Stephen Fewer from Rapid7 has discovered a vulnerability in the Ivanti EPMM. The vulnerability was found when the researchers were investigating another zero-day vulnerability CVE-2023-35078. Successful exploitation of the vulnerability may allow an unauthenticated, remote attacker to access the API and user information.
CVE-2023-35082 has been given the critical severity rating with a CVSS score 10. The advisory states, “This authentication bypass vulnerability may allow an unauthenticated attacker to access restricted functionality or resources of the application.”
CISA has added the CVE-2023-35082 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before February 8, 2024.
Ivanti Endpoint Manager Mobile (EPMM) manages and secures mobile devices. The tool simplifies inventory, configuration, and management of mobile devices. In addition, it helps in creating profiles and enforcing restrictions and security policies.
As per Shodan and Fofa, there are more than 2200 internet-exposed MobileIron Core servers at the time of writing.
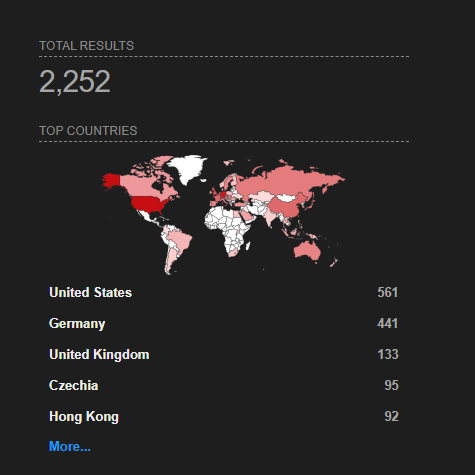
Image Source: Shodan
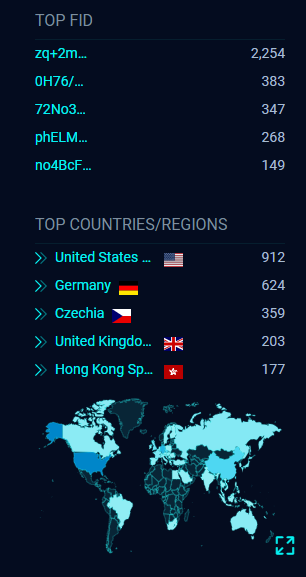
Image Source: Fofa
Vulnerability Description
A remote, unauthenticated attacker can access the API endpoints on a management server by exploiting the vulnerability. An attacker may utilize these API endpoints to perform various tasks, including accessing personally identifiable information (PII) and platform alterations.
CVE-2023-35081 and CVE-2023-35082 can be chained together to write malicious webshell files to the appliance, which the attacker can further execute.
Exploitation of the vulnerability
Ivanti released the hotfix ivanti-security-update-1.0.0-1.noarch.rpm to patch the CVE-2023-35078. The patch blocked the unauthenticated access to the API endpoint. The hotfix prevented the exploit by blocking the /aad/ segment in the URL path used in the exploitation.
An attacker may use the /asfV3/ segment in the URL path instead of the original/aad/ to exploit the CVE-2023-35082.
An attacker may use the endpoint /mifs/asfV3/api/v2/admins/users to access the user’s personal information.
The below screenshot shows that the endpoint /mifs/asfV3/api/v2/ping is accessible without any authentication.
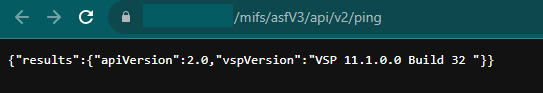
Image Source: Qualys Threat Research Unit
Indicators of Compromise
The log file /var/log/httpd/https-access_log will have an entry showing the request to a targeted API endpoint. The entry contains /mifs/asfV3/api/v2/ in the path with an HTTP response code 200. Blocked exploitation attempts are shown by an HTTP response code of either 401 or 403.
The log file /var/log/httpd/https-request_log will have an entry showing the request to a targeted API endpoint containing /mifs/asfV3/api/v2/ in the path.
Affected versions
This vulnerability impacts Ivanti EPMM versions 11.2 and older.
Mitigation
Customers must upgrade to the Ivanti EPMM version 11.3 to patch the vulnerability.
Note: Ivanti EPMM, formerly MobileIron Core 11.2, has been out of support since March 15, 2022.
Please refer to the Ivanti Security Advisory for more information.
Qualys Detection
Qualys customers can scan their devices with QID 730864 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.rapid7.com/blog/post/2023/08/02/cve-2023-35082-mobileiron-core-unauthenticated-api-access-vulnerability/
https://forums.ivanti.com/s/article/CVE-2023-35082-Remote-Unauthenticated-API-Access-Vulnerability-in-MobileIron-Core-11-2-and-older?language=en_US