The Zabbix server is vulnerable to an SQL injection vulnerability, tracked as CVE-2024-22120. The vulnerability has been given a critical severity rating with a CVSS score of 9.1. Successful exploitation of the vulnerability may allow a remote authenticated attacker to execute arbitrary SQL queries, allowing the threat actors to dump the database, escalate privileges to admin, and perform remote code execution.
Zabbix is an open-source monitoring tool that collects, stores, manages, and analyzes information from IT infrastructure. Zabbix can monitor various IT components, including networks, servers, virtual machines (VMs), and cloud services. Zabbix also offers reporting and data visualization features that can be accessed through a web-based frontend.
As per Shodan, over 22,000 Zabbix Servers are exposed to the internet.
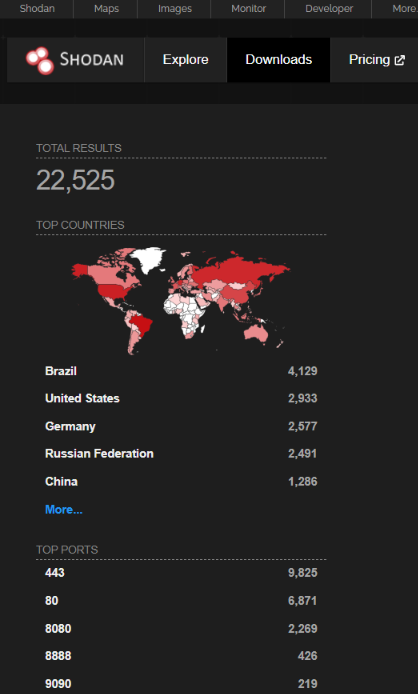
Image Source: Shodan
Vulnerability Details
The vulnerability exists in the command execution feature of the Zabbix server that is used for configured scripts. After executing the command, an audit entry is added to the Audit Log. Due to the unsanitized clientip field, it is possible to inject SQL commands into the clientip field and exploit time-based blind SQL injection.
The advisory describes the steps in which vulnerability can be exploited.
- The attacker needs to log in as a low-privilege user. To execute a command against a host, the attacker must have access to at least one of the hosts.
- Extract the logged-in user sessionid from the zbx_session cookie.
- Extract any hostid available to this user.
Affected Versions
- 6.0.0 – 6.0.27
- 6.4.0 – 6.4.12
- 7.0.0alpha1 – 7.0.0beta1
Mitigation
To patch the vulnerabilities, customers must upgrade to the following versions:
- 6.0.28rc1
- 6.4.13rc1
- 7.0.0beta2
For more information, please refer to the Zabbix Security Advisory (ZBX-24505).
Qualys Detection
Qualys customers can scan their devices with QID 731539 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://support.zabbix.com/browse/ZBX-24505
https://github.com/W01fh4cker/CVE-2024-22120-RCE