The security research team at Veloxity identified an active exploitation of two vulnerabilities (CVE-2023-46805 & CVE-2024-21887) impacting Ivanti Connect Secure VPN devices. When chained together, the vulnerabilities may allow attackers to transmit malicious requests and execute arbitrary commands on a targeted system. According to the research, a Chinese nation-state-level threat actor has exploited the vulnerabilities.
Ivanti has mentioned in the advisory that they are aware that the vulnerabilities impact less than ten customers. The evidence suggests threat actors attempted to manipulate Ivanti’s internal integrity checker (ICT). In response, Ivanti recommended that all customers run the external ICT.
As per Shodan, over 15,000 Connect Secure (ICS) and Policy Secure gateways are currently exposed to the internet.
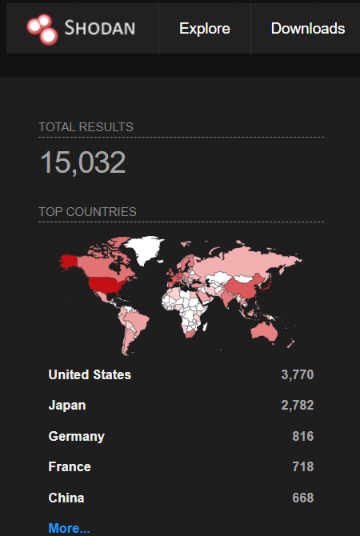
Image Source: Shodan
Acknowledging the active exploitation of the vulnerability, CISA has added them to the Known Exploited Vulnerabilities Catalog. CISA has recommended that users patch the flaw before January 31, 2024.
Ivanti Connect Secure is a VPN solution that provides secure and controlled access to corporate data and applications for employees, partners, and customers. It allows remote and mobile users to access corporate resources from any web-enabled device.
Ivanti Policy Secure (IPS) is a network access control (NAC) solution providing access to authorized and secured users and devices. It’s a central policy management server that validates the user’s identity and determines the endpoint’s security compliance.
Vulnerability Details
CVE-2023-46805 is an authentication bypass vulnerability in the web component of Ivanti ICS 9.x, 22.x, and Ivanti Policy Secure. A remote attacker may exploit the vulnerability to access restricted resources after bypassing control checks.
CVE-2024-21887 is a command injection vulnerability in the web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure. An attacker must be authenticated as an administrator to exploit the vulnerability. Successful exploitation of the vulnerability may allow an authenticated administrator to send specially crafted requests and execute arbitrary commands on the appliance.
When both vulnerabilities are combined, exploitation does not require authentication and enables a threat actor to craft malicious requests and execute arbitrary commands on the system.
Affected versions
The vulnerability affects Ivanti Connect Secure (ICS) versions 9.x and 22.x.
Mitigation
Ivanti has mentioned in the advisory that they will release patches on a staggered schedule. The first version is targeted to be available for customers the week of January 22, and the last version will be available in the week of February 19.
CVE-2023-46805 & CVE-2024-21887 can be mitigated by importing the mitigation.release.20240107.1.xml file via the download portal as a workaround.
For more information, please refer to Ivanti Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 731074 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US
https://forums.ivanti.com/s/article/CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US