Microsoft released patches for an actively exploited vulnerability impacting SharePoint Server. Tracked as CVE-2025-53770, the vulnerability was part of an “active, large-scale” exploitation campaign. Successful exploitation of the vulnerability may allow a remote unauthenticated attacker to execute arbitrary code, leading to critical data loss and possible system compromise. Viettel Cyber Security with Trend Zero Day Initiative discovered and reported the vulnerability to Microsoft.
Microsoft mentioned in the advisory that they are “aware of active attacks targeting on-premises SharePoint Server customers by exploiting vulnerabilities partially addressed by the July Security Update.”
A quick search revealed over 200,000 targets on Fofa at the time of writing.
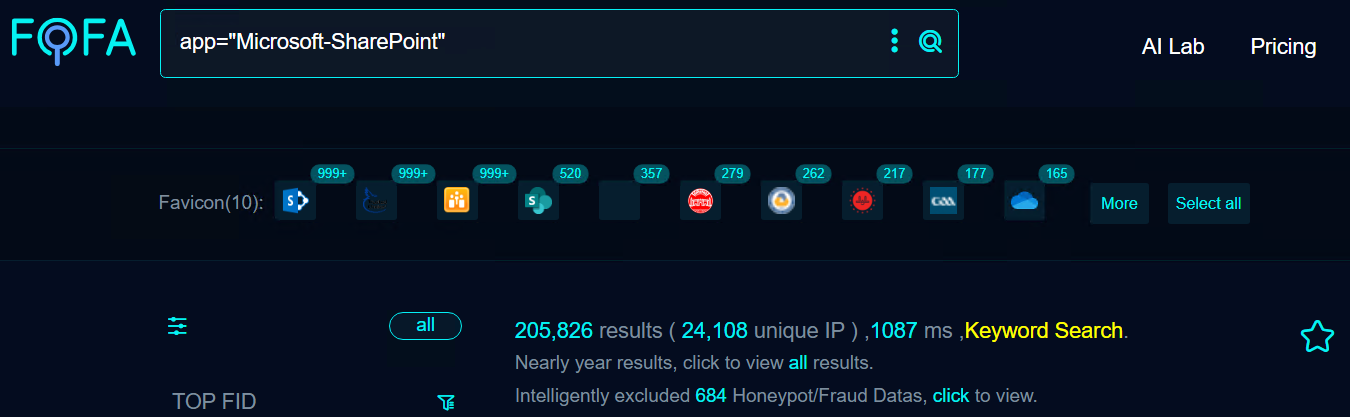
Many organizations use the SharePoint server, which makes the vulnerability even more severe. CISA has also added the vulnerability to its Known Exploited Vulnerabilities Catalog, urging users to patch before July 21, 2025.
Vulnerability Details
The zero-day vulnerability (CVE-2025-53770) bypasses CVE-2025-49704, a code injection and remote code execution flaw in Microsoft SharePoint Server. Microsoft addressed the flaw as part of its July 2025 Patch Tuesday updates.
How the Attack Works
Eye Security’s security researcher described the vulnerability’s exploitation in their blog. The chain combines two vulnerabilities, CVE‑2025‑49704 and CVE‑2025‑49706, called “ToolShell.” An attacker can send a particular POST request to /_layouts/15/ToolPane.aspx using a spoofed Referer: /_layouts/SignOut.aspx to bypass authentication.
Subsequent research revealed that on July 17, 2025, a security researcher had fuzzed this specific Referer value. The only remaining clue was a decompiled .NET assembly named Microsoft.PerformancePoint.Scorecards.Client.dll. Based on this, the crafted Referer header may have unintentionally transformed CVE-2025-49706 into an active zero-day vulnerability, later officially tracked by Microsoft as CVE-2025-53770.
Impact Analysis
- First and foremost, the flaw does not require any authentication for its exploitation. The exploit chain allows direct remote code execution on vulnerable instances.
- Attackers can impersonate services even after remediation.
- The injected code remains effective across reboot and updates.
- SharePoint’s integration with services like Outlook, Teams, and OneDrive broadens the impact beyond the initial breach.
CVE-2025-53771
Microsoft also addressed a spoofing vulnerability in the Microsoft SharePoint server tracker, CVE-2025-53771. The path traversal vulnerability in Microsoft Office SharePoint allows an authenticated attacker to perform spoofing over a network.
Qualys Threat Intelligence provided a Qualys Vulnerability Score (QVS) of 100 for the vulnerability. Qualys Vulnerability Score (QVS) is a Qualys-assigned score for a vulnerability based on multiple factors associated with the CVE, such as CVSS and external threat indicators like active exploitation, exploit code maturity, CISA known exploitable, and many more.
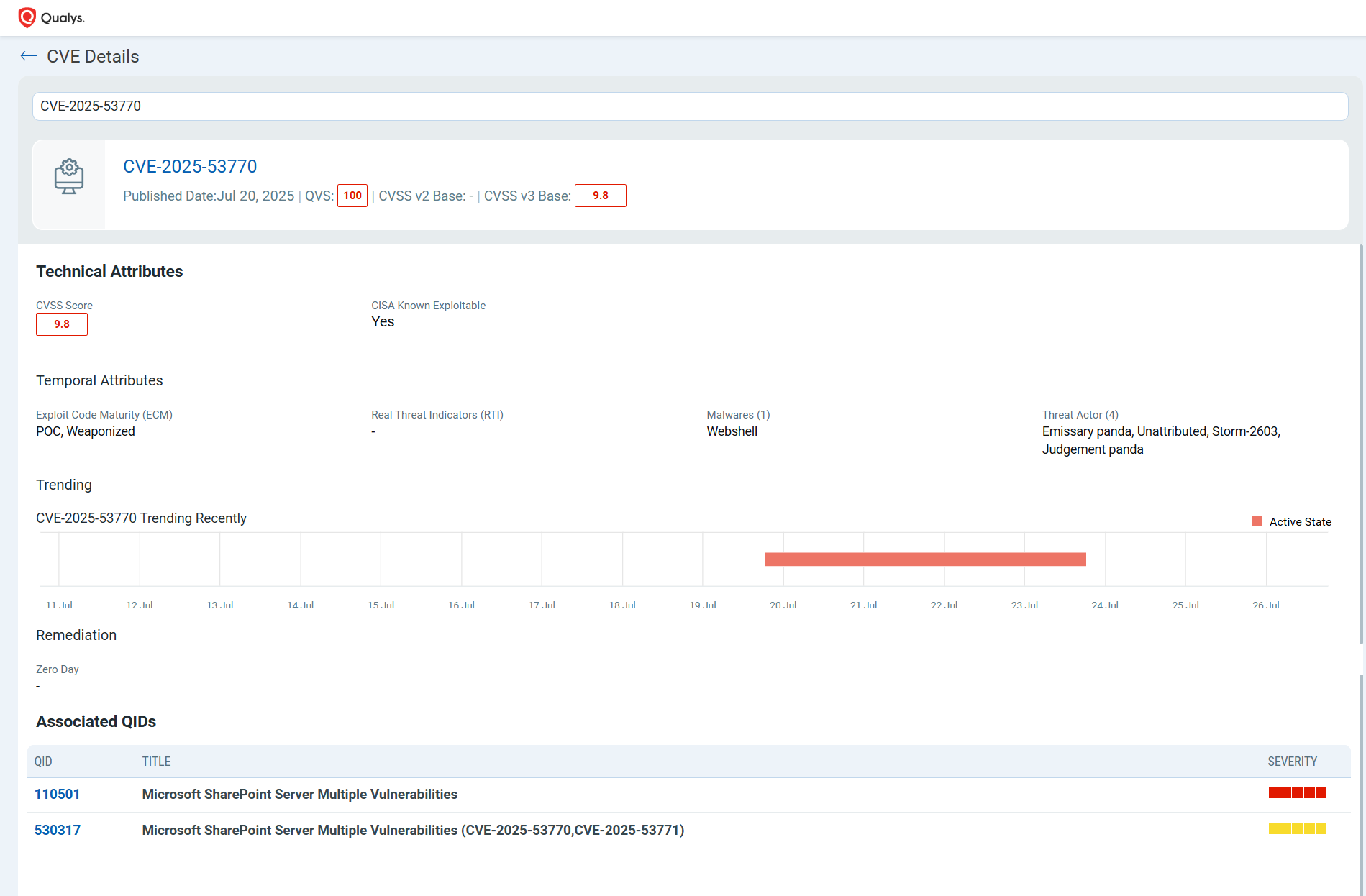
Qualys Threat Intel also revealed that the vulnerability is used in a malware campaign Webshell.
Affected Versions
- SharePoint 2016 (on-prem)
- SharePoint 2019 (on-prem)
- SharePoint Subscription Edition
Mitigation
As per the advisory, “the update for CVE-2025-53770 includes more robust protections than for CVE-2025-49704. The update for CVE-2025-53771 includes more robust protections than the update for CVE-2025-49706.”
Users must upgrade to the following versions to patch the vulnerability:
- SharePoint Subscription Edition build number 16.0.18526.20508
- SharePoint 2019 build number 16.0.10417.20037
Update:
Microsoft released a patch for SharePoint 2016. Users must upgrade to SharePoint 2016 build number 16.0.5513.1001 and 16.0.5513.1001.
For more information, please refer to the Microsoft Security Advisories for CVE-2025-53770 and CVE-2025-53771.
Qualys Detection
Qualys customers can scan their devices with QIDs 110501, 732800, and 530317 to detect vulnerable assets.
Continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://research.eye.security/sharepoint-under-siege/
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53770
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53771
https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/
After following MS patching process for the vulnerability, Qualys scans are still showing our SP servers with the vulnerability.
What other steps are available other than the recommended MS patching steps to allow for a clear Qualys scan of the SP servers?