Microsoft has wrapped up the year with fewer security updates released in its Patch Tuesday, December 2023 edition. We invite you to join us to review and discuss the details of these security updates and patches.
Microsoft Patch Tuesday for December 2023
In this month’s Patch Tuesday edition, Microsoft has addressed 42 vulnerabilities. This month’s updates include four Critical and 34 Important severity vulnerabilities. Microsoft has also included eight Microsoft Edge (Chromium-based) vulnerabilities in the updates patched earlier this month. In this month’s updates, Microsoft has addressed only one vulnerability known to be exploited in the wild.
Microsoft Patch Tuesday, December edition includes updates for vulnerabilities in Microsoft Office and Components, Windows Win32K, Windows Kernel, Microsoft Bluetooth Driver, Windows DHCP Server, Windows ODBC Driver, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), and Spoofing.
The December 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 5 | Critical: 1 Important: 4 |
| Denial of Service Vulnerability | 5 | Important: 5 |
| Elevation of Privilege Vulnerability | 11 | Important: 11 |
| Information Disclosure Vulnerability | 8 | Important: 8 |
| Remote Code Execution Vulnerability | 8 | Critical: 3 Important: 5 |
Zero-day Vulnerability Patched in December Patch Tuesday Edition
AMD: CVE-2023-20588 AMD Speculative Leaks Security Notice
The vulnerability was first discovered in August 2023. As per AMD Security Bulletin, “This is a division-by-zero error on some AMD processors that can potentially return speculative data resulting in loss of confidentiality.”
Microsoft has addressed the flaw in the Security Update Guide because the latest builds of Windows enable mitigation and provide protection against the vulnerability.
Other Critical Severity Vulnerabilities Patched in December Patch Tuesday Edition
CVE-2023-36019: Microsoft Power Platform Connector Spoofing Vulnerability
Microsoft Power Platform connector is a proxy or wrapper around an API that allows users to communicate with the underlying service of Microsoft Power Automate, Microsoft Power Apps, and Azure Logic Apps. It enables users to link their accounts and create apps and processes using a library of prebuilt actions and triggers.
To exploit the vulnerability, an attacker must convince a user to click on a specially crafted URL that can be compromised by the attacker.
CVE-2023-35630: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
Internet Connection Sharing (ICS) is a Windows service that enables one Internet-connected computer to share its Internet connection with other computers on a local area network (LAN).
An attacker can only attack systems connected to the same network segment as them. Attacks cannot be carried out across multiple networks (such as a WAN). To exploit this vulnerability, an attacker must modify an option->length field in a DHCPv6 DHCPV6_MESSAGE_INFORMATION_REQUEST input message.
CVE-2023-35641: Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
An attacker can only attack systems connected to the same network segment as them. Attacks cannot be carried out across multiple networks (for example, a WAN). An attacker may exploit this vulnerability by sending a specially crafted DHCP message to a server that runs the Internet Connection Sharing service.
CVE-2023-35628: Windows MSHTML Platform Remote Code Execution Vulnerability
Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still relevant today and are being patched by Microsoft.
An attacker may exploit the vulnerability by sending a specially crafted email, which triggers when it is retrieved and processed by the Outlook client. The vulnerability can be exploited even BEFORE the email is viewed in the Preview Pane. An attacker may use complex memory-shaping techniques to attack affected instances.
Other Microsoft Vulnerability Highlights
- CVE-2023-35633 is an elevation of privilege vulnerability in Windows Kernel. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-35632 is an elevation of privilege vulnerability in Windows Ancillary Function Driver (AFD) for Winsock. The driver connects a computer to the internet. An attacker who successfully exploits the vulnerability may gain SYSTEM privileges.
- CVE-2023-36011 and CVE-2023-35631 are elevation of privilege vulnerabilities in Win32k. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-35644 is an elevation of privilege vulnerability in Windows Sysmain Service. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-36005 is an elevation of privilege vulnerability in Windows Telephony Server. An attacker must win a race condition to exploit the vulnerability. Successful exploitation of the vulnerability may allow an attacker to execute code in the security context of the “NT AUTHORITY\Network Service” account.
- CVE-2023-36391 is an elevation of privilege vulnerability in the Local Security Authority Subsystem Service. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-36696 is an elevation of privilege vulnerability in Windows Cloud Files Mini Filter Driver. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Media, Microsoft Edge (Chromium-based), Microsoft Office Outlook, Microsoft Dynamics, Microsoft Windows DNS, Azure Connected Machine Agent, Azure Machine Learning, Windows MSHTML Platform, Windows USB Mass Storage Class Driver, Windows Internet Connection Sharing (ICS), Windows Kernel-Mode Drivers, XAML Diagnostics, Windows DPAPI (Data Protection Application Programming Interface), Windows Telephony Server, Microsoft WDAC OLE DB provider for SQL, Microsoft Office Word, Windows Defender, Microsoft Power Platform Connector, Windows Local Security Authority Subsystem Service (LSASS), and Windows Cloud Files Mini Filter Driver.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
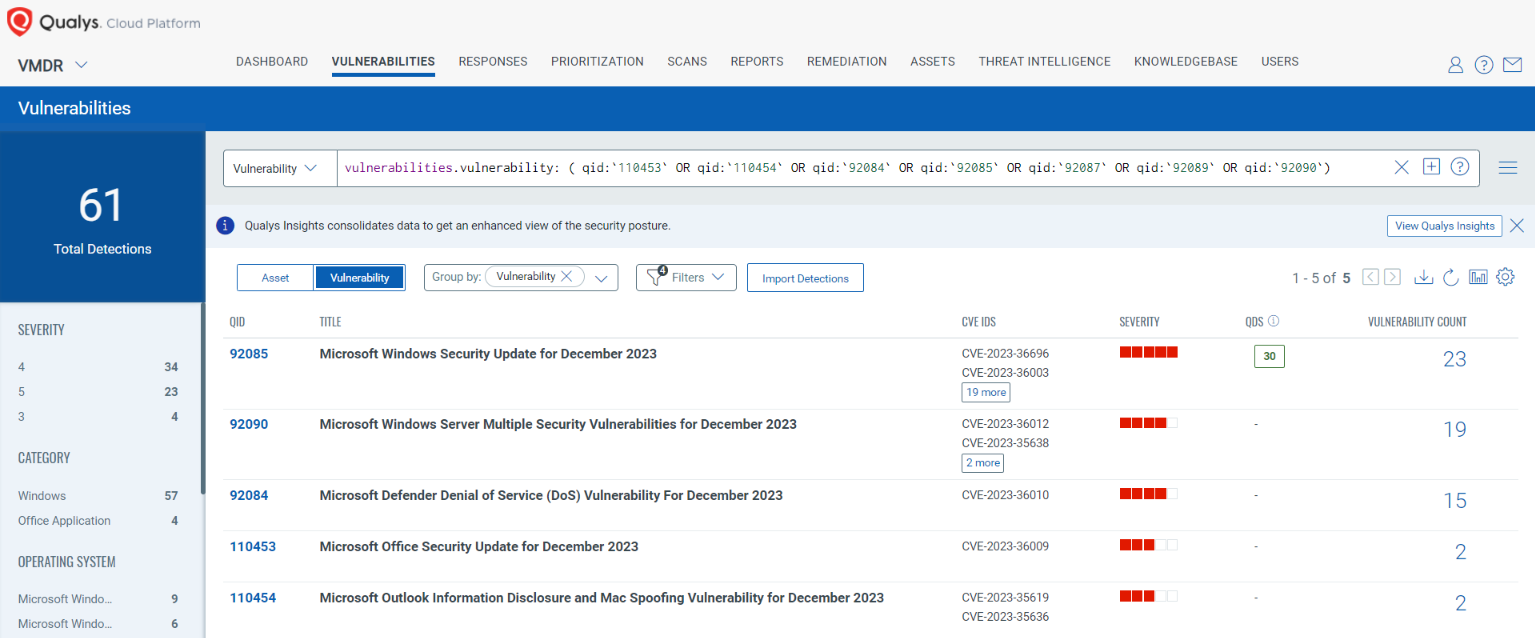
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110453` OR qid:`110454` OR qid:`92084` OR qid:`92085` OR qid:`92087` OR qid:`92089` OR qid:`92090` )
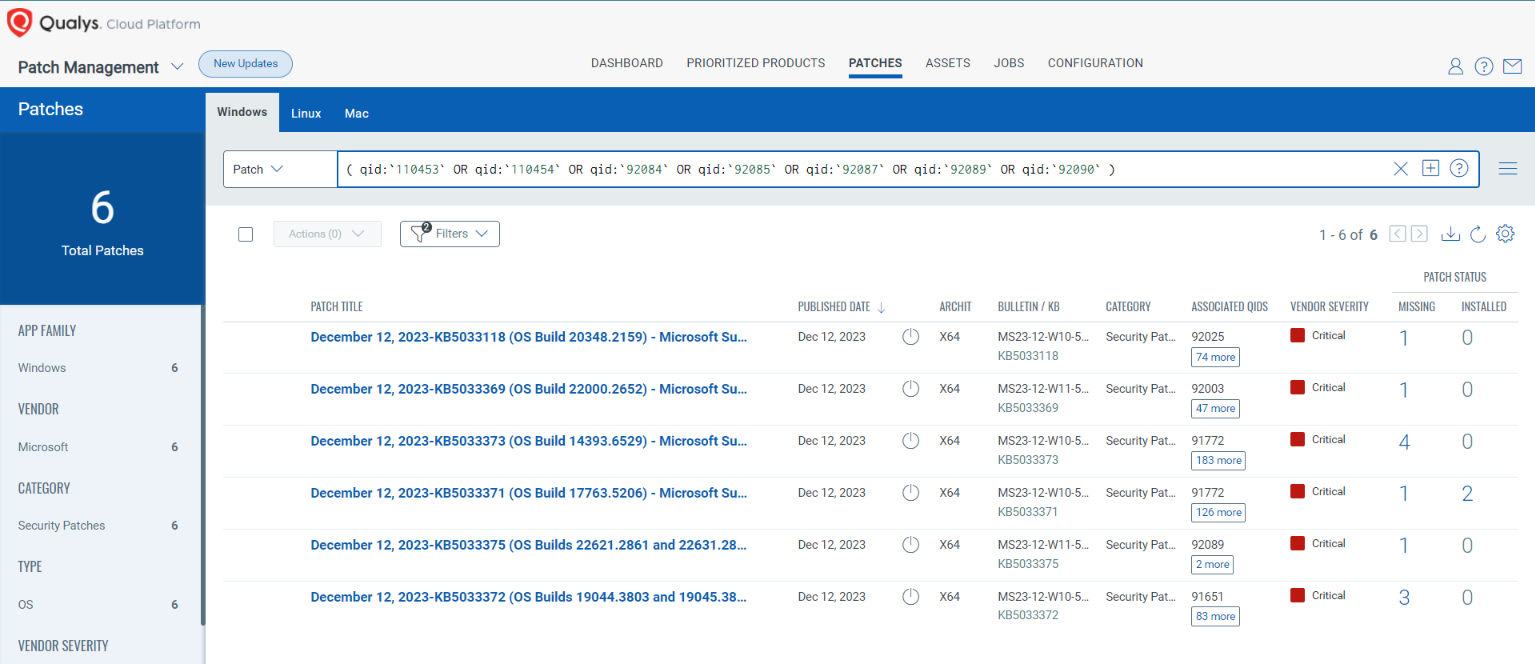
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110453` OR qid:`110454` OR qid:`92084` OR qid:`92085` OR qid:`92087` OR qid:`92089` OR qid:`92090` )
Visit the December 2023 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110453, 110454, 92084, 92085, 92087, 92089, and 92090 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/
https://msrc.microsoft.com/update-guide/releaseNote/2023-Dec
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-20588
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36019
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35630
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35641
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-35628