptables rules restricting access to TCP ports 16520 through 16580.
Vulnerable Ports Analysis
VMware vRealize Log Insight Firewall Recommendations document informs about the use of Apache Thrift RPC protocol in the TCP ports 16520 through 16580.
Apache Thrift is a software framework used for scalable cross-language services development. The software framework combines a software stack with a code generation engine to build services that work efficiently between C++, Java, Python, PHP, and other languages.
The data types and service interfaces are defined in Apache Thrift using a straightforward definition file. The compiler uses that file as input and produces code that can be used to create RPC clients and servers quickly and easily, enabling cross-language communication.
The TCP port 16520 is created by a java application, and the primary class is identified as com.vmware.loginsight.daemon.LogInsightDaemon. The file system shows that the primary class is stored in /usr/lib/loginsight/application/lib/daemon-service-li.jar. The function startThriftServer is responsible for starting the Apache Thrift server. The function startThriftServer analysis shows that the DaemonCommandsHandler class implements the server-side Thrift RPC commands. The file uses various RPC commands, which can be utilized to exploit the vulnerability.
Exploiting the Broken Access Control Vulnerability (CVE-2022-31704)
To exploit this vulnerability, an attacker would have to implement a client for a simple function in DaemonCommandsHandler. The getNodeType can be used as it doesn’t require creating too many Thrift definitions and is easy to test. The command thrift –gen py loginsight.thrift will help create a simple Python client that will call getNodeType, confirming the exploitation of broken access control vulnerability.
Exploiting the Directory Traversal Vulnerability (CVE-2022-31706)
The remotePakDownloadCommand in the requestCommand endpoint of RPC server can be used to reach out to an external URL to download a “Pak” file and place it in /tmp/<filename>.pak. The pakUpgradeCommand invokes the Python script loginsight-pak-upgrade.py to process downloaded files by remotePakDownloadCommand.
Now, the script loginsight-pak-upgrade.py is the point of concern here. The script has a pak file that can be used to apply a system upgrade. The script informs that a Pak file is a tar file containing specific necessary files. Since this script extracts the tar file, an attacker might encode relative paths into the tar file and obtain an arbitrary file write or directory traversal.
Summary
Here are the steps required for an attacker to gain remote code execution:
- Create a Thrift client and using it for unauthenticated access to the Log Insight Thrift server.
- Create a malicious tar file containing a directory traversal using a valid Pak file.
- Using remotePakDownloadCommand to upload the malicious Pak file to /tmp/<filename>.pak.
- Extract the pak file using pakUpgradeCommand.
Affected versions
VMware vRealize Log Insight 8.x prior to 8.10.2 are affected by these vulnerabilities.
Mitigation
VMware has released VMware vRealize Log Insight version 8.10.2 to address these vulnerabilities. For more information about the mitigation, please refer to VMware Security Advisory (VMSA-2023-0001).
Workaround
VMware updated the workaround on 30 January 2023. The article states, “Scripts updated to resolve the issue when executing in a FIPS-enabled environment.” The workaround contains two scripts:
- KB90635.sh
- KB90635_validate.sh
Perform the following steps for each vRealize Log Insight node in the cluster:
- Log into the node as root via SSH (using Putty.exe or any similar SSH Client).
- Upload the “KB90635.sh” script into the “/opt/vmware/bin/” folder using WinSCP or a similar utility.
- Use the command mentioned below to change the file’s permissions and make it executable:
chmod +x /opt/vmware/bin/KB90635.sh
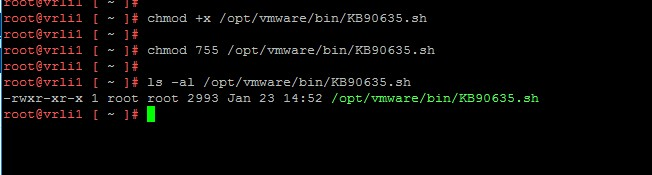
Image source: KB90635
- Execute the script, passing the “setup” argument:
/opt/vmware/bin/KB90635.sh setup
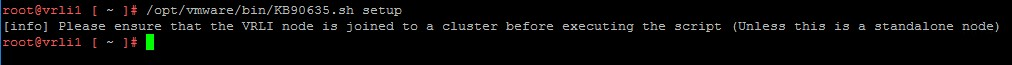 Image source: KB90635
Image source: KB90635
Note: To confirm that the node is already a part of a VRLI cluster, the software prompts the user. Only standalone hosts or nodes that have already been added to a VRLI cluster should run this script. Ensure that the output of the command doesn’t contain any ERROR messages.
- Proceed to the next node in the cluster and follow steps 1-4 on each appliance.
Validation of the workaround
The KB90635 states, “Please ensure that you have executed the steps above on ALL nodes on the cluster before proceeding with the workaround.”
- Log into the node as root via SSH (using Putty.exe or any similar SSH Client)
- Upload the “KB90635_validate.sh” script into the “/opt/vmware/bin/” folder using WinSCP or a similar utility.
- Change the file’s permissions and make it executable by running the command below:
chmod +x /opt/vmware/bin/KB90635_validate.sh
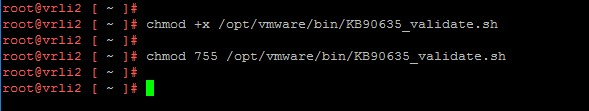
Image source: KB90635
- Execute the validation steps by running the command:
/opt/vmware/bin/KB90635_validate.sh - Ensure that all the VRLI nodes in the cluster are listed in the output.
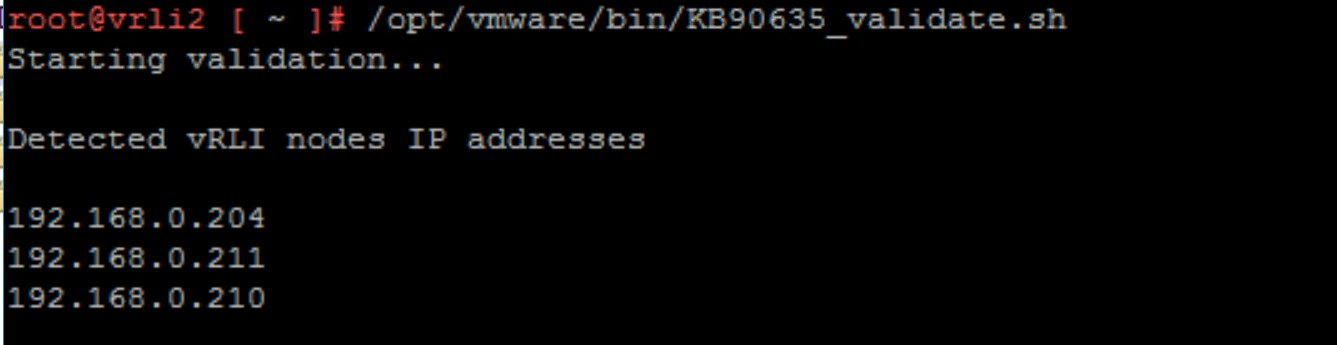
Image source: KB90635
- The script will continue to execute the required steps. Please follow the output and ensure that no errors are reported. Upon successful completion, a message like the one below will be displayed.
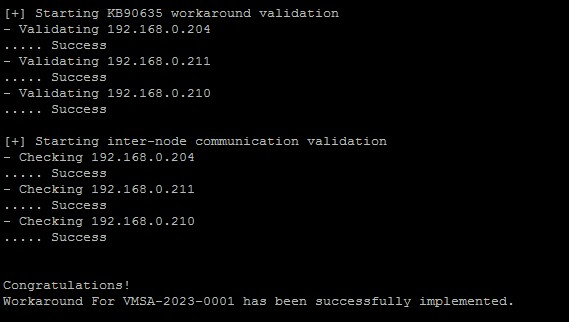
Image source: KB90635
For more information, please refer to KB90635.
Qualys Detection
Qualys customers can scan their devices with QIDs 377932 and 730717 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://thrift.apache.org/
https://kb.vmware.com/s/article/90635
https://www.horizon3.ai/vmware-vrealize-cve-2022-31706-iocs/
https://www.vmware.com/security/advisories/VMSA-2023-0001.html
https://www.horizon3.ai/vmware-vrealize-log-insight-vmsa-2023-0001-technical-deep-dive/
https://docs.vmware.com/en/vRealize-Log-Insight/8.10/com.vmware.log-insight.administration.doc/GUID-14DBC90A-379A-4316-9D76-4850E08437A8.html