Academic researchers have discovered a vulnerability in SSH cryptographic network protocol that can be used in an attack called Terrapin, a prefix truncation attack. Tracked as CVE-2023-48795, the vulnerability allows attackers to lower the security of established connections by truncating the extension negotiation message.
SSH is an internet standard that offers safe access to over 15 million servers on the open internet and network services, including file transfers and remote terminal logins inside the company networks.
The Terrapin Attack
An attacker can delete any messages delivered by the client or server at the start of the secure channel without the client or server recognizing it by carefully manipulating the sequence numbers during the handshake.
An attacker may perform an attack by truncating the extension negotiation message (RFC8308) from the transcript, lowering the connection’s security. In OpenSSH 9.5, the truncation may result in using less secure client authentication algorithms and deactivating protections against keyboard timing attacks.
Terrapin can be used to enable the exploitation of implementation flaws. Security researchers of Ruhr University Bochum have discovered various flaws in the state machine of the AsyncSSH servers that let an attacker sign a victim’s client into a different account without the victim realizing it. As a result, it will strengthen the possibility of phishing attacks and might even provide the attacker access to the encrypted session via Man-in-the-Middle (MitM) techniques.
As per the researchers’ blog, “Many vendors have updated their SSH implementation to support an optional strict key exchange. Strict key exchange is a backward-incompatible change to the SSH handshake which introduces sequence number resets and takes away an attacker’s capability to inject packets during the initial, unencrypted handshake.”
It is essential to understand that for strict key exchange implementation to be effective, it requires both the client and server to support it. A vulnerable client connected to a patched server, and vice versa, still results in a vulnerable connection.
The researchers have released a scanner to detect vulnerable hosts. Users can download the scanner from the GitHub page.
The scanner checks for vulnerable hosts by detecting the algorithms ChaCha20-Poly1305 and CBC-EtM.
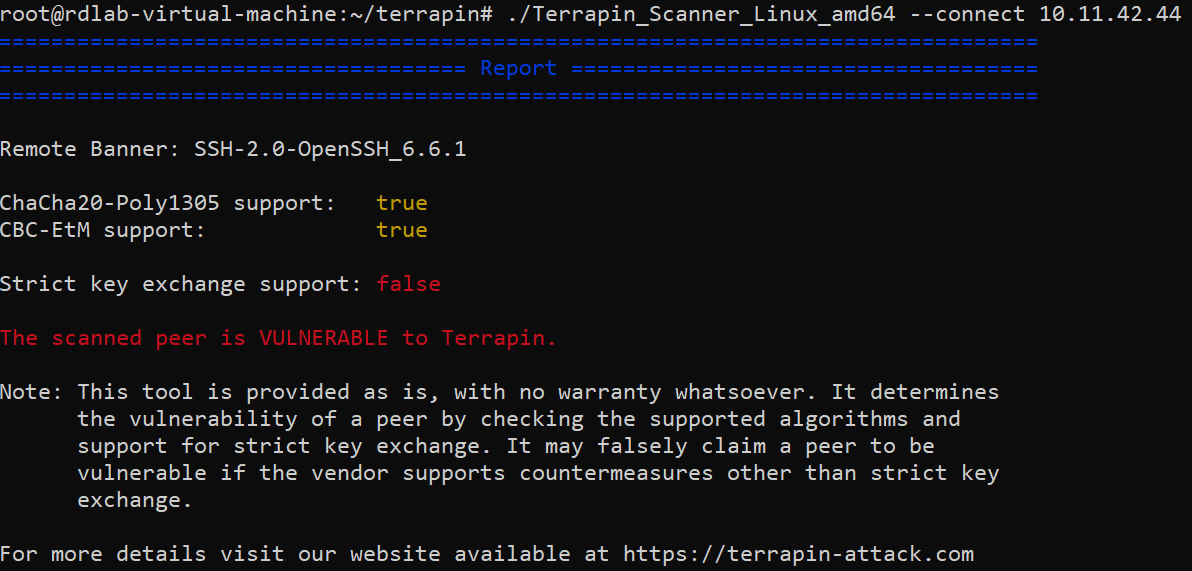
Image Source: Qualys Threat Research Unit (TRU)
Mitigation
Vendors/maintainers of affected implementations, applications, and Linux distros such as AsyncSSH, LibSSH, OpenSSH, PuTTY, Transmit, SUSE, and others have been pushing out fixes. Customers may refer to the individual vendor advisory for their operating system and install the patches.
For more information regarding the vulnerability, please refer to Terrapin Vulnerability.
Qualys Detection
Qualys customers can scan their devices with QIDs 38913, 755499, 755498, 755497, 755496, 691379, 200018, 200017, 996391, 356795, 356794, 35679, 996375, and 996349 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://terrapin-attack.com/
https://www.helpnetsecurity.com/2023/12/19/ssh-vulnerability-cve-2023-48795/