CVE-2023-6548 and CVE-2023-6549 are the two vulnerabilities impacting Citrix NetScaler ADC and NetScaler Gateway. On successful exploitation, the vulnerabilities may result in remote code execution and denial of service. Citrix has mentioned in the advisory that they have observed the exploitation attempts on vulnerable appliances.
Citrix stated in the advisory, “This bulletin only applies to customer-managed NetScaler ADC and NetScaler Gateway products. Customers using Citrix-managed cloud services or Citrix-managed Adaptive Authentication do not need to take any action.”
CISA has added the vulnerabilities to its Known Exploited Vulnerabilities Catalog and requested users to patch it before January 24, 2024 (CVE-2023-6548) and February 2, 2024 (CVE-2023-6549).
Citrix ADC is an application delivery solution for both on-premises and the cloud. Application delivery controllers (ADCs) are networking devices explicitly designed to enhance the performance, security, and resilience of the delivery of applications.
Citrix Gateway unifies remote access infrastructure to offer single sign-on for all applications, whether hosted in a data center, the cloud, or provided as SaaS.
As per Shodan, over 86,000 NetScaler Gateway management interfaces are exposed to the internet.
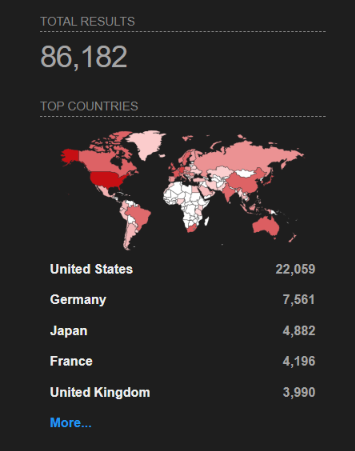
Image Source: Shodan
CVE-2023-6548: Authenticated Remote Code Execution Vulnerability
An attacker must have access to NSIP, CLIP, or SNIP with management interface access to exploit the vulnerability. On successful exploitation, an attacker may perform remote code execution on target systems.
It is essential to know that the vulnerability only impacts the management interface. Cloud Software Group strongly recommends separating the network traffic to the appliance’s management interface from regular network traffic, either physically or logically. Along with that, Citrix also recommends that users not expose the management interface to the internet.
CVE-2023-6549: Denial of Service Vulnerability
The prerequisites for the successful exploitation of the vulnerability are:
- The appliance must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy)
OR
- AAA virtual server
Successful exploration of the vulnerability may allow an attacker to perform a denial-of-service attack on vulnerable targets.
Affected Versions
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-12.35
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-51.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.21
- NetScaler ADC 13.1-FIPS before 13.1-37.176
- NetScaler ADC 12.1-FIPS before 12.1-55.302
- NetScaler ADC 12.1-NDcPP before 12.1-55.302
Note: NetScaler ADC and NetScaler Gateway version 12.1 is now End-of-Life (EOL) and is vulnerable.
Mitigation
Customers are advised to upgrade to the following versions to mitigate the vulnerabilities:
- NetScaler ADC and NetScaler Gateway 14.1-12.35 and later releases
- NetScaler ADC and NetScaler Gateway 13.1-51.15 and later releases of 13.1
- NetScaler ADC and NetScaler Gateway 13.0-92.21 and later releases of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.176 and later releases of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.302 and later releases of 12.1-FIPS
- NetScaler ADC 12.1-NDcPP 12.1-55.302 and later releases of 12.1-NDcP
Note: NetScaler ADC and NetScaler Gateway version 12.1 is now End-of-life (EOL). Customers are recommended to upgrade their appliances to one supported version that addresses the vulnerabilities.
Please refer to the Citrix Security Bulletin (CTX584986) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 379265 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.