Microsoft has released its May edition of Patch Tuesday. Let’s take a deep dive into the crucial insights from Microsoft’s Patch Tuesday updates for May 2024.
Microsoft Patch Tuesday’s May 2024 edition addressed 67 vulnerabilities, including one critical and 59 important severity vulnerabilities. In this month’s security updates, Microsoft has addressed two zero-day vulnerabilities known to be exploited in the wild. Microsoft also addressed five vulnerabilities in Microsoft Edge (Chromium-based). The vulnerabilities have been patched earlier this month.
Microsoft Patch Tuesday, May edition includes updates for vulnerabilities in Microsoft Office and Components, Power BI, Visual Studio, Windows Cloud Files Mini Filter Driver, Windows Common Log File System Driver, Windows Cryptographic Services, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing. The May 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 4 | Important: 4 |
| Denial of Service Vulnerability | 3 | Important: 3 |
| Elevation of Privilege Vulnerability | 17 | Important: 17 |
| Information Disclosure Vulnerability | 7 | Important: 7 |
| Remote Code Execution Vulnerability | 27 | Critical: 1 Important: 26 |
| Security Feature Bypass Vulnerability | 2 | Important: 1 |
Zero-day Vulnerabilities Patched in May Patch Tuesday Edition
CVE-2024-30040: Windows MSHTML Platform Security Feature Bypass Vulnerability
Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still relevant today and are being patched by Microsoft.
The vulnerability can bypass OLE mitigations in Microsoft 365 and Microsoft Office, which protect users from vulnerable COM/OLE controls. An unauthenticated attacker may exploit this vulnerability to execute code by convincing a user to open a malicious document.
CISA has added this CVE to its Known Exploited Vulnerabilities Catalog and requested users to patch it before May 6, 2024.
CVE-2024-30051: Windows DWM Core Library Elevation of Privilege Vulnerability
The Microsoft Windows Desktop Window Manager (DWM) Core Library is a system manager that generates every visible element on a PC or laptop, including visual effects in menus, wallpapers, themes, and more. It has been a part of Microsoft Windows since Windows Vista and is also known as the Desktop Compositing Engine (DCE).
On successful exploitation, an attacker could gain SYSTEM privileges.
CISA has added this CVE to its Known Exploited Vulnerabilities Catalog and requested users to patch it before May 6, 2024.
Critical Severity Vulnerability Patched in May Patch Tuesday Edition
CVE-2024-30044: Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft SharePoint is a web-based platform that allows organizations to create websites for storing, organizing, sharing, and accessing information. SharePoint is available in Microsoft 365 and can be used on PCs, Macs, and mobile devices.
An authenticated attacker with Site Owner permissions or higher could upload a specially crafted file to the targeted SharePoint Server and craft specialized API requests to trigger the deserialization of the file’s parameters. Successful exploitation of the vulnerability may allow an attacker to perform remote code execution in the context of the SharePoint Server.
Other Microsoft Vulnerability Highlights
- CVE-2024-29996 and CVE-2024-30025 are elevation of privilege vulnerabilities in the Windows Common Log File System Driver. On successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2024-30050 is a security feature bypass vulnerability in Windows Mark of the Web. An attacker might host a file on a server and convince a targeted user to download and open the file to exploit this vulnerability. An attacker may alter the functionality of the Mark of the Web on successful exploitation.
- CVE-2024-30032 is an elevation of privilege vulnerability in Windows DWM Core Library. On successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2024-30034 and CVE-2024-30035 are information disclosure vulnerabilities in the Windows Cloud Files Mini Filter Driver. On successful exploitation, an attacker may disclose certain kernel memory content.
- CVE-2024-30038 is an elevation of privilege vulnerability in Win32k. Successful exploitation of the vulnerability may allow a local, authenticated attacker to gain elevated local system or administrator privileges.
- CVE-2024-30049 is an elevation of privilege vulnerability in the Windows Win32 Kernel Subsystem. On successful exploitation, an attacker could gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Task Scheduler, Microsoft Windows SCSI Class System File, Windows Mobile Broadband, Microsoft WDAC OLE DB provider for SQL, Microsoft Brokering File System, Windows DWM Core Library, Windows Routing and Remote Access Service (RRAS), Windows Hyper-V, Windows Kernel, Windows DHCP Server, Windows NTFS, Windows Win32K – ICOMP, Windows Win32K – GRFX, Windows CNG Key Isolation Service, Microsoft Windows Search Component, Windows Deployment Services, Windows Remote Access Connection Manager, Windows MSHTML Platform, Microsoft Bing, Microsoft Office Excel, Microsoft Office SharePoint, .NET and Visual Studio, Microsoft Dynamics 365 Customer Insights, Windows Mark of the Web (MOTW), Azure Migrate, Power BI, Microsoft Edge (Chromium-based), and Microsoft Intune.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
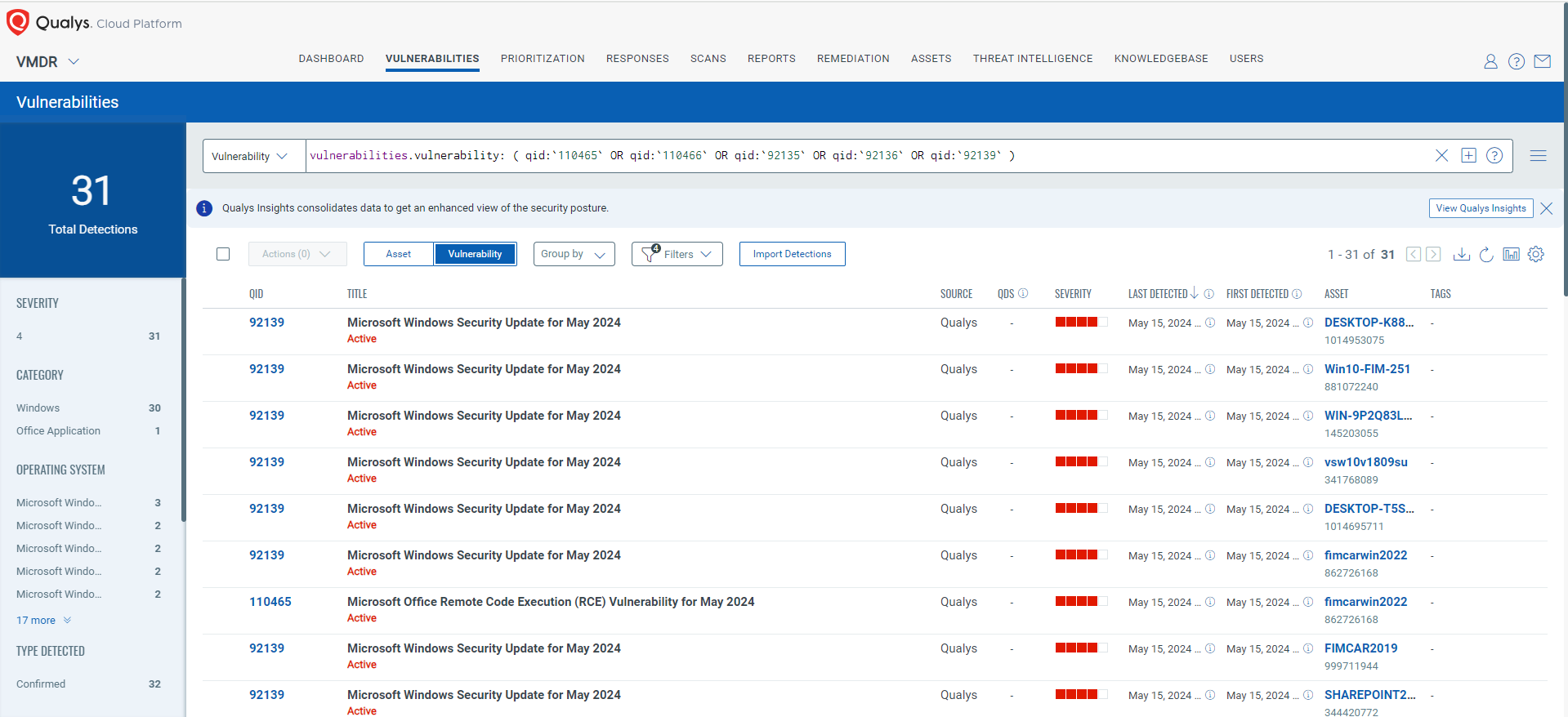
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110465` OR qid:`110466` OR qid:`92135` OR qid:`92136` OR qid:`92139` )
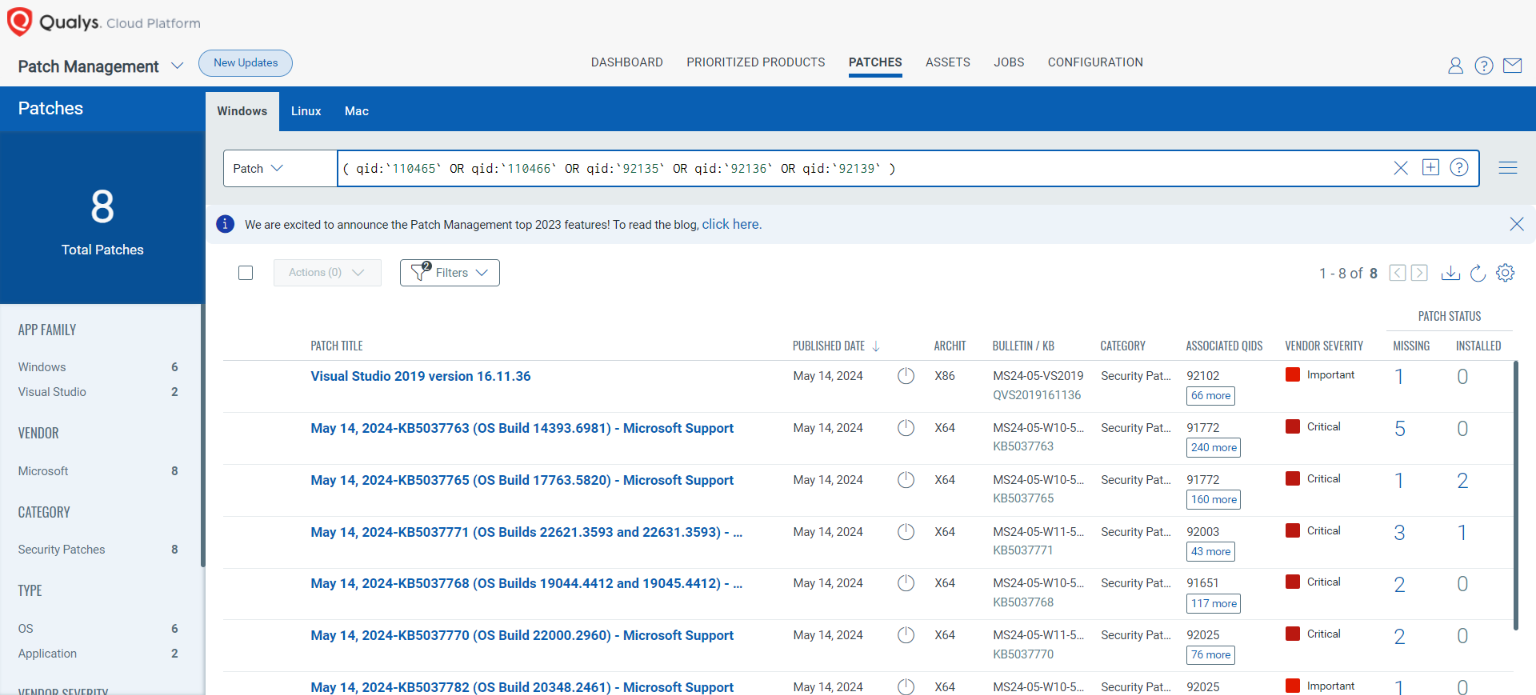
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110465` OR qid:`110466` OR qid:`92135` OR qid:`92136` OR qid:`92139` )
Visit the May 2024 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110465, 110466, 92135, 92136, and 92139 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/
https://msrc.microsoft.com/update-guide/releaseNote/2024-May
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-30040
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-30051
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-30044