Security researchers at Horizon3.ai have discovered two path traversal vulnerabilities in PapertCut NG/MF application servers. An attacker with direct IP address access may chain these vulnerabilities to read and write arbitrary files. CVE-2023-39143 has been rated with a CVSS score of 8.4
PaperCut is a comprehensive Print management software used in many industries worldwide. To provide a business logic unit for computing user costs and giving end users a web browser interface, PaperCut NG/MF uses the Application Server. A print server is a device that hosts print queues and distributes printer resources to desktop clients and workstations.
In April, PaperCut patched two vulnerabilities in the same product:
- CVE-2023-27350, remote code execution vulnerability
- CVE-2023–27351, authentication bypass vulnerability
As per Shodan, there are more than 7600 internet-exposed PaperCut servers at the time of writing.
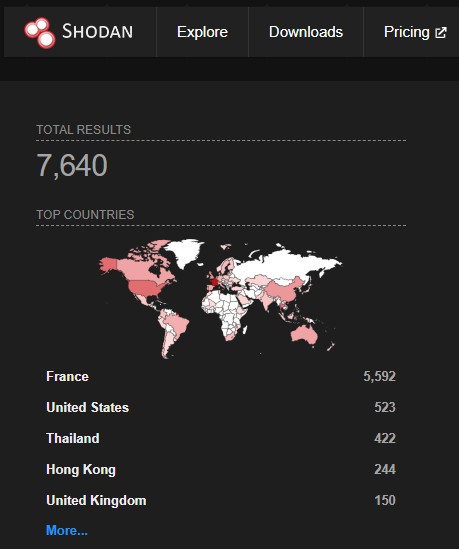
Image Source: Shodan
Vulnerability Details
The vulnerability may allow an unauthenticated attacker to read, delete, and upload arbitrary files to the PaperCut MF/NG application server. The vulnerability may result in remote code execution in specific configurations.
The issue primarily affects PaperCut servers running on Windows. When the external device integration feature is enabled, file upload that results in remote code execution is available. With some PaperCut installations, such as PaperCut NG Commercial Edition or PaperCut MF, this parameter is activated by default.
Research revealed that most PaperCut installations are running on Windows with the external device integration setting enabled.
Exploitation
The exploitation of the vulnerability requires multiple flaws to be chained together. Successful exploitation of the vulnerability would result in compromising a server.
A user may check if their server is vulnerable or not by running the command curl -k -v –head “http://<ip>:<port>/custom-report-example/..\..\..\deployment\sharp\icons\home-app.png”.
A 200 response indicates the server is vulnerable and running on Windows.
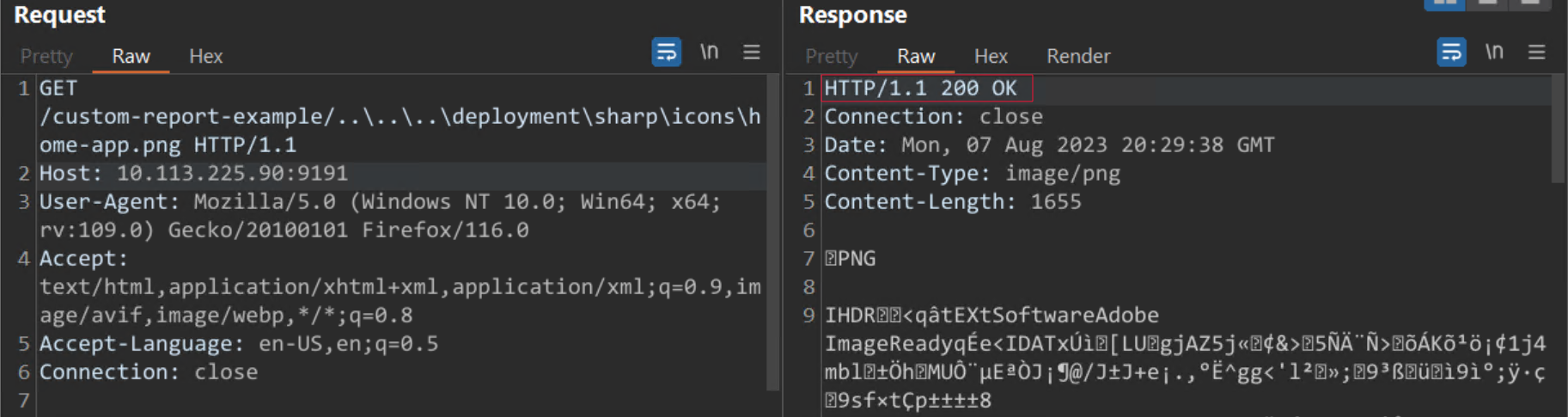
Image Source: Qualys Threat Research Unit (TRU)
A 404 response indicates the server is either patched or not running on Windows.
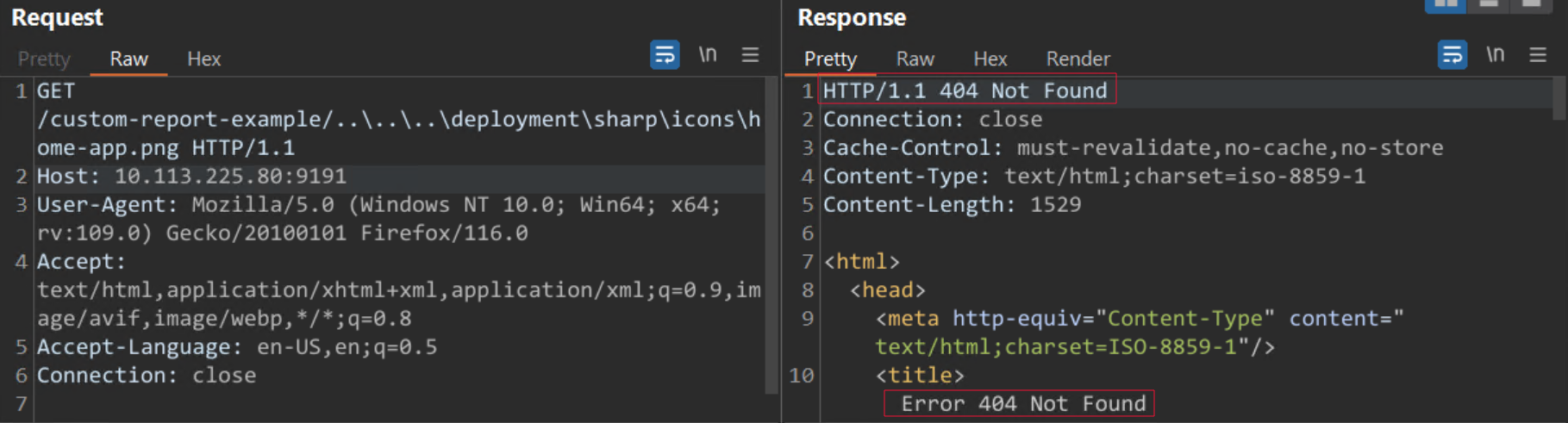
Image Source: Qualys Threat Research Unit (TRU)
Affected versions
The vulnerability affects the PaperCut NG/MF versions before 22.1.3 working on Windows platforms only.
Mitigation
Customers must upgrade to the PaperCut MF/NG version 22.1.3 or later.
For more information, please refer to the PaperCut Security Bulletin.
Qualys Detection
Qualys customers can scan their devices with QIDs 378740 and 730865 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.papercut.com/kb/Main/SecurityBulletinJuly2023/
https://www.horizon3.ai/cve-2023-39143-papercut-path-traversal-file-upload-rce-vulnerability/