Security researchers at Spark Engineering Consultants have discovered an authentication bypass vulnerability in GoAnywhere Managed File Transfer. Tracked as CVE-2024-0204, the vulnerability has a critical severity and a CVSS score of 9.8. The vulnerability allows an unauthorized user to create an admin user via the administration portal.
GoAnywhere MFT is a secure managed file transfer solution that provides smooth data sharing between systems, employees, clients, and business partners. It helps process information from files into XML, EDI, CSV, and JSON databases and offers centralized control with a wide range of security settings and complete audit trails. Deployable on-premises, cloud, and hybrid environments, GoAnywhere MFT encrypts data following industry standard protocols, for example, HTPPS, OpenPGP, and STFP.
Exploitation Analysis
The analysis of the Application directories shows that the /InitialAccountSetup.xhtml endpoint is mapped to the com.linoma.ga.ui.admin.users.InitialAccountSetupForm class by inspecting the file GoAnywhere/adminroot/WEB-INF/forms-faces.xml.
After installation, the vulnerable endpoint could not allow access to the same page; instead, the user will be redirected to the /Dashboard.xhtml endpoint and then to /auth/Login.xhtml because they are not authenticated.
This behavior in the application is because of the com.linoma.dpa.security.SecurityFilter class. This class is called on all requests and performs the doFilter() function. The function checks the requested endpoint and will allow the request to be routed to the correct endpoint based on the endpoints, user context, and application settings.
In the SecurityFilter class, two specific areas deal with requesting the /InitialAccountSetup.xhtml endpoint.
- When no admin user is created already, and the path is not /wizard/InitialAccountSetup.xhtml, then it will adequately route to the setup page.
- When an admin user is created already, and the path is /wizard/InitialAccountSetup.xhtml, then redirect to /Dashboard.xhtml.
The vulnerability exploitation depends upon the path traversal flaw in the Tomcat-based applications when the request contains /..;/. An attacker must request the vulnerable endpoint with a request similar to https://ip/goanywhere/images/..;/wizard/InitialAccountSetup.xhtml. The request will redirect the user to the setup page.
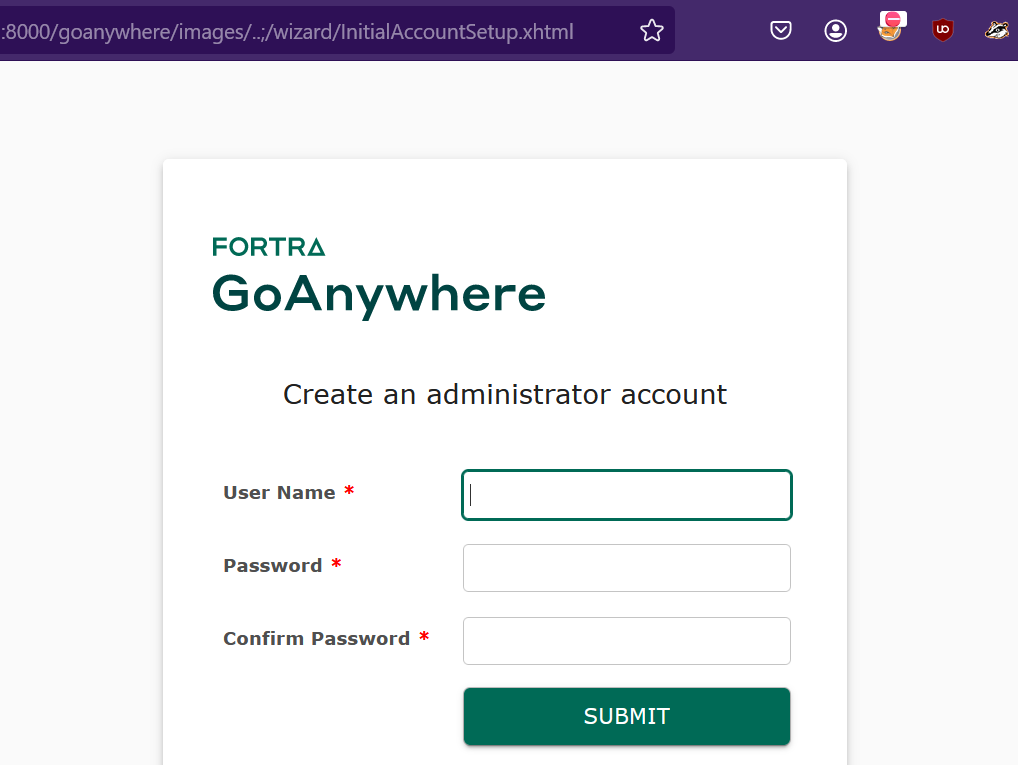
Image Source: Qualys Threat Research Unit
Submitting this form again by re-writing the form submission request to include the path traversal will create a new administrative user.
On a patched target, the same request returns a 401 error.
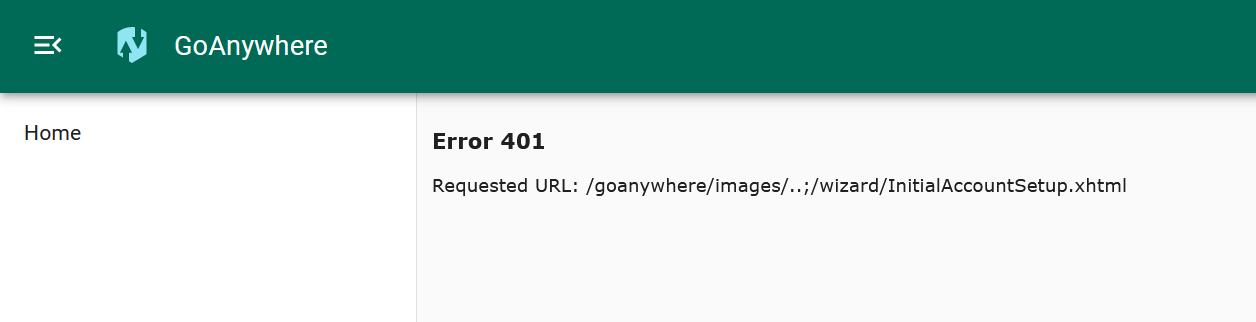
Image Source: Qualys Threat Research Unit
Indicators of Compromise
The indicators of compromises can be seen as new additions to the Admin Users group. The new addition can be checked from the GoAnywhere administrator portal Users -> Admin Users section.
Along with that, logs for the database are stored at \GoAnywhere\userdata\database\goanywhere\log\*.log. These files contain the transactional history of the database, for which adding users will create entries.
Affected Versions
- Fortra GoAnywhere MFT 6.x from 6.0.1
- Fortra GoAnywhere MFT 7.x before 7.4.1
Mitigation
Customers are advised to upgrade to GoAnywhere Managed File Transfer (MFT) 7.4.1 or later to patch the vulnerability.
For more information, please refer to Fortra Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 731096 to detect vulnerable assets. The QID checks for vulnerable version of GoAnywhere MFT by sending a GET request to the ‘goanywhere/ images/..;/wizard/InitialAccountSetup.xhtml‘ endpoint and checks if the Account Setup page is accessible.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.fortra.com/security/advisory/fi-2024-001
https://www.horizon3.ai/cve-2024-0204-fortra-goanywhere-mft-authentication-bypass-deep-dive/