Juniper Network Operating System SRX Series and EX Series are vulnerable to an Out-of-bounds Write vulnerability. Tracked as CVE-2024-21591, the vulnerability has a critical severity rating and a CVSS score of 9.8. Successful exploitation of the vulnerability may allow an attacker to create a Denial-of-Service condition. The vulnerability arises due to an insecure function that may allow an attacker to overwrite arbitrary memory. In some cases, the successful exploitation may result in remote code execution and an attacker obtaining root privileges on the device.
Junos OS offers streamlined and fine-tuning network operations to increase operational efficiency and critical time and resources for top-line growth. Many of the most advanced network deployments in the world are powered by Junos OS, which is renowned for its dependability, security, and adaptability.
Juniper has mentioned in the advisory that they have no evidence of a malicious attempt to exploit this vulnerability.
As per Shodan, over 9,000 Juniper devices have their J-Web interfaces exposed to the internet.
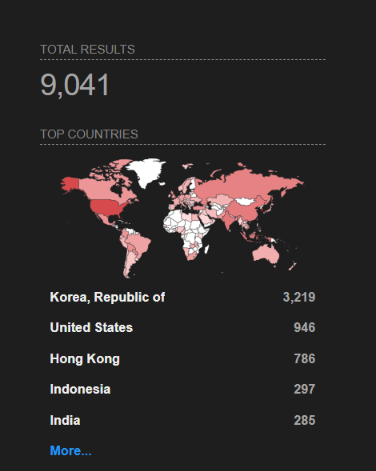
Image Source: Shodan
Prerequisite
The following minimal configuration must be present on the device:
[system services web-management http]
or
[system services web-management https]
Affected Versions
This vulnerability affects Juniper Networks Junos OS SRX Series and EX Series:
- Junos OS versions earlier than 20.4R3-S9
- Junos OS 21.2 versions earlier than 21.2R3-S7
- Junos OS 21.3 versions earlier than 21.3R3-S5
- Junos OS 21.4 versions earlier than 21.4R3-S5
- Junos OS 22.1 versions earlier than 22.1R3-S4
- Junos OS 22.2 versions earlier than 22.2R3-S3
- Junos OS 22.3 versions earlier than 22.3R3-S2
- Junos OS 22.4 versions earlier than 22.4R2-S2, 22.4R3
Mitigation
GitLab has released Junos OS 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S5, 22.1R3-S4, 22.2R3-S3, 22.3R3-S2, 22.4R2-S2, 22.4R3, 23.2R1-S1, 23.2R2, 23.4R1 versions to patch the vulnerability.
For more information, please visit the Juniper Security Advisory.
Workaround
Disable J-Web or limit access to only trusted hosts.
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now.
Qualys Policy Compliance team releases these controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been published to support the evaluation of recommended mitigations:
- 8580 Status of the ‘HTTP Access JWEB Service’ setting
- 8581 Status of the ‘HTTPS Access JWEB Service’ setting
Qualys Detection
Qualys customers can scan their devices with QID 44147 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.