The SonicWall Threat research team has discovered an authentication bypass vulnerability in Apache OFBiz, a Java-based web framework. Tracked as CVE-2023-51467, the vulnerability has a critical severity rating with a CVSS score of 9.8. An attacker who exploits the vulnerability may bypass authentication to achieve a simple Server-Side Request Forgery (SSRF).
A security researcher at SonicWall accidentally discovered the CVE-2023-51467 while researching the root cause for the previously disclosed CVE-2023-49070. According to the researcher, the patch released for CVE-2023-49070 left the root issue, making authentication bypass possible.
Apache OFBiz is a business application suite that can be used across any industry. The Java-based framework allows developers to quickly expand or improve a typical design to provide new features.
Vulnerability Details & Exploitation Analysis
Earlier this month, Apache removed the XML RPC code from the application to patch the CVE-2023-49070. After further investigation, it was found that the vulnerability exists in the login functionality. Analysis of the LoginWorker.java file helps to understand the flow of data within the various functions and checks during the authentication process.
The researcher has developed two test cases to exploit the vulnerability.
-
Keeping the USERNAME and PASSWORD parameters empty
In the first test case, no value is given to the USERNAME and PASSWORD parameters, and the parameter requirePasswordChange=Y is included in the URI.
When the username and password are passed through the login function, it returns the value requirePasswordChange because the username and password are empty, and requirePasswordChange is set to ‘Y.’ These values are further passed through the checkLogin function. Surprisingly, the flow doesn’t enter the conditional block because the Boolean checks (username == null) and (password == null) returning false even though both the parameters are empty. Additionally, the “error”.equals(login(request, response)) also results in false due to the return value given by the login function was requirePasswordChange.
Consequently, this leads to the checkLogin function returning success, which permits the authentication bypassing.
-
Providing a known invalid USERNAME and PASSWORD parameter
In the second test case, a known invalid value is given to the USERNAME and PASSWORD parameters, and the parameter requirePasswordChange=Y is included in the URI.
In this case, the login function returns the value requirePasswordChange due to the parameter requirePasswordChange=Y. Further, the value is passed through the checkLogin function. Like the first case, the flow doesn’t enter the conditional block because the username and password are not set to null. Along with that, the “error”.equals(login(request, response)) also held false due to the return value given by the login function, which was requirePasswordChange, like test case 1.
In this case, the checkLogin function also returns success, allowing the authentication to be bypassed.
The above cases conclude that the string requirePasswordChange=Y allows authentication bypass, irrespective of the username and password or other parameters. Consequently, the bypass persisted, and eliminating the XML RPC code proved to be an ineffective patch.
The Qualys Threat Research Unit has recreated the issue and tested it on the vulnerable version successfully.
The below screenshot shows sending a request to the endpoint being redirected to the login page.
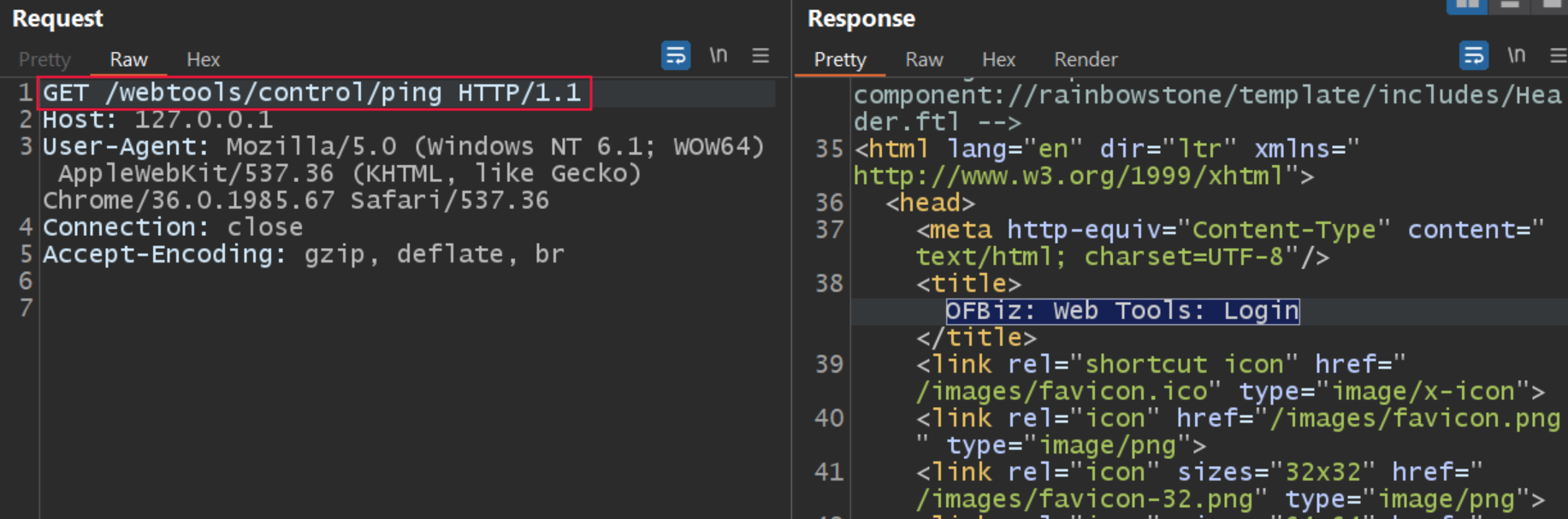
Image Source: Qualys Threat Research Unit (TRU)
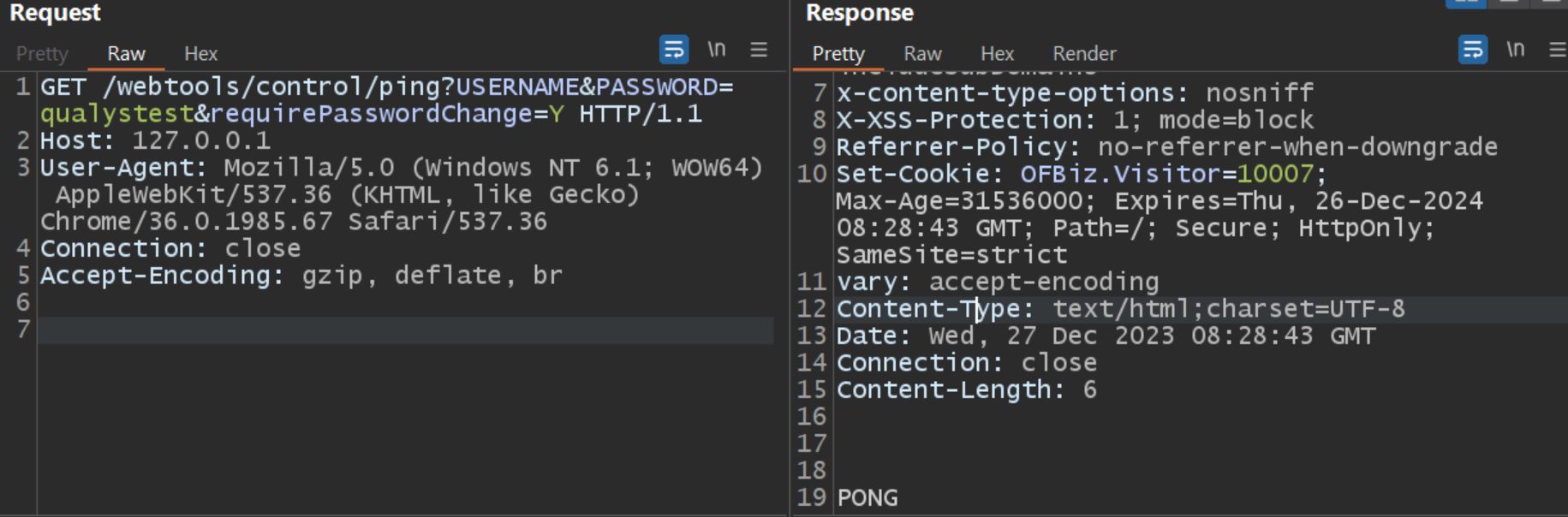
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects Apache OFBiz versions prior to 18.12.11.
Mitigation
Customers are advised to upgrade to Apache OFBiz 18.12.11 to patch the vulnerability. For more information, please refer to the Apache Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 731049 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://lists.apache.org/thread/9tmf9qyyhgh6m052rhz7lg9vxn390bdv
https://blog.sonicwall.com/en-us/2023/12/sonicwall-discovers-critical-apache-ofbiz-zero-day-authbiz/