Zoom addressed a vulnerability that impacts the Zoom Desktop Client for Windows, Zoom VDI Client for Windows, and Zoom Meeting SDK for Windows. Tracked as CVE-2024-24691, the vulnerability has a critical severity with a CVSS score 9.6. The vulnerability may allow an unauthenticated user to escalate privilege with the help of network access.
Zoom did not release many details about the ways of vulnerability exploitation. The CVSS vector shows an attacker can exploit the vulnerability in a low-complexity attack.
Zoom is a cloud-based platform that offers videotelephony and online chat services. It can be used for meetings, messaging, voice calls, conference rooms, virtual events, and contact centers. Zoom is available on Windows, macOS, Google Play, and the App Store.
Affected Versions
- Zoom Meeting SDK for Windows before version 5.16.5
- Zoom Rooms Client for Windows before version 5.17.0
- Zoom Desktop Client for Windows before version 5.16.5
- Zoom VDI Client for Windows before version 5.16.10 (excluding 5.14.14 and 5.15.12)
Mitigation
Customers are advised to upgrade to Zoom Client for Windows versions 5.16.5, 5.16.10, 5.17.0, and 5.16.5 to patch the vulnerability.
The latest versions are available at https://zoom.us/download.
Please refer to the Zoom Security Advisory (ZSB-24008) for more information.
Qualys Detection
Qualys customers can scan their devices with QID 379376 to detect vulnerable assets.
Once the QID is detected from VMDR, users can remediate or mitigate the vulnerability as per their need.
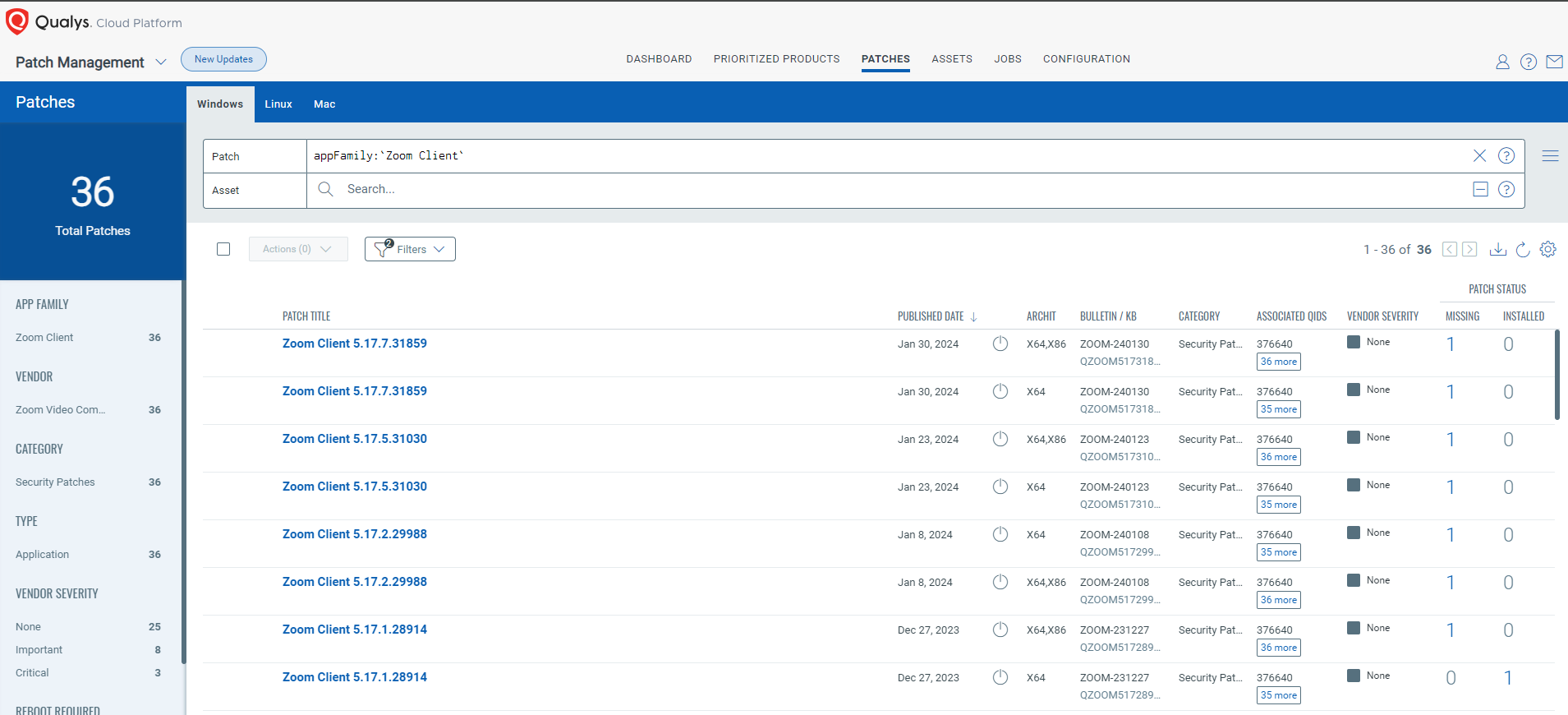
EXECUTE Remediation Using Patch Management (PM)
Users can update the Zoom app and remediate the vulnerability.
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
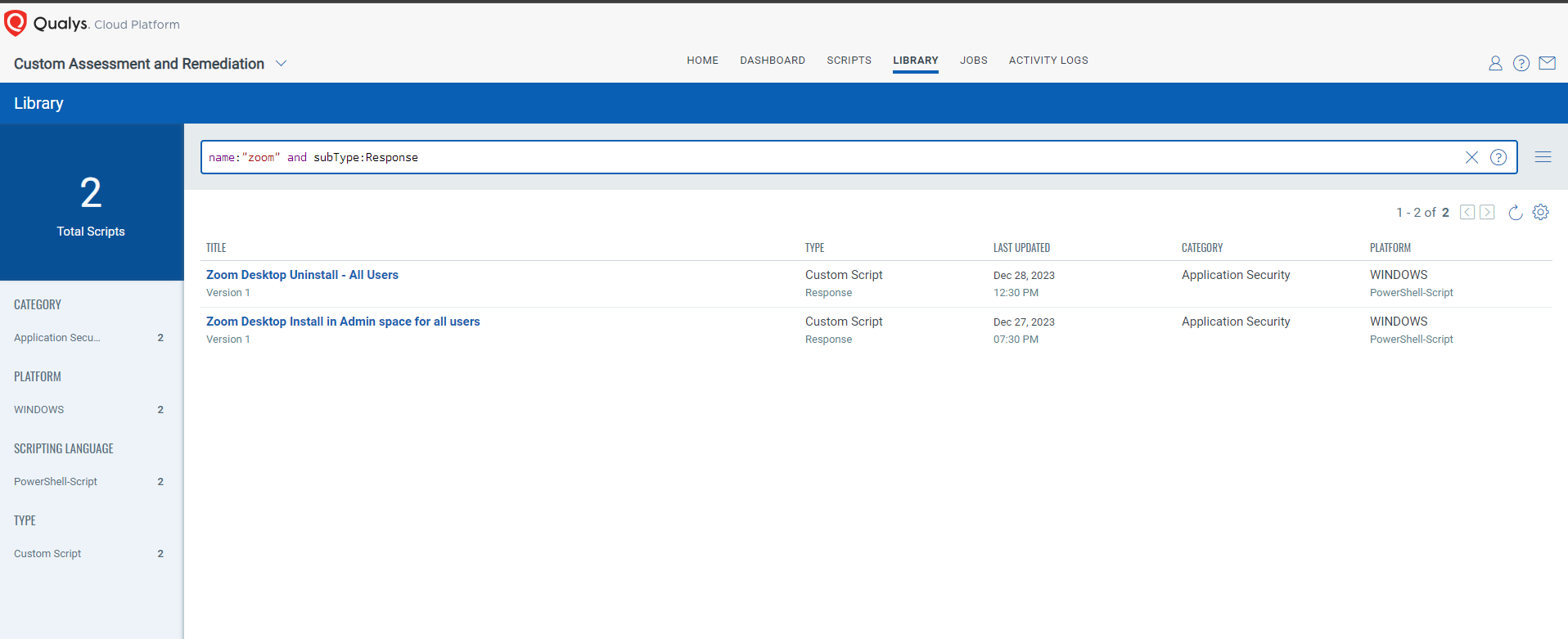
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.zoom.com/en/trust/security-bulletin/ZSB-24008/