PaperCut, a print manager software, has a remote code execution vulnerability that is being actively exploited. CVE-2023-27350 has been rated as critical with a CVSS Base Score of 9.8. Successful exploitation of the vulnerability allows unauthenticated attackers to perform remote code execution to compromise the vulnerable PaperCut application server. The vendor mentioned in the advisory that evidence suggests unpatched servers are exploited in the wild.
The advisory also addressed an authentication bypass vulnerability (CVE-2023-27351) affecting PaperCut NG. The vulnerability has been rated high, with a CVSS Base Score of 8.2. On successful exploitation, an attacker could bypass authentication on the system. There are no instances of active exploitation of this vulnerability publicly available.
Both vulnerabilities were reported to PaperCut by Trend Micro’s Zero Day Initiative ZDI-CAN-18987 and ZDI-CAN-19226.
CISA has added the CVE-2023-27350 to its Known Exploitable Vulnerabilities Catalog and requested users to patch it before May 12th, 2023.
PaperCut is a comprehensive Print management software used in many industries worldwide. To provide a business logic unit for computing user costs and giving end users a web browser interface, PaperCut NG/MF uses the Application Server. A print server is a device that hosts print queues and distributes printer resources to desktop clients and workstations.
As per Shodan, there are more than 1800 internet-exposed PaperCut servers at the time of writing.
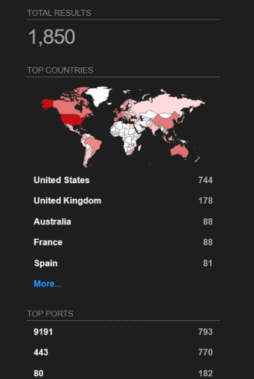
Image Source: Shodan
Description
CVE-2023-27350: PaperCut NG SetupCompleted Improper Access Control Authentication Bypass Vulnerability
The vulnerability exists in the SetupCompleted class that stems from improper access control. There is no authentication required to exploit the vulnerability. On successful exploitation, the vulnerability may allow an attacker to bypass authentication and further perform remote code execution on the target PaperCut NG administrator server.
CVE-2023-27351: PaperCut NG SecurityRequestFilter Authentication Bypass Vulnerability
The information disclosure vulnerability enables a remote, unauthenticated attacker to access user data saved in PaperCut MF/NG, including usernames, email addresses, and sensitive information such as the card numbers linked to the user. An attacker may also access the hashed passwords for internal PaperCut-created users only.
This vulnerability exists in the SecurityRequestFilter class, which arises due to improper implementation of the authentication algorithm.
The exploitation of both vulnerabilities depends on the authentication bypass performed on affected installations that lead to further damage, such as arbitrary code execution in the context of the NT AUTHORITY\SYSTEM account.
Vulnerability Analysis (CVE-2023-27350)
The vulnerable SetupCompleted class is present in the C:\Program Files\PaperCut NG\server\lib\pcng-server-web-19.2.7.jar that can be decompiled to readable Java codes using the command line.
The decompiled class calls the performLogin() function for the Admin user on form submission. Usually, the software only calls this function after a user’s password has been verified during the login process. However, the logic in the SetupCompleted flow unintentionally verifies the anonymous user’s session. This kind of web-based application vulnerability is called Session Puzzling.
The exploitation of CVE-2023-27350
To perform remote code execution, an attacker may exploit printers’ built-in “Scripting” functionality. The functionality allows administrators to develop hooks that help customize printing across the enterprise.
The PaperCut web application uses dynamic form fields based on the last request, which makes it difficult to exploit. An attacker would have to use sessions and individually request each page to access the user interface and ensure the form fields are correctly populated.
Prerequisite for the remote code execution
An authenticated attacker can modify the two settings mentioned below to perform remote code execution:
- print-and-device.script.enabled to Y
- print.script.sandboxed to N
Source: Qualys Threat Research Unit (TRU)
Indicators of Compromise
Several indicators can be seen by navigating to the native application logs in the Logs -> Application Log tab. Most indications will be seen in regular activities, but close attention should be paid to any unusual source IP addresses, times, or a rapid succession of these events.
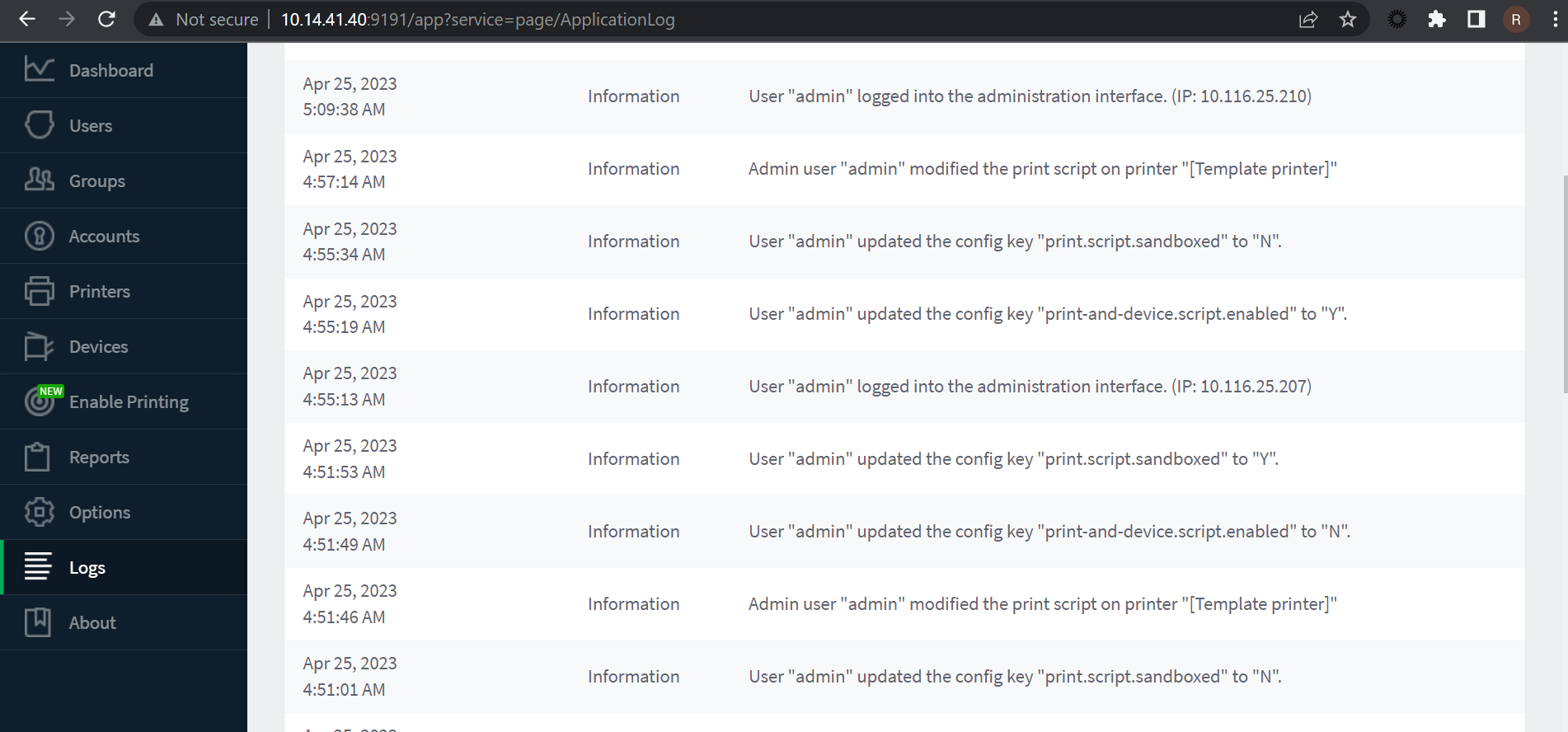 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
CVE-2023-27350
PaperCut MF or NG version 8.0 or later operating on all OS platforms.
CVE-2023-27351
PaperCut MF or NG version 15.0 or later operating on all OS platforms.
Mitigation
Customers are requested to upgrade to the PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11, and 22.0.9 and later.
For more information, please refer to the PaperCut Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 378441 and 730790 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.zerodayinitiative.com/advisories/ZDI-CAN-19226/
https://www.zerodayinitiative.com/advisories/ZDI-CAN-18987/
https://www.papercut.com/kb/Main/PO-1216-and-PO-1219#zdi-can-18987-po-1216
https://www.horizon3.ai/papercut-cve-2023-27350-deep-dive-and-indicators-of-compromise/
https://www.huntress.com/blog/critical-vulnerabilities-in-papercut-print-management-software