Microsoft released its October edition of Patch Tuesday! In this month’s updates, Microsoft has addressed 105 vulnerabilities in different products, features, and roles. Let’s take a look at the updates in detail.
Microsoft Patch Tuesday for October 2023
Microsoft has addressed three zero-day vulnerabilities in this month’s updates. 13 of these 105 vulnerabilities are rated as Critical and 91 as Important. Microsoft has released patches to address one vulnerability related to Microsoft Edge (Chromium-based) in this month’s Patch Tuesday Edition.
Microsoft Patch Tuesday, October edition includes updates for vulnerabilities in Microsoft Office and Components, Windows RDP, Windows Message Queuing, Azure SDK, Microsoft Dynamics, SQL Server, Azure Real Time Operating System, Azure, Windows IKE Extension, Windows Win32K, Microsoft Exchange Server, Skype for Business, Windows Client/Server Runtime Subsystem, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The October 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 1 | Important: 1 |
| Denial of Service Vulnerability | 17 | Critical: 1 Important: 16 |
| Elevation of Privilege Vulnerability | 26 | Important: 26 |
| Information Disclosure Vulnerability | 12 | Important: 12 |
| Security Feature Bypass Vulnerability | 3 | Important: 3 |
| Remote Code Execution Vulnerability | 45 | Critical: 12 Important: 33 |
Zero-day Vulnerability Patched in October Patch Tuesday Edition
MITRE: CVE-2023-44487 HTTP/2 Rapid Reset Attack
Microsoft has addressed the new “HTTP/2 Rapid Reset” zero-day DDoS attack method, which has been extensively exploited since August. The vulnerability exists in the HTTP/2’s stream cancellation feature. An attacker may exploit this vulnerability to repeatedly send and cancel requests, resulting in a DDoS condition.
There is no “fix” for the method other than rate limiting or blocking the protocol, as the feature is part of the HTTP/2 standard. In the advisory, Microsoft has given workaround to mitigate the vulnerability.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before October 31, 2023.
CVE-2023-41763: Skype for Business Elevation of Privilege Vulnerability
Skype for Business is an enterprise software application that is used for instant messaging and video calling. The software can be used with the on-premises Skype for Business Server software and a software-as-a-service version offered as part of the 365 suite.
An attacker could exploit this vulnerability by making a specially crafted network call to the target server. Successful exploitation of the vulnerability may allow an attacker to parse an HTTP request to an arbitrary address that may disclose IP addresses, port numbers, or both to the attacker. In some cases, successful exploitation may expose sensitive information that could provide access to internal networks.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before October 31, 2023.
CVE-2023-36563: Microsoft WordPad Information Disclosure Vulnerability
Microsoft WordPad is a basic text-editing app used to create and edit files, insert pictures, and add links to other files. The word processor software was included with Windows 95 and, later, until Windows 11.
An attacker must log on to the system and run a specially crafted application to exploit the vulnerability. An attacker must also convince a user to click a malicious link and open the specially crafted file.
Successful exploitation of this vulnerability could allow an attacker to disclose NTLM hashes. The NTLM hashes are encoded by converting the user’s password into a 16-byte key using an MD4 hash function. The key is divided into two halves of 8 bytes. The key is used as input to three rounds of DES encryption that generates a 16-byte output representing the NTLM hash.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before October 31, 2023.
Other Critical Severity Vulnerabilities Patched in October Patch Tuesday Edition
CVE-2023-35349: Microsoft Message Queuing Remote Code Execution Vulnerability
Message Queuing (MSMQ) is a protocol developed by Microsoft to ensure reliable communication between Windows computers across different networks, even when a host is temporarily not connected (by maintaining a message queue of undelivered messages).
Successful exploitation of the vulnerability may allow an attacker to perform remote code execution on the target server.
CVE-2023-36697: Microsoft Message Queuing Remote Code Execution Vulnerability
To exploit this vulnerability, an attacker must convince a user on the target machine to connect to a malicious server or compromise a legitimate MSMQ server host and make it run as a malicious server. Successful exploitation of this vulnerability could allow an authenticated domain user to execute code on the target server remotely.
CVE-2023-36718: Microsoft Virtual Trusted Platform Module Remote Code Execution Vulnerability
The Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto processor that is intended to carry out cryptographic operations.
An attacker must perform complex memory-shaping techniques to attempt an attack. To escape the virtual machine, the attacker must be authenticated as a guest mode user. Successful exploitation of the vulnerability could lead to a contained execution environment escape.
CVE-2023-36566: Microsoft Common Data Model SDK Denial of Service Vulnerability
Microsoft Common Data Model is built upon a rich, extensible metadata definition system that allows users to describe and share semantically enhanced data types and structured tags. The tool also helps capture valuable business insight, which can be integrated with heterogeneous data to deliver actionable intelligence.
An authenticated attacker may trigger this vulnerability without any admin or other elevated privileges required.
CVE-2023-41765, CVE-2023-41767, CVE-2023-41768, CVE-2023-41769, CVE-2023-41770, CVE-2023-41771, CVE-2023-41773, CVE-2023-41774, CVE-2023-38166 – Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
Layer 2 Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used mainly by Internet Service Providers and Virtual Private Networks (VPNs). L2TP is one of the protocols that help ensure security and privacy by enabling a tunnel for Layer 2 traffic over a Layer 3 network.
To exploit these vulnerabilities, an attacker is required to win a race condition. An unauthenticated attacker could send a specially crafted connection request to a RAS server and perform remote code execution on the RAS server machine.
Other Microsoft Vulnerability Highlights
- CVE-2023-36780 is a remote code execution vulnerability in Skype for Business. The vulnerability exists in PowerShell when exposed through Microsoft Exchange or Skype. To exploit this vulnerability, an attacker must be granted an administrative role in the Skype for Business Control Panel. Successful exploitation of the vulnerability would allow an attacker to perform remote code execution on the Skype for Business Server backend.
- CVE-2023-36778 is a remote code execution vulnerability in Microsoft Exchange Server. An attacker must have LAN access and credentials for a valid Exchange user to exploit this vulnerability. An authenticated attacker who is on the same intranet as the Exchange server may perform remote code execution via a PowerShell remoting session.
- CVE-2023-36713 is an information disclosure vulnerability in the Windows Common Log File System Driver. Successful exploitation of the vulnerability would allow an attacker to read small portions of heap memory potentially.
- CVE-2023-36594 and CVE-2023-38159 are elevation of privilege vulnerabilities in the Microsoft Graphics Component. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-36731, CVE-2023-36732, CVE-2023-36743, CVE-2023-36776, and CVE-2023-41772 are elevation of privilege vulnerabilities in Win32k. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows IIS, Microsoft QUIC, Windows HTML Platform, Windows TCP/IP, Azure DevOps, Microsoft WordPad, Microsoft Windows Search Component, Microsoft Common Data Model SDK, Windows Deployment Services, Windows Kernel, Microsoft WDAC OLE DB provider for SQL, Windows Mark of the Web (MOTW), Windows Active Template Library, Microsoft Graphics Component, Windows Remote Procedure Call, Windows Named Pipe File System, Windows Resilient File System (ReFS), Windows Microsoft DirectMusic, Windows DHCP Server, Windows Setup Files Cleanup, Windows AllJoyn API, Microsoft Windows Media Foundation, Windows Runtime C++ Template Library, Windows Common Log File System Driver, Windows TPM, Windows Virtual Trusted Platform Module, Windows Mixed Reality Developer Tools, Windows Error Reporting, Active Directory Domain Services, Windows Container Manager Service, Windows Power Management Service, Windows NT OS Kernel, Windows Layer 2 Tunneling Protocol, and Client Server Run-time Subsystem (CSRSS).
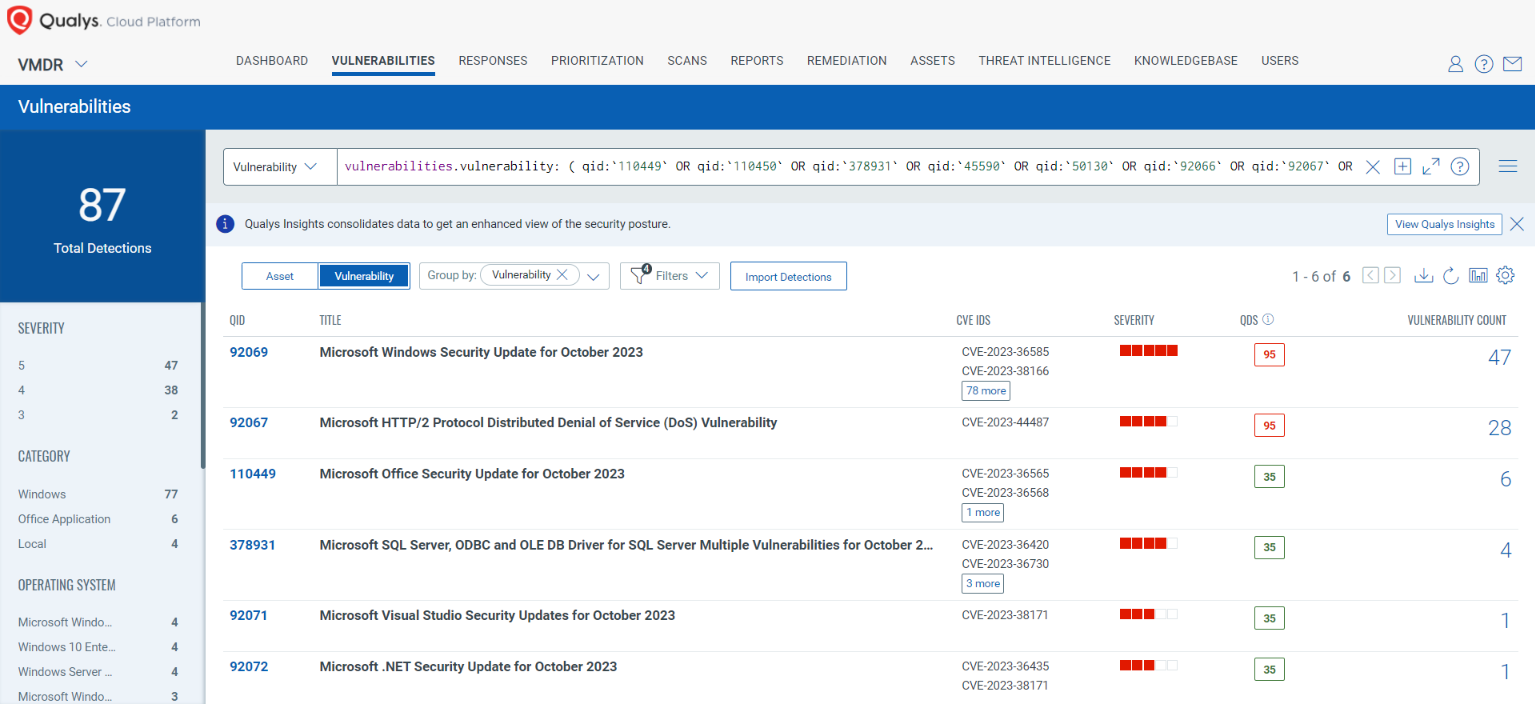
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110449` OR qid:`110450` OR qid:`378931` OR qid:`45590` OR qid:`50130` OR qid:`92066` OR qid:`92067` OR qid:`92068` OR qid:`92069` OR qid:`92070` OR qid:`92071` OR qid:`92072` )
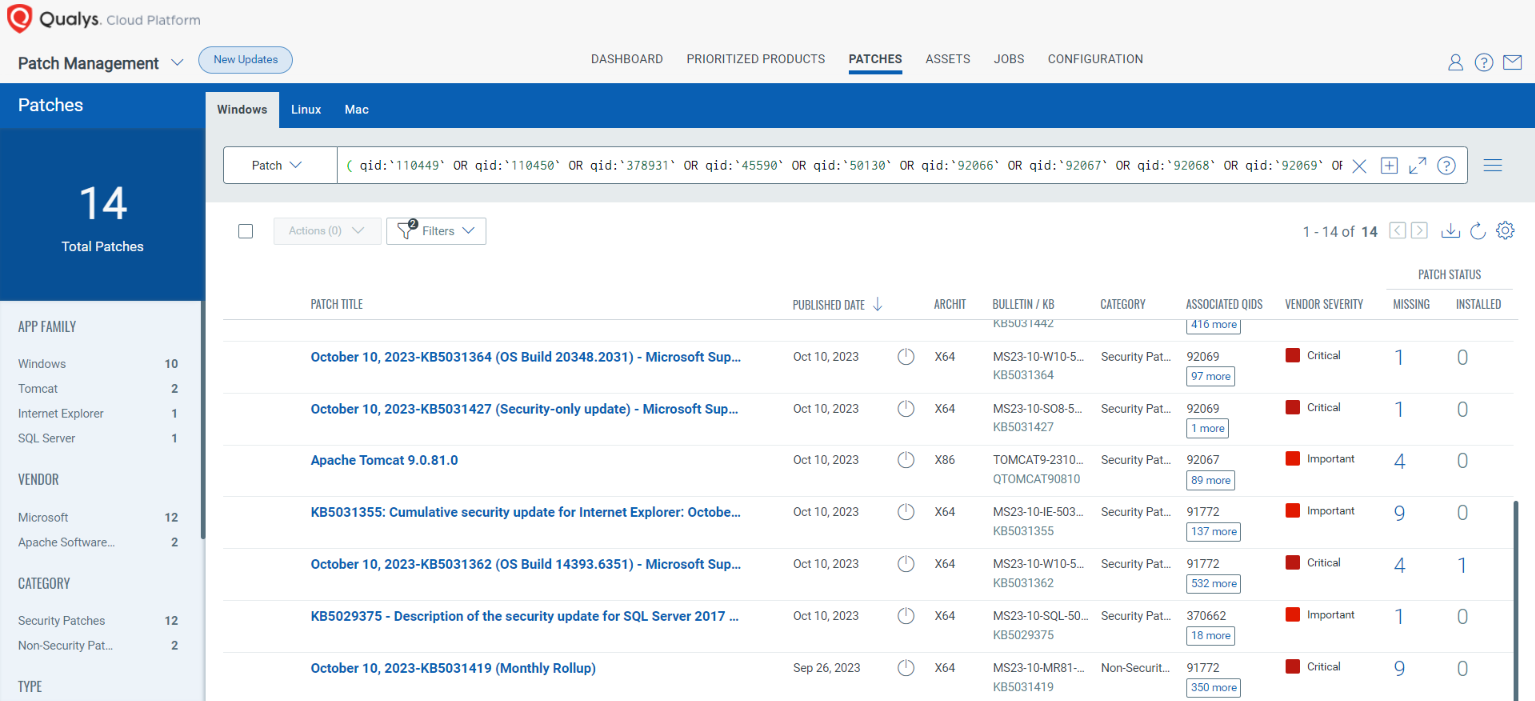
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110449` OR qid:`110450` OR qid:`378931` OR qid:`45590` OR qid:`50130` OR qid:`92066` OR qid:`92067` OR qid:`92068` OR qid:`92069` OR qid:`92070` OR qid:`92071` OR qid:`92072` )
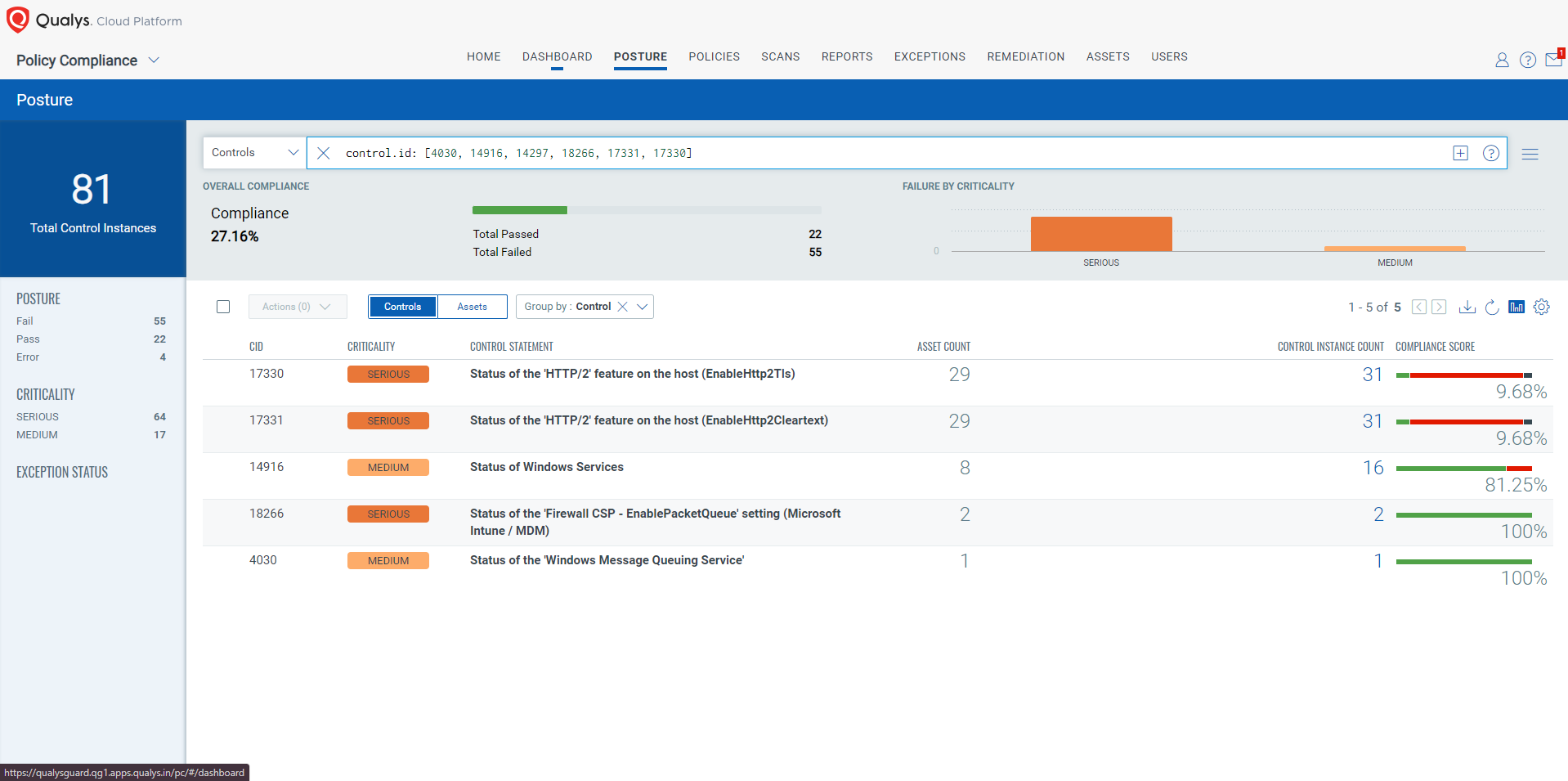
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now; these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-44487: HTTP/2 Rapid Reset Attack
This vulnerability has a CVSS:3.1
Policy Compliance Control IDs (CIDs):
- 17331 Status of the ‘HTTP/2’ feature on the host (EnableHttp2Cleartext)
- 17330 Status of the ‘HTTP/2’ feature on the host (EnableHttp2Tls)
CVE-2023-36603: Windows TCP/IP Denial of Service Vulnerability
This vulnerability has a CVSS:3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
- 18266 Status of the ‘Firewall CSP – EnablePacketQueue’ setting (Microsoft Intune / MDM)
CVE-2023-36591, CVE-2023-36578, CVE-2023-36575, CVE-2023-36571, CVE-2023-35349, CVE-2023-36574, CVE-2023-36590, CVE-2023-36573, CVE-2023-36583, CVE-2023-36570, CVE-2023-36572, CVE-2023-36582, CVE-2023-36589, CVE-2023-36593, CVE-2023-36592 – Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 7.3 / 6.4
Policy Compliance Control IDs (CIDs):
- 4030 Status of the ‘Windows Message Queuing Service’
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030, 14916, 14297, 18266, 17331, 17330]
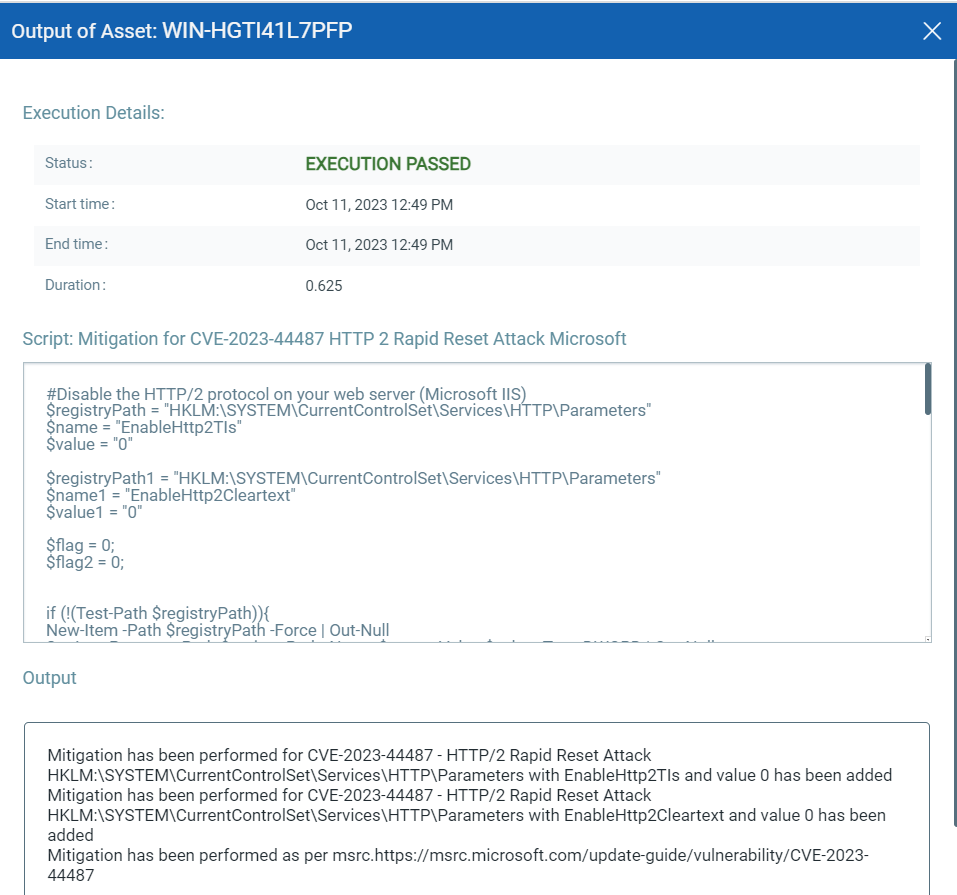
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
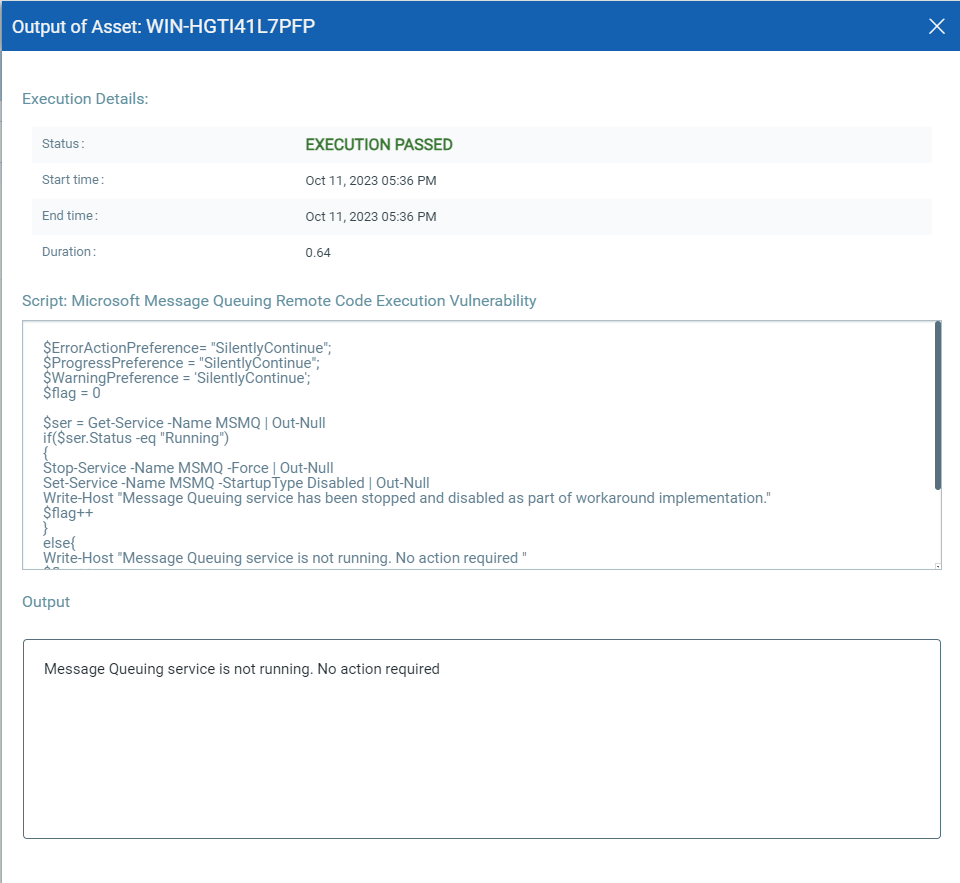
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-44487: HTTP/2 Rapid Reset Attack
CVE-2023-36591, CVE-2023-36578, CVE-2023-36575, CVE-2023-36571, CVE-2023-35349, CVE-2023-36574, CVE-2023-36590, CVE-2023-36573, CVE-2023-36583, CVE-2023-36570, CVE-2023-36572, CVE-2023-36582, CVE-2023-36589, CVE-2023-36593, CVE-2023-36592 – Microsoft Message Queuing Remote Code Execution Vulnerability
Visit the October 2023 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110449, 110450, 378931, 45590, 50130, 92066, 92067, 92068, 92069, 92070, 92071, and 92072 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/
https://msrc.microsoft.com/update-guide/releaseNote/2023-Oct
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-44487
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-41763
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-36563
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-35349
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-36697
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-36718
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-36566
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41765
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41767
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41768
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41769
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41770
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41771
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41773
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-41774
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-38166