Apache Struts, an open-source Model-View-Controller (MVC) framework, is vulnerable to a critical vulnerability that may lead to remote code execution. Tracked as CVE-2023-50164, the vulnerability has been addressed with security updates released by Apache.
Apache Struts helps build sophisticated, contemporary Java web apps. It is expandable through plugin architecture, prioritizes convention over configuration, and comes with AJAX, REST, and JSON plugins.
Vulnerability Details
The vulnerability exists in the framework’s handling of file upload parameters. An unauthenticated, remote attacker may exploit the flaw to perform unauthorized path traversal. Successful exploitation of the vulnerability may allow an attacker to navigate the server’s directory structure and upload a malicious file that can lead to remote code execution.
The Qualys Threat Research Unit has recreated the issue and tested it on the vulnerable version successfully.
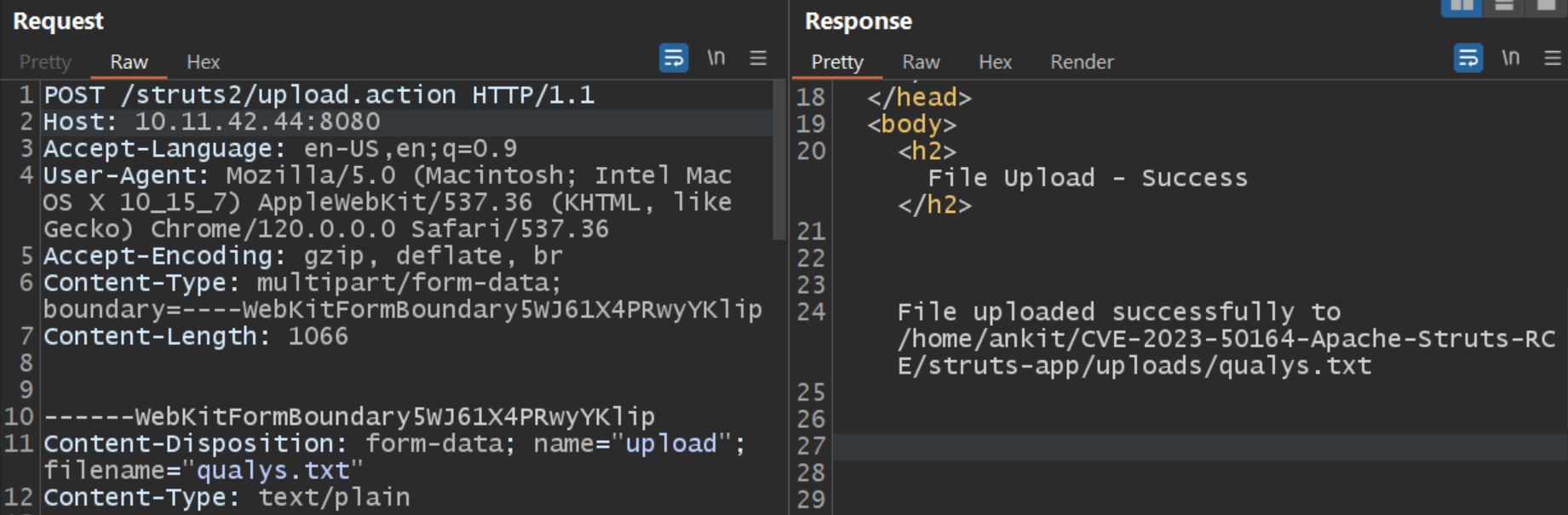
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
- Apache Struts 2.0.0 through 2.5.32
- Apache Struts 6.0.0 through 6.3.0.1
Mitigation
Customers must upgrade to Apache Struts 2.5.33, 6.3.0.2, or later to patch the vulnerability.
Please refer to the Apache Struts2 Security Advisory for more information.
Qualys Detection
Qualys customers can scan their devices with QIDs 379106, 379107, 731026, and 996137 to detect vulnerable assets. The QID 996137 will be available to customers who subscribe to the SCA (Software Composition Analysis) product.
The authenticated QID 379106 retrieves the Tomcat location from the Tomcat server authentication record and searches for the struts-core.x.jar file under subdirectories. It extracts the version from a .jar file and compares it with vulnerable Struts versions.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://cwiki.apache.org/confluence/display/WW/S2-066
https://www.openwall.com/lists/oss-security/2023/12/07/1
https://lists.apache.org/thread/yh09b3fkf6vz5d6jdgrlvmg60lfwtqhj