Fortra has released a patch for a zero-day vulnerability that affects GoAnywhere Managed File Transfer (MFT). GoAnywhere MFT instances that have the administrative console remotely accessible are affected by this vulnerability. On successful exploitation, the vulnerability will allow an attacker to execute malicious code remotely. The vulnerability is being tracked as CVE-2023-0669.
GoAnywhere MFT is a secure managed file transfer solution that provides smooth data sharing between systems, employees, clients, and business partners. It helps process information from files into XML, EDI, CSV, and JSON databases and offers centralized control with a wide range of security settings and complete audit trails. Deployable on-premises, cloud, and hybrid environments, GoAnywhere MFT, encrypts data following industry standard protocols; for example, HTPPS, OpenPGP, and STFP.
Brian Krebs, an investigative journalist, made the security advisory public, providing information on an “On-Prem Notification/Technical BulletinFeb 1, 2023“, released by the vendor. The advisory was accessible to its users only, which warned of a zero-day vulnerability affecting the GoAnywhere MFT file transfer solution.
Description
The attack vector of the GoAnywhere MFT vulnerability requires an attacker to have access to the administrative console of the application. The administrative console is accessible only from within a private company network, through VPN, or by allow-listed IP addresses (when running in cloud environments, such as Azure or AWS).
The vulnerability affects the administrative interface only. The Web Client interface, which is usually accessible from the public internet, is not vulnerable to this security flaw.
Indicator of compromise (IOC)
Search for the error messages mentioned in the list below to determine if the currently running GoAnywhere MFT instance(s) have been a target of this attack:
- Errors containing the text “/goanywhere/lic/accept”
- Errors containing the text “Error parsing license response”
The following additional error may also confirm unauthorized access:
java.lang.RuntimeException: InvocationTargetException: java.lang.reflect.InvocationTargetException
At
- org.apache.commons.beanutils.BeanComparator.compare(BeanComparator.java:171)
- java.util.PriorityQueue.siftDownUsingComparator(PriorityQueue.java:721)
- java.util.PriorityQueue.siftDown(PriorityQueue.java:687)
- java.util.PriorityQueue.heapify(PriorityQueue.java:736)
- java.util.PriorityQueue.readObject(PriorityQueue.java:796
Please follow the guidelines mentioned below to check for any unauthorized access that may have occurred:
- Evaluate your Audit Logs for suspicious activity. Navigate to Reporting -> Audit Logs -> Administration to investigate Admin User activity and look for:
- Admin Audit Log with a non-existent or disabled super user creating an unexpected account.
Click the Magnifying Glass icon next to the suspicious activity logs to view more details.
- Evaluate your Admin User, and Web User accounts for anything suspicious. Navigate to the Admin Users and Web Users pages and look for the following:
- Unrecognized usernames
Click the Cog icon next to any Username listed and select the View option.
- The Created By details show an unexpected user
If you have an unrecognized username in this field, view the user’s details. If root, administrator, or System created the user and you do not recognize the username, investigate further.
Note: Some legitimate users may show root, administrator, or System in the Created By field. For example, the System will create new users if you use SAML or LDAP Login Methods with automatic account creation enabled.
- The timing of the account creation is suspicious
The Created-On time and date may not be from when you were working with the platform.
Affected Versions
All versions of GoAnywhere MFT prior to version 7.1.2 are affected by this vulnerability.
Mitigation
Customers are recommended to upgrade to the GoAnywhere MFT version 7.1.2. According to the advisory, “This patch version prevents the deserialization of illegitimate data sent to the GoAnywhere server.”
For more information, please refer to GoAnywhere MFT Security Advisory.
Workaround
The advisory provides a workaround for users unable to upgrade to patched versions.
-
- Disable the LicenseResponseServlet:
- On the file system where GoAnywhere MFT is installed, edit the file [install_dir]/adminroot/WEB-INF/web.xml
- In the screenshot below, locate and delete (or comment out) the following servlet and servlet-mapping configuration.
Before:
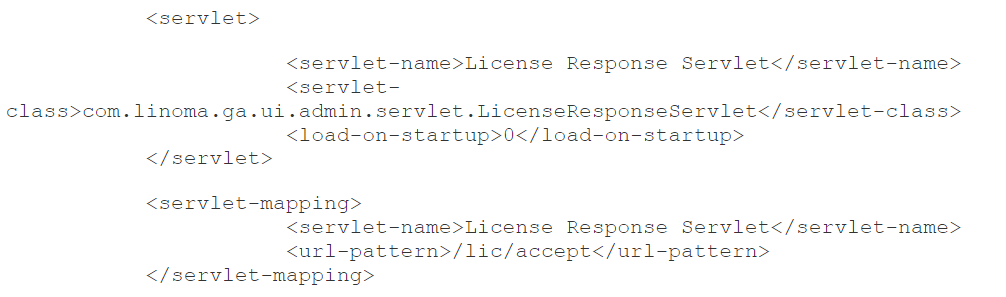
Image source: GoAnywhere security advisory
After: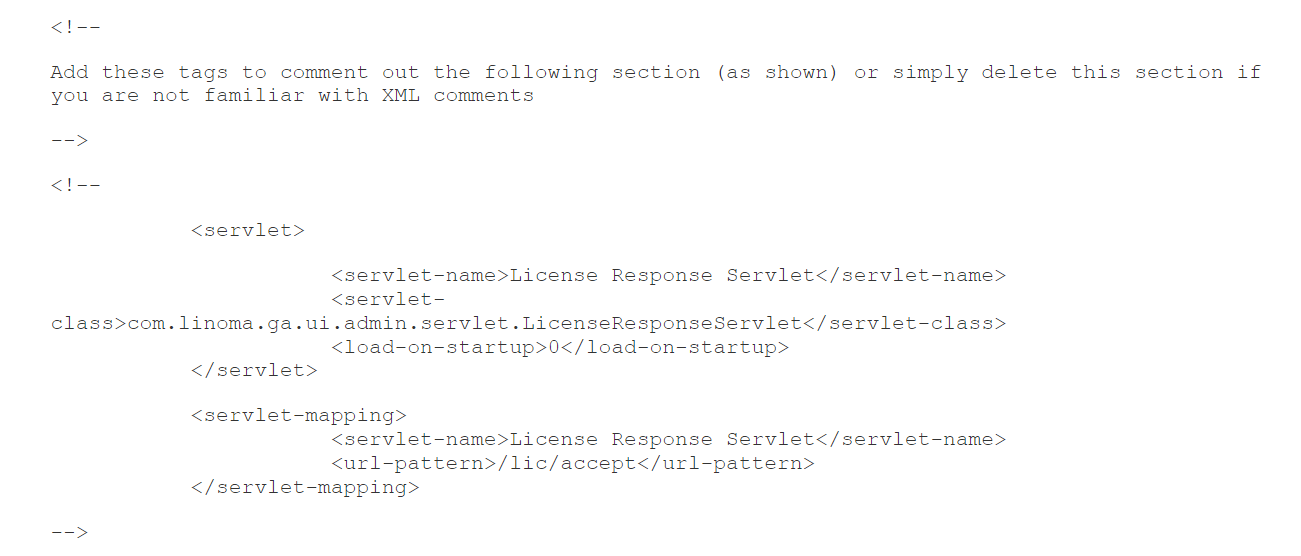
Image source: GoAnywhere security advisory- Restart the GoAnywhere MFT application.
- Disable the LicenseResponseServlet:
- Reduce unauthorized access to your GoAnywhere MFT management interface using network access controls like firewalls.
Qualys Detection
Qualys customers can scan their devices with QID 730720 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://infosec.exchange/@briankrebs/109795710941843934
https://my.goanywhere.com/webclient/ViewSecurityAdvisories.xhtml