VMware addressed an authentication bypass vulnerability in VMware Tools. CVE-2023-20867 may allow attackers to execute privileged commands across Windows, Linux, and PhotonOS (vCenter) guest VMs without authentication.
The vulnerability was discovered by Mandiant. The firm suggests that the cyber espionage group known as UNC3886 has exploited the vulnerability.
VMware Tools is a set of services and modules that enable several features in VMware products. The tools offer better guest operating systems management and seamless user interactions. VMware Tools allow users to customize guest operating systems as a part of the vCenter Server and other VMware products.
CISA has added CVE-2023-20867 to its Known Exploited Vulnerabilities Catalog and urged users to patch it before July 14th, 2023.
Vulnerability Details
The authentication bypass vulnerability exists in the vgauth module of VMware Tools. A fully compromised VMware ESXi host may cause VMware Tools to fail to authenticate host-to-guest operations, which may affect the confidentiality and integrity of the guest virtual machine.
Successful exploitation of the vulnerability may allow an attacker to execute privileged Guest Operations on guest VMs from a compromised ESXi host without the authentication with the guest VM by targeting the authentication check mechanism.
An attacker must first compromise the VMware ESXi host to exploit the vulnerability. An attacker may use vpxuser account credentials along with the command it intended to execute on a guest VM as parameters to a Python script, e.py.
The vpxuser account is created by vCenter Server when the host is first attached and is used for privileged authentication to ESXi. While vCenter Server automatically rotates the password on an interval governed by VirtualCenter.VimPasswordExpirationInDays, also has shell access which can be deactivated in ESXi 8 to reduce the attack surface.
The complete attack path for the exploitation of the vulnerability provided by Mandiant is given below:
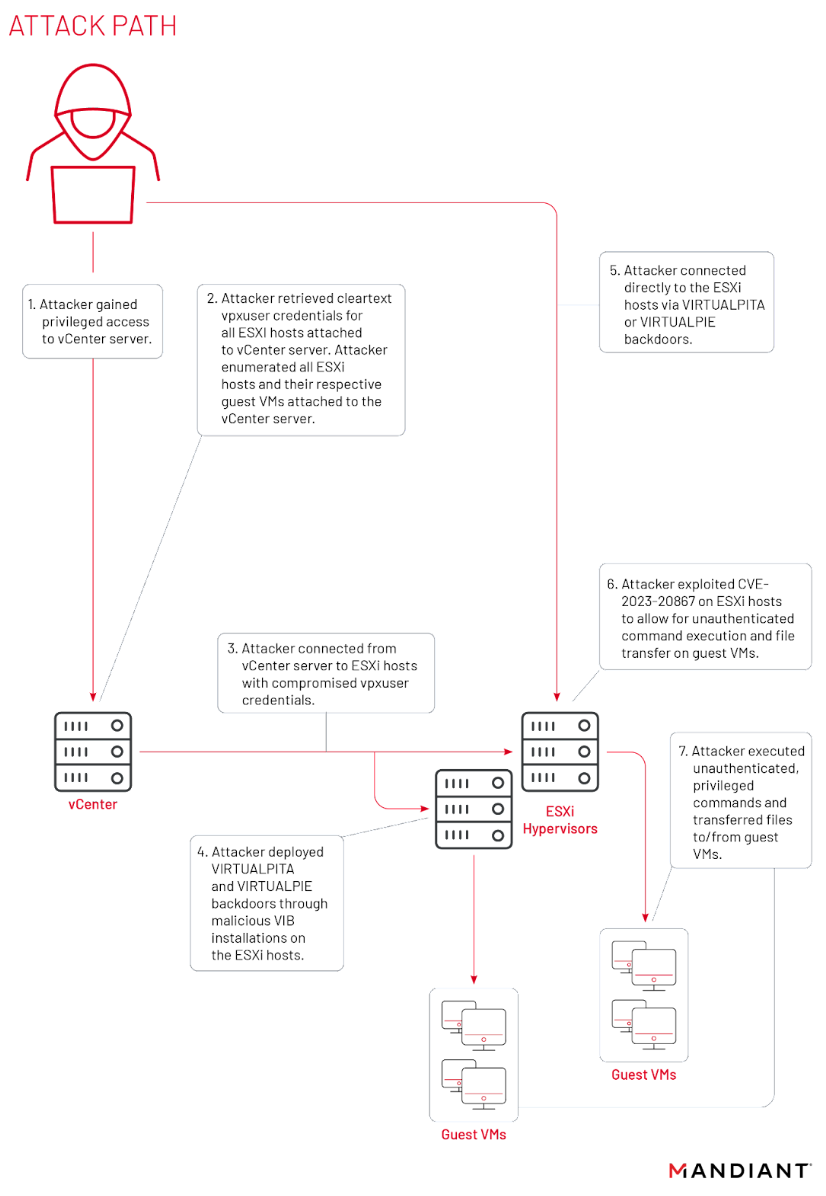
Image Source: Mandiant
Affected Versions
- VMware Tools version 10.3.x
- VMware Tools version 11.x.x
- VMware Tools version 12.x.x prior to 12.2.5
Mitigation
Customers are requested to upgrade to VMware Tools 12.2.5 to patch the vulnerability.
For more information, please refer to the VMware Advisory (VMSA-2023-0013).
Qualys Detection
Qualys customers can scan their devices with QIDs 378578, 754124, and 754102 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.vmware.com/security/advisories/VMSA-2023-0013.html
https://www.mandiant.com/resources/blog/vmware-esxi-zero-day-bypass